Wednesday, July 19, 2023
Blog topics:
 PERSPECTIVES FROM THE CAMPUS
PERSPECTIVES FROM THE CAMPUS
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name "Perspectives From the Campus Series”, we invite experts -- immersed in the pursuit of educating their students -- to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the first installment of this series, David Dungan, who serves as the Executive Director at the Center for Security Services and Cyber Defense at Anderson University, shares his perspective on why cybersecurity is an essential tool for local business owners.
By David Dungan
The world is digital. Present-day business infrastructures depend on technology that provides simplicity but may be easily exploited. Small businesses are subject to cyberattacks, usually due to deficits in their security infrastructure.
The Cybersecurity & Infrastructure Security Agency (CISA) stresses that small businesses have valuable information, such as health, financial, and personally identifiable information on employees and financial data of customers. Small businesses are usually more vulnerable and at higher risk of cyberattacks compared to larger firms due to fewer resources for cybersecurity than larger businesses.
Small businesses should upgrade their security infrastructure to decrease the odds of a successful cyberattack.
Cyberattacks are usually viewed as external threats, but this may not always be the case. Most cyber-related incidents actually occur within the company itself, whether it was done on purpose or on accident. International Business Machines (IBM)classifies these threat actors into four different categories:
- The Pawn is an innocent employee, unaware of the implications of their digital actions. Essentially, this employee could be easily duped by outside threats. If they were to receive an inauthentic email from their district manager, asking for personally identifiable information, this employee will mistakenly send the requesting entity the information asked of them.
- The Goof is an employee that does not properly follow company security protocols. This individual may enter restricted parts of the company, or they may take their work home, risking the exposure of business information to outsiders.
- The Collaborator is the “undercover employee.” This employee has ulterior motives, which mainly involve working with other organizations that may be competitors.
- The Lone Wolf is the employee who works alone against the company, perhaps for financial gain or malicious intent. The situation becomes worse if this person has an elevated privilege level and access.
Common Cyber Threats to the Workplace
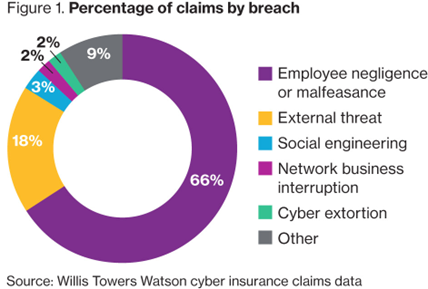 (World Economic Forum, 2017)
(World Economic Forum, 2017)
How Can Local Businesses Start Preparing?
There are a variety of ways an organization can start improving its security infrastructure, including:
- Employ qualified cybersecurity professionals
- Utilize identification cards
- Install/Upgrade security cameras if they are more than five years old
- Assess the cyber awareness of employees on a regular basis
- Update staff on any new hires
- Define company limitations and designate no-access/restricted zones
There is always more an organization can do to improve its security capabilities. It is great to have security procedures in place, but those protocols must be continuously revised and updated to ensure a secure working environment.
There is no way to guarantee against a cyberattack, but businesses can upgrade their security posture, making it more difficult for attackers to access and breach their assets.

