At a time when cyber breaches are happening frequently to many organizations, it can be helpful use the information that is available from trusted sources, such as CISA, to stay better protected.
Source: 2023 Verizon Data Breach Investigation Report
A Security Incident Could Be in Your Future
More Than a Phase: Incident Response Plans Involves Five Critical Steps
Phase One - Plan, Prepare and Be Ready
- Know Your Organization and Who You’re Accountable To
- Local government
- Small business
- Nonprofit
- Know your apps, systems, data, components, and secure them
- Identify and codify who will help in an incident before it happens
- Author and announce incident response policies
- Write and exercise incident response plans
- Determine who you must communicate with
- Train people on what to report, to whom, and how
Phase Two - Identify and Report
- Teammates are trained to inform you of breach indications.
- Report analyzed incidents and events to those who can help.
- Inform your regulators according to their requirements.
Phase Three - Assess and Analyze
Determine
- What happened and when did it occur.
- Source and targets of attack.
- Data, applications, systems, and components that may have been compromised.
- Whether the attack is continuing.
- What must be done to defend, recover, and reconstitute.
Phase Four - Update and Recommend
Inform the following groups of the information from the Assess and Analyze slide, as necessary.
- Organizational leadership.
- Customers—what happened, impact to them, and actions they should take.
- Regulators
Phase Five - Defend, Recover and Reconstitute
Contact internal, contracted, state, and federal incident response partners to help.
- Fail over to disaster recovery sites if possible.
- Defend against and stop continuing attacks.
- Develop and execute recovery and reconstitution plans.
- Formulate communications with employees, customers, and others.
- Collaborate with federal agencies on investigations, if necessary.
In the Event…
- Cyber incidents and cyberattacks never happens the way you planned for it.
- Be sure to use your incident response plan and lessons learned from exercises.
- Be flexible!
Guidance for Local Government:
1. Data Protection and Privacy Laws: Local governments must comply with relevant data protection and privacy laws specific to their jurisdiction. These laws may impose obligations on government entities to protect sensitive data, implement security measures, and notify individuals in the event of a data breach.
2. Breach Notification Requirements: Depending on the jurisdiction, local governments may be required to notify affected individuals, regulatory authorities, or other relevant stakeholders following a data breach or loss. The specific notification timelines, content, and procedures can vary, so it's important to consult the applicable laws and regulations.
3. Record Retention and Destruction Policies: Local governments often have regulations outlining record retention and destruction requirements. It's crucial to establish appropriate policies and procedures for the retention, storage, and disposal of data to mitigate the risk of data breaches and ensure compliance with these regulations.
4. Compliance with Industry-Specific Standards: Local governments may need to adhere to industry-specific standards or frameworks pertaining to data security and privacy. For example, in the United States, the National Institute of Standards and Technology (NIST) provides guidelines and frameworks, such as the NIST Cybersecurity Framework, which can help inform best practices for data protection and incident response.
Small Business:
1. General Data Protection Regulation (GDPR): If a Small operates within the European Union or handles personal data of EU citizens, compliance with the GDPR is crucial. The GDPR enforces obligations on organizations to safeguard personal data, inform relevant supervisory authorities and affected individuals in case of a data breach, and implement appropriate security measures.
2. California Consumer Privacy Act (CCPA): If a small business collects personal information from California residents and meets certain criteria, you may need to comply with the CCPA. It requires providing specific notices to affected individuals in the event of a data breach.
3. Health Insurance Portability and Accountability Act (HIPAA): If a small business deals with protected health information (PHI) in the healthcare industry, you must comply with HIPAA regulations. HIPAA necessitates reporting data breaches to affected individuals, the U.S. Department of Health and Human Services (HHS), and in certain cases, the news media.
4. Payment Card Industry Data Security Standard (PCI DSS): If a small business accepts credit card payments, you must comply with PCI DSS requirements. PCI DSS includes guidelines for securing cardholder data, detecting and responding to breaches, and notifying payment card brands and individuals affected by a breach.
Non-Profit Organizations:
1. General Data Protection Regulation (GDPR): If a nonprofit operates within the European Union or handles personal data of EU citizens, compliance with the GDPR is crucial. The GDPR enforces obligations on organizations to safeguard personal data, inform relevant supervisory authorities and affected individuals in case of a data breach, and implement appropriate security measures.
2. Data Breach Notification Laws: Nonprofits must adhere to data breach notification laws specific to their jurisdiction. These laws typically demand organizations to swiftly notify affected individuals, regulatory authorities, and sometimes even the media about data breaches. The notification requirements may differ in terms of timing, content, and the specific circumstances that trigger the obligation to notify.
3. State or Provincial Privacy Laws: Nonprofits operating within particular states or provinces must follow specific privacy laws that outline requirements regarding data breaches or losses. These laws may include provisions for reporting breaches, informing affected individuals, and implementing security measures to protect personal information.
4. Nonprofit-Specific Regulations: Depending on a nonprofit's mission, activities, or funding sources, there could be particular regulations or standards applicable to the organization. For instance, nonprofits in the healthcare sector might need to comply with the Health Insurance Portability and Accountability Act (HIPAA), which includes breach notification requirements for protected health information (PHI).
Gotta Have a Plan and Take Time to Practice
 One of the best ways to measure the effectiveness of a plan, once it's developed, is to conduct an exercise (and routinely practice) as a solution for achieving the best outcome for your business or organization. The following are some (free to download) examples, from trusted sources, that can help, including:
One of the best ways to measure the effectiveness of a plan, once it's developed, is to conduct an exercise (and routinely practice) as a solution for achieving the best outcome for your business or organization. The following are some (free to download) examples, from trusted sources, that can help, including:


 The purpose of the Indiana Privacy Toolkit is to provide a practical, FREE-to-download resource intended to help organizations gain a better understand of how privacy “works” and why it’s important. It is meant to be a step-by-step guide, with information tailored to fit the needs of a variety of small businesses and not-for-profit organizations, as well as local government.
The purpose of the Indiana Privacy Toolkit is to provide a practical, FREE-to-download resource intended to help organizations gain a better understand of how privacy “works” and why it’s important. It is meant to be a step-by-step guide, with information tailored to fit the needs of a variety of small businesses and not-for-profit organizations, as well as local government.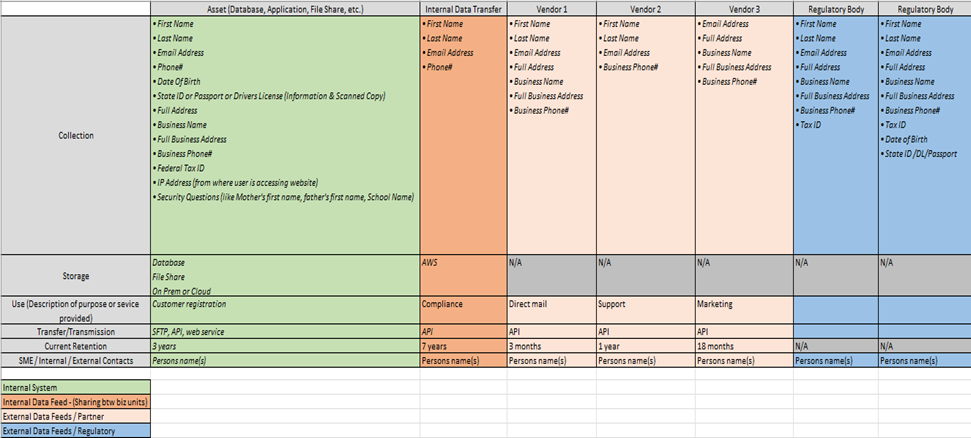
 One of the best ways to measure the effectiveness of a plan, once it's developed, is to conduct an exercise (and routinely practice) as a solution for achieving the best outcome for your business or organization. The following are some (free to download) examples, from trusted sources, that can help, including:
One of the best ways to measure the effectiveness of a plan, once it's developed, is to conduct an exercise (and routinely practice) as a solution for achieving the best outcome for your business or organization. The following are some (free to download) examples, from trusted sources, that can help, including: