WELCOME TO THE INDIANA CYBER HUB BLOG
The Indiana Cyber Hub Blog is your all-new, online resource featuring helpful advice and guidance from the Hoosier State's Cybersecurity Program Director, along with the perspectives of a wide range of cyber industry experts.
Data Defense Directives Offer Sound Strategies for Protecting Your Personal Information
Wednesday, October 30, 2024
Blog topics:
 PERSPECTIVES FROM THE CAMPUS
PERSPECTIVES FROM THE CAMPUS
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name, “Perspectives from the Campus”, we invite experts – immersed in the pursuit of educating their students – to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the latest installment of this series, David Dungan, who serves as the executive director at the Center for Security Services and Cyber Defense at Anderson University, shares his perspective on the four key defenses we can use to protect our personal data.
By David Dungan
Did you know researchers estimate that 61 percent of Americans have had their personal data compromised and 45 percent of Americans have had their data compromised in a breach within the last five years.
Additionally, 44 percent have been involved in more than one data breach. Because millions of records are exposed every month, it is paramount that users take precautions to defend their data. Fortunately, there are several defenses that can be deployed to protect your personal information. Moreover, these techniques can be used to help in an effort to protect one’s data from being accessed as part of a data breach.
The first data defense directive is to use a virtual private network (VPN). VPNs encapsulate network traffic and encrypt data in transmission, in such a way that it cannot be accessed by unauthorized users. This also prevents what is known as data breadcrumbs from being left behind after browsing sessions. By using a VPN, you can ensure that your data is only going where you want it. This is a tool that’s especially important to use if you are in a public place, such as a coffee shop, airport, or even a retail store. It’ll help in needing to rely on a free public Wi-fi network that anyone could access.
The next directive is to consider freezing your credit. In the event of a data breach, threat actors will be unable to apply for credit cards or loans – even if they swipe your social security numbers, birthdays, names, or other personal information. Once frozen, your credit stays frozen. No activity is allowed unless or until you lift the freeze yourself. As an aside, freezing your credit doesn’t negatively impact your credit score!
The third directive is to limit with whom, where, and how your data is stored.
While it may be convenient to store your credit card information and login credentials with apps or websites you frequently visit, doing this creates a security risk for your personal information. It’s worth taking a few extra seconds to manually enter your payment information or credentials each time you visit certain sites. Also, it’s a good idea to read the privacy policies before giving your personal information to any company.
If possible, avoid companies that share your information with third-party brokers. For companies that store or transmit your data, make sure they are applying end-to-end encryption, hashing, and other defensive security controls. Before giving any information to these companies, conduct your research, read other customer reviews, and scan the Terms and Conditions. Finally, it’s absolutely OK to be skeptical and ask questions. You can’t be too careful when it comes to sharing personal data.
The final data defense directive is to join a personal data clean-up subscription service. You can arrange for these applications to select what data you want removed from the web and the service goes out into the Internet and cleans up your stored (and vulnerable) information. Among the personal data clean-up services that are out there include:
- DeleteMe
- Kanary
- Mozilla Monitor Plus
- Optery
- Privacy Bee
Here in the Hoosier state, there are other FREE resources, available from state government, that you can access by visiting the Indiana Cyber Hub website. In the event you suspect your data has been stolen, there are steps you can take, whether you’re an individual or it involves a company or organization, to report the incident and begin recovering.
By following these steps and always being vigilant with personal data, you can experience a greater peace of mind that your data is secure from threat actors.
COMIC STRIPS ILLUSTRATE IMPORTANCE OF CYBERSECURITY, OPPORTUNITY TO LAUGH AS WE LEARN
Wednesday, October 23, 2024
Blog topics:
 PERSPECTIVES FROM THE FIELD
PERSPECTIVES FROM THE FIELD
The strength of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the Indiana Executive Council on Cybersecurity (IECC). Hence the name “Perspectives from the Field”, we invite experts to discuss the real and challenging issues that we’re facing in cybersecurity, along with the solutions that could help improve our quality of life for all Hoosiers.
In the latest installment of this series, Adenike Oriolowo, who works as a cybersecurity engineer with the City of Indianapolis and as a member of the digital strategy team for the Indianapolis Public Schools (IPS), shares her thoughts on what led her to create an imaginative series of comic strips as a way to help people, especially senior citizens, younger kids and teenagers, to learn about cyber in a way that’s fun, informative and engaging.
When it comes to learning a skill, or taking a class, I think we’d all agree that it should be fun, right?
With that in mind, it occurred to me that I could use this approach even with something that (for a lot of us) can be complicated, like cybersecurity.
Within our society, children and older adults are two groups of people, who are particularly vulnerable for a variety of reasons. And, in today’s ever-changing digital world, cybercriminals have found a way to do everything from stealing a child’s identity – before they’ve started kindergarten – to convincing someone’s grandparent, using artificial intelligence (AI) to create a fake audio recording of a child’s voice, to lose hundreds, if not, thousands of dollars because they are falsely led to believe that their grandchild is in jail, or in the hospital. It’s heartbreaking.
Yet, as with some of the other things we know that we need to do, we struggle with – and even tune out – the messages and the information that are intended to help us. This is especially true in cyber, whether we’re talking about creating strong passwords or using multi-factor authentication.
That’s where the idea of creating a comic strip came from, based on the belief that telling a story, especially visually or interactively, could help us process it more effectively.
Not only that, but it was also my belief that a comic strip could make these topics more relatable and approachable. In other words, it would engage the audience in a way that traditional methods cannot.
As an illustration, one of my most recent exposés focused on elder fraud, in which older adults are duped into disclosing private login information to scammers or are victims of credential theft. In addition, I've authored exposés on how predators lure children into risky situations by using free, open-access online games. These examples illustrate what it means to be secure online and, for all of us, to be aware of potential threats, like malware or phishing scams, in real-world situations.
In taking the time to read the comics I’ve created, you’ll be able to witness an outcome and discover how it occurred, amplifying the impact of the cyber threat and strategies for mitigating it.
In the short term, my aim is to utilize a method for using virtual reality (VR) as an innovative tool for cybersecurity education. By doing so, we can immerse children and seniors in real-world scenarios while providing a safe, entertaining, and humanized virtual environment fully integrated into the scene and presenting them with various threats in a controlled environment.
They will be fully aware of the dangers, able to see and hear them, and will receive guidance on responding to these threats. Ultimately, the goal is to help people become more safety-conscious through interactive experiences. That’s for another day, but I hope you’ll enjoy taking some time to “read the comics”, celebrate Cybersecurity Awareness Month and share the stories I’ve created to help others learn more about cyber in a way that’s as engaging as it is educational.
Cybersecurity and Mental Illness: Resources Available to Stay Safe, Avoid Scams
Wednesday, October 9, 2024
Blog topics:
 PERSPECTIVES FROM THE CAMPUS
PERSPECTIVES FROM THE CAMPUS
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name, “Perspectives from the Campus”, we invite experts – immersed in the pursuit of educating their students – to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the latest installment of this series, David Dungan, who serves as the executive director at the Center for Security Services and Cyber Defense at Anderson University, discusses the impact, in terms of our mental health, that being impacted by a cyber crime can have on all of us.
By David Dungan
Even as we celebrate Cybersecurity Awareness Month throughout the month of October, it’s understandable that, at times, the news we hear and read about cybersecurity speaks of the latest cryptocurrency, job, or grandparent scams so often that it can induce a sense of detachment for many of us.
In that moment, it can seem as though we’re, somehow, brushing aside the fact that in 2023, more than 11,000 Hoosiers were the victim of a cybercrime – ranging from scams involving identity theft, ransomware, and real estate to devastating threats of extortion, violence, and crimes against children, with losses reported in excess of $222.8 million.
What’s worse, these scams – for some people -- become a part of a difficult reality they live in, either because they’re unaware of the scam they’ve been tricked into, or they’re reeling from the financial and occasionally emotional loss they’ve experienced. Because of that, it’s essential to consider the mental health of those who have been scammed. According to data from the FINRA Investor Education Foundation, fully two thirds of individuals, who’ve been impacted, report that they’ve experienced emotional costs from fraud, including “…stress, depression, frustration, anger, other psychological consequences, (as well as) sleep deprivation…”
As is often the case, many of these scams deliberately target people, who are the most vulnerable. It’s important, too, to keep in mind that it doesn’t define or diminish those who have lost money or confidence due to the actions of another.
When it comes to the age and generation of the people who are impacted, it’s important to know:
- A Gallup poll from 2023 suggests that eight percent of American adults have fallen victim to a scam within the past 12 months, and it is more likely for individuals with lower incomes and adults with no college education to be scammed.
- It’s not just older Americans who are the victim of a cybercrime; research suggests that younger adults ages 18 to 59 are actually more likely to fall for scams in general, especially those involving online shopping, investment, and job postings/offers.
- Conversely, seniors are more likely to fall victim to tech support, lottery, and family/friend imposter scams.
So, what can we do?
If you have a loved one, who has been a victim of a cybercrime or you suspect they’re at risk of being scammed, it is best to be empathetic to their experience, understanding that it is common for individuals who have been victimized to feel shame or embarrassment. Discuss the topic in private, and help direct them to resources that can be trusted.
Here in Indiana, you can visit the Indiana Cyber Hub website and go to the Report a Cyber Incident page. All of the services/resources are free, and it provides information on the steps someone can take as an individual to report a case of identity theft, as well as the type of reporting that is recommended if you’re a part of an organization.
Additionally, here are some helpful steps you can take, including:
- Talking with a close friend or family member, who, you believe, will be non-judgmental about your situation and will assist you in seeking out the resources to support you and help you begin the process to recover.
- Knowing it’s normal to experience negative emotions because of a scam or a cybercrime.
- It’ll be difficult, but it’s important to stop communicating immediately with someone, if you believe they might be trying to mislead you or they’re pressuring you to do something, such as making a decision involving your financial well-being or your personal information (or that of someone close to you).
In the unfortunate event that you or a loved one have been defrauded and you have already done so, be sure to contact the victims’ bank or financial institution to report the fraud and contact a law enforcement agency, including:
- FBI - Internet Crime Complaint Center (IC3) - The FBI Internet Crime Complaint Center's (IC3) mission is to receive, develop, and refer criminal complaints regarding the rapidly expanding arena of cybercrime. The IC3 gives the victims of cybercrime a convenient and easy-to-use reporting mechanism that alerts authorities of suspected criminal or civil violations.
- FBI Cyber - The FBI is the lead federal agency for investigating cyberattacks and intrusions. To learn more about what you can do to protect yourself against various forms of cybercrimes, FBI Cyber offers a great deal of information and resources including:
- Indianapolis Cyber Fraud Task Force
- Cyber incidents that are financially related can be reported to the Indianapolis Cyber Fraud Task Force at: ind-cftf@usss.dhs.gov or call (317) 635-6420.
- Indiana State Police (ISP)ISP’s Cybercrime & Investigative Technologies Section is staffed with detectives who specialize in conducting cybercrime investigations. Call (317) 232-8248.
If you see that your loved one’s mental wellness is being negatively affected, consider contacting a mental health expert, such as a counseling and therapy service. In a mental health crisis, Indiana also offers 988 as a mental health services hotline or contact 911 in the event of an emergency.
In following these steps, we can help to reduce the number of scams that occur on an everyday (and annual) basis and begin to experience more of the “good” that comes from cybersecurity and gives us a reason to celebrate! Be safe out there!
Cybersecurity Awareness Month: A New Job for All of Us – Cyber Defender (Everyone Need Apply)
Wednesday, October 2, 2024
Blog topics:
 Whether you’re the chief privacy officer for a major corporation, or you’re a “team of one” who’s in charge of making sure the operations of your town’s water plant are safe and secure, cybersecurity is a big part of your job that, at times, keeps you up at night.
Whether you’re the chief privacy officer for a major corporation, or you’re a “team of one” who’s in charge of making sure the operations of your town’s water plant are safe and secure, cybersecurity is a big part of your job that, at times, keeps you up at night.
Of course, as we’ve come to discover in very real terms, cyber threats impact all of us.
And it’s fair to say that any time we’re online, there’s going to be a cybercriminal with a scam who’s out there trying to steal our money, as well as our personal data and financial information. And there’s also an entire operation of nation state actors (in Russia, China, Iran, North Korea and elsewhere) who are targeting our critical infrastructure. In fact, according to a recent report from Consumer Reports, Aspen Digital, and the Global Cyber Alliance, one in five American adults, who have encountered online scams have ended up falling for one of them and losing money.
As all of this is occurring, it’s fitting, perhaps, (and just in time for Cybersecurity Awareness Month, as proclaimed here in Indiana by Gov. Eric Holcomb, as well as nationally), we’ve all got a new job title – cyber defender.
It certainly has a nice Marvel Superheroes feel to it, right?
That’s the message from Jen Easterly, who serves as the director of the Cybersecurity and Infrastructure Security Agency (CISA), whose role (and importance) as “America’s Cyber Defense Agency” can’t be understated for the work they do, in partnership with state and local government, as well as other federal agencies, including the Federal Bureau of Investigation (FBI), among others.
In asking us to pick up a shield, throughout the month of October, CISA and the National Cybersecurity Alliance will focus on ways to “Secure Our World” by encouraging everyone to adopt four simple steps to stay safe online, including:
- Use strong passwords that are long, random, and unique to each account, and consider using a password manager to generate them and to save them.
- Turn on multifactor authentication (MFA) on all accounts that offer it. We need more than a password on our most important accounts, like email, social media, and financial accounts.
- Recognize and report phishing, as we like to say, think before you click. Be cautious of unsolicited emails or texts or calls asking you for personal information, and don't click on links or open attachments from unknown sources.
- Update software. In fact, enable automatic updates on software so the latest security patches keep devices we are connected to continuously up to date.
Additionally, CISA offers a wealth of resources on its Cybersecurity Awareness Month website, which includes a toolkit, tip sheets, and animated videos.
In the Hoosier State, cybersecurity continues to be a top priority, as evidenced by the work of the Indiana Executive Council on Cybersecurity, together with the leadership exhibited by the Indiana Office of Technology and the free services IOT provides for local government and the Indiana Department of Homeland Security, whose services extend across Indiana as it involves  cyber resiliency and response and supporting emergency personnel with their preparedness to keep aal of us safe and protected. There are also a wide range of resources, best practices and tips that are featured on the website you’re visiting, also known as the Indiana Cyber Hub website. As if it’s not enough of a reminder, cybersecurity is an important part of our daily life, whether we’re at home with our family, at work, or at school, as well as anytime we’re online. In celebrating Cybersecurity Awareness Month, it’s a great time to take just a few minutes to follow these steps and use our “superpowers” – every day and throughout the year – to stay safe and protected.
cyber resiliency and response and supporting emergency personnel with their preparedness to keep aal of us safe and protected. There are also a wide range of resources, best practices and tips that are featured on the website you’re visiting, also known as the Indiana Cyber Hub website. As if it’s not enough of a reminder, cybersecurity is an important part of our daily life, whether we’re at home with our family, at work, or at school, as well as anytime we’re online. In celebrating Cybersecurity Awareness Month, it’s a great time to take just a few minutes to follow these steps and use our “superpowers” – every day and throughout the year – to stay safe and protected.
Cybercriminals Aiming for Different Kind of Jackpot with Your ATMs
Wednesday, September 25, 2024
Blog topics:
 By Joe Henrich
By Joe Henrich
When it comes hitting a jackpot, we often think of someone winning a LOT of money, either while standing at a slot machine at a casino, or because they’ve won the lottery.
But now, unfortunately, “jackpotting” is a term that’s being used to describe the means by which an attacker can get an ATM machine to dispense cash outside of its normal legitimate transaction-based processing.
The first of these attacks began occurring in the U.S. back in 2018 and there are three methods that have been used to carry out this type of heist, including:
- Malware based – This is when malware is introduced into the operating system of the ATM. This is done by gaining access to a USB port on the ATM being physically accessed. The malware then sends the dispense commands to the dispenser causing it to distribute the cash.
- Black Box Attacks – is achieved by disconnecting the cash dispenser from the ATM’s motherboard and connecting it to an attacker’s device to interact directly with the cash dispenser.
- Man-in-The-Middle – involves the attacker placing their own device between the ATM and the host service provider. The attacker then responds to transaction authorization requests from the ATM without actually reaching out to the core networks.
While these attacks have been common in Central and South America for many years, within the past year, they have begun to become more prevalent, with reports of attempts coming from Utah, Minnesota, Texas, Colorado, Idaho, Maryland, Georgia, North Carolina, South Carolina, Tennessee, California, Pennsylvania, Oregon, Washington and New York.
In one such case, in Indiana, the attackers were able to locate the alarm and disable it, so as to prevent it from being activated. In response, the bank used a different method for installing some of the equipment to make it more secure.
Of course, as with a lot of things involved with cybersecurity, there is no one “silver bullet” to protecting an ATM, whether it is operated by a bank, credit union, or other type of financial institution, or it is privately owned, it takes a layered approach. But there are steps you can take that includes:
- Ensuring attackers can’t physically access the computer inside the ATM. The whole ATM should be alarmed, not just the vault. Opening the upper enclosure (also known as the “top hat”) should trigger an alarm.
- Next, the computer inside the ATM should be treated just like any other computer that could end up in a hostile environment. Its USB ports should be disabled, if not in use.
- The computer also needs to be running advanced anti-malware to block any unwanted applications. Software whitelisting should also be employed.
- To defeat Man-in-The-Middle attacks, your machines should be using the highest available version of safe communications (TLS encryption) when talking to the host network.
- To defeat Black Box attacks, your dispensers should require secure handshakes with the operating system in order to become active (e.g., unique image bonding, high level dispenser settings). And to protect against many other types of attacks, the hard drives of your ATMs should use full disk encryption and employ their TPM defenses and/or BIOS password management. An attacker should not be able to swap their own hard drive in and boot the hardware.
What’s more, it’s a good idea to work with whoever manages your ATM fleet to ask about the protections available for your machines, as well as which ones you actually have to set up. As a Financial Industry, we should be demanding these types of security as the default from the manufacturers, not just as an add-on for an additional price.
For more information, be sure to check out information from ATM USA that includes some additional safety recommendations related to not only physical attacks, but also tips to keep in mind when it comes time to refilling an ATM with cash, along with a few other methods for keeping your staff and your equipment safe and secure.
Cyber Insurance Toolkit – Free Resource for Making Sense of Tech-Driven Risks, Liabilities
Wednesday, September 11, 2024
Blog topics:
 At a time when cyber insurance claims in North America have reached record levels, there’s a free-to-download resource that is available to help businesses and organizations better understand what cyber liability insurance is, what it covers, and, most importantly, why it’s become a vitally important part of a company’s risk management strategy.
At a time when cyber insurance claims in North America have reached record levels, there’s a free-to-download resource that is available to help businesses and organizations better understand what cyber liability insurance is, what it covers, and, most importantly, why it’s become a vitally important part of a company’s risk management strategy.
Utilizing the knowledge and expertise of insurance professionals and members of the legal profession – as part of the Indiana Executive Council on Cybersecurity (IECC) – the Cyber Insurance Toolkit features a wealth of information from trusted sources that covers everything from the types of questions to consider asking as part of an underwriting document to understanding how you can implement reasonable security controls (without spending a great deal of money) while, at the same time, exercising due diligence.
Cyber insurance covers the financial risk and exposure that arises from unauthorized access to one’s network and the inappropriate disclosure of private or confidential information. It is also intended to guard against cybercrimes, such as business email compromise or funds transfer fraud. Cyber insurance is an important factor to consider when updating your cybersecurity policies or developing an incident response plan.
The easy-to-use Toolkit features several key sections, including:
- Underwriting questions that typically appear on an insurance application (along with the resources that’ll help you).
- Implementing (and what is meant by) “reasonable security controls”.
- Understanding what your risk exposure is (when) a data breach occurs.
- Glossary of Terms – as it relates to the insurance industry and policies, as well as cybersecurity and technology.
Given the fact that we’ve reached a point where technology-related activities that could impact a company or organization of any size includes not only cyberattacks, but also extends to misplaced cell phones and incidents involving the use of artificial intelligence (AI), it can be a challenge to understand what you need while, at the same time, balancing that with a policy that ensures you are covered for the exposures that are critical for providing adequate protection for your company’s most important assets and data.
According to the 2023 Internet Crime Report, from the FBI, Ransomware incidents continue to be impactful and costly, as there were more than 2,800 reported complaints and losses totaling $59.6 million.
This is especially important when to comes to handling someone’s Personally Identifiable Information (PII), such as Social Security numbers, bank account information and personal health information (such as HIPAA-covered information), as well as payment card information, or confidential corporate information, which could be addressed in a contract or agreement, or even something that is shared in an email or a text message.
For all those reasons, the Cyber Insurance Toolkit can provide a playbook to help make sense of the risks and liabilities before or, more precisely, when something happens that you and your company will have arrived at a solution that’s as affordable as it is effective.
A First in the US: An Entire Week Dedicated to Celebrating Women IN Tech
Wednesday, September 4, 2024
Blog topics:
 By Kara Kavensky
By Kara Kavensky
Women have been integral to Indiana’s tech landscape for decades, serving in various roles such as Agile experts, software developers, cyber analysts and process leaders. Despite making significant contributions to technology, women in IT roles and tech careers across our state and nation have often been overlooked. According to the U.S. Department of Labor Women’s Bureau, only 17 percent of Chief Information Officers are women, and only 25 percent of all jobs in the tech industry are currently held by women — this is the lowest number of women in technology since before 1980 – and STEM careers are anticipated to grow by nearly 8.5 percent by 2029.
This disparity has not gone unnoticed. Efforts, such as TechPoint’s Mission 41K, have been designed to attract more women into the growing technology field as Indiana strives to be a leader in this area.
Recently, Governor Holcomb signed the first-of-its-kind-in-the-U.S. proclamation dedicating Women IN Tech Week, September 15-22, 2024. Women IN Tech Week presents an opportunity for companies, communities and educational institutions to acknowledge and celebrate the invaluable contributions of women across the state.
As an advocate for women in tech, Karrah Herring, Indiana’s Chief Equity Inclusion & Opportunity Officer, has worked tirelessly for the past four years with an affinity group, Government Women in Technology. That effort has focused on creating a supportive ecosystem for women in technology, advocating for the empowerment and elevation of capable women in technology, and motivating and modeling ways to inspire women to choose STEM careers.
“I am pleased that Governor Holcomb and his team have issued a proclamation declaring September 15-22 Women IN Tech Week for Indiana,” shares Herring. “We must continue to create pathways to success and promotion for women in technology across diverse industries. Because of the amazing advocacy of Linda Calvin and Kara Kavensky, this state proclamation will help reinforce and elevate the importance of those efforts.”
Contributions of women in the technology workforce have been critical to the development of our new economy, our culture and artistic achievements, our social and technological advancement and all areas of accomplishment. Indiana has reaffirmed its commitment to promote the recruitment, retention, and support of women in technology by supporting Women IN Tech Week.
According to the U.S. Department of Labor Women’s Bureau, women account for nearly half of the workforce in this country. Women of every race, class and ethnic background play a key role in the advancing technology, contributing to the growth and strength of Indiana, our nation and the global community. Additional stats from the Women’s Bureau:
- Women make up 47 percent of all employed adults but hold only 28 percent of computing and math roles.
- Black and Hispanic women account for only 5 percent of the computing workforce, and representation has declined by 10 percent from 2018 – 2022.
- Only 8-9 percent of women hold positions like CIO, CTO or Senior IT Manager.
“Building Indiana’s tech talent pool is essential for driving innovation, boosting the state’s Gross Domestic Product and creating rewarding career opportunities for Hoosiers across various sectors,” says Linda Calvin, Chief Impact Officer, Reboot Representation and President of Transcend Consulting. “Women are pivotal to achieving these objectives, and Women IN Tech Week opens the door for meaningful discussions on how we can better support women and girls in Indiana’s tech economy.”
This initiative will play a crucial role in inspiring more girls to pursue careers in tech by celebrating role models, sharing success stories, and hosting events highlighting the diverse contributions of women of all ages, backgrounds, and ethnicities to Indiana’s tech ecosystem. As the saying goes, “When you see us, you can be us.”
To join in this celebration, any and all organizations, municipalities and companies may celebrate on any given day during the week or throughout. A downloadable media kit and ideas to celebrate Women IN Tech Week are available on the website, as well as Events, female IT Speakers Bureau, videos of female tech leaders and more.
Ways to celebrate include:
- Utilize the Women IN Tech Week logo in social media posts with the tag #womenINtech
- Create social posts (in Canva, for instance) with co-branded logos of your organization (templates on website).
- Already have a set meeting that week? Brand it to celebrate Women IN Tech!
- Include the names of these amazing women to your internal eNews to celebrate them!
- Send these amazing women working in tech within your organization a note of gratitude.
- Leverage the momentum of Women IN Tech Week to help attract more women to enter the tech field and to help retain talent.
- Have your local elected official sign a proclamation (draft in media kit) for a Women IN Tech Day in your community.
For more information, contact Kara Kavensky or Linda Calvin via LinkedIn.
SURE, YOU’VE GOT A CYBERSECURITY POLICY, BUT DO YOU HAVE A “RESPONSE PLAN”?
Wednesday, August 28, 2024
Blog topics:
 At a time when, some days, it may feel as though cybercriminals are playing chess and the rest of us are playing checkers, there’s one thing that a company or organization can do to help make sure it’s ready when a cyber incident or cyberattack occurs.
At a time when, some days, it may feel as though cybercriminals are playing chess and the rest of us are playing checkers, there’s one thing that a company or organization can do to help make sure it’s ready when a cyber incident or cyberattack occurs.
Because while it’s essential for all of us to keep creating strong passwords and using multi-factor authentication, practicing cyber hygiene is only part of the equation. At some point, it’s (more than) likely you’re going to take a hit, as evidenced by the fact that, in 2023, there was a 72 percent increase in the number of data breaches since 2021.
To borrow a line from the movie, “City Slickers”, the one thing is making sure you have an incident response plan.
Having a written document, one that’s formally approved by your company or organization, is crucial and it’ll help you before, during, and after an incident (even those in which you suspect something may have happened). More than that, it enables people to understand their roles and responsibilities and it’s a good opportunity to provide any kind of guidance that is needed for key activities.
Here in Indiana, to get you started, there are a wealth of free-to-download resources available on the Emergency Response and Recovery page on the Indiana Cyber Hub website. In addition to the Emergency Manager Cybersecurity Toolkit 2.0, there are four cybersecurity incident response plan templates (including ones for county and city government). Each template is easy to use and designed in a format that fits with your type of business or organization.
Before it Happens
Of course, the first step in any process, in which you expect your staff to be prepared, begins by providing them with the training they’ll need, along with the understanding that comes with anything that’s new; for everything from what they’ll want to look for when reporting something that’s suspicious to being sure that’s you are gracious, in the event someone reports a false alarm.
Among the other things you’ll want to prepare “before” an incident includes:
- Meeting your CISA regional team. (Yes, this is something you can use as a resource). You can find your regional CISA office information here.
- Meeting and getting to know your local law enforcement agency team. In coordination with your attorney, get to know your local police or FBI representatives. This will help you, so that you’re not just meeting them for the first time when something happens.
- Print these documents and the associated contact list and give a copy to everyone you expect to play a role in an incident. During an incident, your internal email, chat, and document storage services may be down or inaccessible.
- Review your plan quarterly. The best response plans are living documents that evolve with the changes occurring within your business or organization.
- Making sure you have responses for the news media prepared in advance. If a reporter calls you, claiming to have data stolen from your file, you’ll want to be ready with information that’s accurate and appropriate to the situation.
When it Happens
During an incident, there’s three important assignments you’ll want to have identified ahead of time, including the roles of an incident manager (to lead the response), a tech manager (to serve as the subject matter expert), and a communications manager (to handle the information that’s shared internally, as well as with the press and your external stakeholders (i.e. shareholders, customers, school community).
After it’s Over
After a cyber incident is over, you’ll want to formally report out the known timeline for the incident itself and ask others for additions and edits. In going through this step of the process, be sure that these discussions must be blameless. For this part of the plan to have any value, people need to feel as though that they are free to openly discuss the incident in an environment that’s safe and supportive. Security incidents are rarely the result of one person’s action; the focus needs to be on the processes and identifying ways that it can be improved.
Another outcome will be to update any policies or procedures from the discussions that take place and, most importantly, you’ll want to be sure to communicate the findings – from what you’ve learned – with your staff. In doing so, you’ll provide the kind of transparency that builds trust and many staff will appreciate hearing how seriously the leadership of your company or organization consider security to be as a priority.
In the movie, when Curly is asked what’s the “one thing”, he replies “…that’s what you got to figure out”.
When it comes to having an incident response plan, what you decide and how it works will depend on a number of factors and, in all likelihood, it’ll be driven by how your school, local government agency or business is structed, but that’s OK, so long as what you’re doing helps keep everything – and everyone – safe and secure.
If it were a plot, cyber always offers it fair share of twists and turns and sometimes you don’t always know who’s the bad guy. But, with some proactive planning, you’ll have an opportunity to write a happier ending.
Heading Back to School? Cybersecurity is Our "Trapper Keeper"
Wednesday, August 21, 2024
Blog topics:
 Whether your kids are starting back to school to begin their first day in kindergarten, or it’s the last time you’re moving them back into an apartment or a house as they get ready to finish their last year of college, it’s easy to think back to a time when we were the ones, who were heading back into class.
Whether your kids are starting back to school to begin their first day in kindergarten, or it’s the last time you’re moving them back into an apartment or a house as they get ready to finish their last year of college, it’s easy to think back to a time when we were the ones, who were heading back into class.
Of course, when it comes to making sure that our students have everything they need, there are few “must have” school supplies that rivaled the popularity of the Mead “Trapper Keeper”.
Launched in 1981, the Trapper Keeper, with its retro cover designs and multiple folders with vertical pockets worked perfectly (for kids of all ages) for holding all of their notes in place no matter what happened.
With an original price of $4.85, the Trapper Keeper saved time, stress, and locker space. In fact, the all-in-one organizers were so popular that adults started buying them as well. That may explain why Mead was able to sell more than 75 million of them, with some of the designs becoming collectors’ items.
So, what in the name of E. Bryant Crutchfield and Jon Wyant does an 1980’s era pocket folder have to do with cybersecurity? Let me explain…
Here in Indiana, there are more than 2,200 urban, suburban, and rural K-12 schools, with 1.2 million students and about the only thing there’s “more of” (aside from textbooks) is the amount of personal identifying information (PII) that exists within these school districts; that’s the data that exists on every student, as well as their family members, even their emergency contacts. That’s just one of the reasons why the education sector experienced a 44 percent increase in cyberattacks from 2021 to 2022. What’s more, the value of a full data set, enough to steal someone’s identity, costs as much as $1,000 on the dark web.
Fortunately, just as the Trapper Keeper was ideal for helping to make sure nothing important was lost, there is a wealth of cybersecurity resources that are FREE to download using the Cybersecurity for Education Toolkit 2.0.
First developed in 2020 and updated in 2023 by the Indiana Executive Council on Cybersecurity (IECC), in partnership with the Cybersecurity Infrastructure and Security Agency (CISA) and the Indiana Department of Education, It is geared for everyone in a school community including staff, school board members and superintendents, as well as the rest of us, regardless of whether or not you had kids in school.
In addition to the Toolkit and the information you’ll find on the Indiana Cybersecurity Hub website, there’s more being done with cybersecurity to help protect keep these critical systems secure.
if you’re a part of a school’s technology department, there is a program known as Cybertrack, which is designed to put local school districts (and local governments) in contact with top-tier cybersecurity experts. It is a no-cost program – through sponsorship from the Indiana Office of Technology – that provides an actionable cybersecurity assessment report.
More and more, we’re reminded each day about how cybersecurity is intertwined into the fabric of our everyday life, whether we’re at home, at work, or at school and whenever we’re online. And while it’s easy – for a lot of reasons – to sigh a little bit, at the prospect of knowing we have to be prepared by following a few (otherwise) simple steps, or making sure we’ve done everything we can to protect ourselves and our personal data, it’s good to know that once we’ve done that, we’ll have that same level of confidence that some of us had when we were walking around at school with our oh-so-cool Trapper Keeper!
Here's hoping it’s a cybersafe school year!
Don’t Miss Your Shot to Grow During Indiana Women in Tech Week
Wednesday, August 14, 2024
Blog topics:
A study by the Girl Scout Research Institute shows 74 percent of teen girls are enthusiastic about Science, Technology, Engineering and Math (STEM) subjects, but in Indiana, women represent only about 28 percent of the tech workforce.
This significant discrepancy raises important questions about the barriers preventing these talented young women from entering and thriving in the tech industry. What factors are contributing to this gap between interest and representation? It is crucial for Indiana to address these issues by implementing targeted support programs, fostering mentorship opportunities, and creating inclusive educational pathways. By investing in initiatives that bridge this gap, such as Mission 41k, Indiana can help transform the landscape of the tech workforce and ensure that the growing number of young women interested in STEM have the support they need to succeed and contribute to the field.
Governor Eric Holcomb’s proclamation designating September 15 – 22, 2024, as Women IN Tech Week is a pivotal step in Indiana’s journey towards fostering inclusivity and innovation in technology.
Indiana has long produced legendary basketball players, and recently welcomed top female basketball players such as Aliyah Boston and Caitlin Clark. This summer we have witnessed women achieving parity at the Paris 2024 Olympics. It is the first Olympic Games to achieve full gender parity, with women representing 50 percent of all athletes.
My hope is that support for gender parity and the celebration of women does not remain inside sporting arenas, but transcends into all areas, especially in growing to diversify our tech workforce here in Indiana.
I see Women IN Tech week as a great opportunity to build on this momentum, especially as emerging technology creates new and exciting positions and opportunities. Indiana must remain focused on ensuring women and other historically disadvantaged groups have equal opportunity to fill those exciting roles in artificial intelligence (AI) and cybersecurity to name just two of the most areas currently in high demand.
The week’s events offer all of us opportunities to hear stories about women in tech and the trailblazing impact they have had on members of their community and to meet and network with women across all sectors in the state. I’m fortunate to be surrounded by women making their mark in tech like TechPoint leaders Ting Gootee, Chelsea Linder, Kristen Elfering and others, but I’m also eager to learn about stories I have never come across before and for this chance to connect with more women in tech.
In celebration of the upcoming week, I want to highlight two women in tech who have impacted me.
- Mary Ryan: Mary Ryan displays the many opportunities an individual can have within the tech ecosystem. Our paths crossed when we were both colleagues at Lev, where she helped showcase to me, early on in my career, the different roles in the tech industry. Mary currently serves as the Executive Business Partner at Stitch, a Martech Consulting and Business Services company. She has been an executive assistant for multiple tech companies here in Indiana, helping chief executive officers remain focused on the company’s goals and essentially keeping the company running towards those goals. She was also recently recognized with the Leadership Award by the Admin Awards. Mary was highlighted for her servant leadership and leading by example with tech certifications. Her work has immensely helped her tech startup company to continue to excel in Indiana and highlight the different roles one can have in the tech ecosystem.
- Crystal Bell: Crystal Bell is a bright young leader who is a force to be reckoned with. I had the opportunity to serve under her in the Orr Fellowship while she was the Chief of Staff. In this role, she inspired all of her colleagues to go out and make an impact in not only our careers, but also our local Indianapolis community. Crystal currently serves as a technology program manager at Open Lane, working closely with the Chief Technology Officer to advance OPENLANE's transformative initiatives. Outside of fostering tech growth for her company, she volunteers as a Big Sister with the Big Brothers and Big Sisters of Central Indiana and hosts the Startup Executive podcast, where she interviews current executives on what it takes to become an effective startup executive. Crystal inspires me to prioritize pouring into the next generation and sharing our community's stories.
I challenge you to share stories of others who have impacted with you, whether it be on LinkedIn, or just over lunch with friends. This isn’t boasting or bragging: it’s shining a light on accomplishments, that for too long have remained in the shadows. In celebrating these inspirational stories, we can encourage other women to take a chance, to launch their own companies or make other positive change.
How will you celebrate the inaugural Indiana Women in Tech week? What can you do to inspire the next generation to strive for careers in tech?
I encourage you to take time to reflect on the women in your lives who have made an impact within the Indiana tech communities and to celebrate them. You can do that by giving them a shoutout in a meeting, writing a personal note, sharing their story on your social media accounts or some other forum. I guarantee you that your words will have a positive impact. They might even inspire someone to take step that changes her world, and ours.
Want to learn more about Women IN Tech Week on September 15-22, 2024? Be sure to read up on all events happening on the Women in Tech Week website and look for me at one of these or some of the other events that will be announced soon.
- CTRL+ALT+EMPOWER: A Women in Tech Mentorship Event
- Women IN Tech Week Symposium & Showcase
- There's More to Tech than Coding
I hope to see you at a Women in Tech Week event!
The Secret Recipe for Safe Cyber Cookies: National Chocolate Chip Cookie Day
Sunday, August 4, 2024
Blog topics:
 Craving a cookie? It's the perfect day to celebrate, as today is National Chocolate Chip Cookie Day!
Craving a cookie? It's the perfect day to celebrate, as today is National Chocolate Chip Cookie Day!
But the ones we're talking about are the ones that "pop up" on nearly every website prompting you to accept their cookies, which begs the question, what are cyber cookies?
Accepting cyber cookies helps remember your site preferences for a personalized web browsing experience, making the world wide web that much more convenient for its users. If you often visit the same websites, accepting cookies helps personalize and optimize your experience; even keeping you signed in if you accidentally close your browser window.
Internet cookies are very popular, and we see them everywhere; but should we be clicking “accept cookies” when prompted? Users should be aware of what a trustworthy site is and avoid accepting cookies from websites that haven’t been certified as a trusted website.
A trusted site is one that has gotten what is known as an SSL Certificate, which acts as the website’s public key and validates its identity and information to be a valid site. Beyond that, web users should be sure to check the URL to make sure that it is spelled correctly and that it includes HTTPS as it acts as the protocol for sending data between your web browser and the websites you visit. As such, there are many ways to make sure that you are surfing a trusted site!
Now, I’ve never been known to turn down a cookie, but even the biggest dessert lovers need to understand that it’s OK to say no! Web users should be aware of the dangers of internet cookies and know when to decline them. You may be asking, "how can a cookie be dangerous?". Let us tell you more!
Malicious websites include tracking elements in their cookies that are invisible to users, that allow cybercriminals access to your online activity. Bad actors use that information to target users with custom-tailored malicious content like phishing emails or drive-by downloads which download malicious software onto computers.
Cyber cookies can be harmless, or they can be malicious, so how do you accept internet cookies safely? There are several steps that you can take to help avoid and minimize the dangers such as:
- Being cautious when exchanging personal information as cookies have the possibility to communicate such sensitive information.
- Deactivating the storage of cookies in your browser, which reduces the amount of data exchanges.
- Changing your browser’s privacy settings and avoiding storing passwords in the browser.
- Utilizing browser add-ons and anti-malware to disable third-party software to keep your browsing data private.
Most of all, it’s important to keep in mind that just as you don’t want to get scared away from sweets, like cookies, there are many ways to consume them safely. The same is true with the cookies that are out there online.
All it takes, often times, is having a great recipe to get what you want while, at the same time, staying safe, and keeping a cybercriminal from getting into the proverbial cookie jar to fill up their bank account by stealing your personal information. Have a great day and enjoy those chocolate chip cookies!
National Intern Day: It’s Way More Than Making Copies, Especially in Cyber – Part 2
Friday, July 26, 2024
Blog topics:
EDITOR'S NOTE: This week's Indiana Cyber Hub blog is a two-part series in celebration of National Intern Day and Indiana Intern Day. Part One of the series was posted on July 25th.
 In today's blog, we continue our conversation with Libby Stroud, who is completing an internship this summer with the State of Indiana and is working as a Communications Specialist with the Indiana Executive Council on Cybersecurity (IECC).
In today's blog, we continue our conversation with Libby Stroud, who is completing an internship this summer with the State of Indiana and is working as a Communications Specialist with the Indiana Executive Council on Cybersecurity (IECC).
Libby, what have you learned about cybersecurity?
I have learned just how many different vulnerabilities cyber can leave us with and how cyber criminals are able to take advantage of that to exploit unsuspecting people in so many ways. Bad actors are constantly looking for their next attack, and they don’t discriminate when it comes to choosing their victims. I used to think that cyber criminals’ main targets were large corporations. Now, I’ve learned that cyber scammers will target whoever they can get to, and small businesses are especially vulnerable. Cyberattacks are far more common than I realized before this internship. Cyber criminals are nothing if not talented when it comes to scamming for money and personal information; they can target any organization, any industry, and any person. Cybercrime exists in many different forms and costs people billions of dollars each year. I have learned a lot about cybersecurity this summer for everything from how hackers target people and exploit their vulnerabilities and how cyberattacks can be countered to how people can protect themselves against cybercrime, and the different abilities of cyber, just to name a few. That said, the cyber world is constantly evolving and there is always more to learn!
As someone who's grown up, you might say, with the Internet and digital technology, what would you say you've learned about cyber as part of your everyday life?
Cyber as part of your everyday life is a tool that can be used to simplify and complicate your life in more ways than I had ever considered. I thought that cybersecurity was something that only corporations (big or small) had to worry about, I didn’t think that it necessarily applied to ‘normal’ people for everyday protection.
Every day, cyber criminals are working to scam people out of their money and sensitive information. They are constantly scam calling, sending phishing emails, gaining access to people’s personal accounts, etc. While those are the negative everyday uses of cyber, it can also be used for personal protection! Cyber can be used to keep all categories of data including personally identifiable information and intellectual property more secure. There are so many ways that cyber can be used in everyday life to protect personal data such as keeping your software updated on all devices, being careful about what links you click on, and downloading anti-virus software for everyday protection. Cyber, whether we like it or not, is an essential part of everyday life that can keep you protected against cyber criminals and can be a huge convenience in your life if you are vigilant and use it responsibly.
What's the most interesting experience or something you've learned about cyber working with the State of Indiana?
Interning for the State of Indiana has provided me with a lot of interesting opportunities that have added to my professional growth during my time here at the Indiana Office of Technology (IOT). I have gotten to attend cybersecurity summits, sit in on meetings for various committees involved with the Indiana Executive Council on Cybersecurity (IECC), and have been introduced to many impressive people in the communications space, cybersecurity field, and members of government.
I have gotten to attend workshops that the Governor’s summer interns have access to that help support my professional development, as well as meet the Governor and Lieutenant Governor that had interesting topics to share during their discussions. I have gotten to meet the executives at IOT and hear about their views on cybersecurity and how they found themselves in the professional positions that they are in now, with their advice for “surviving” the cyber world. I have gotten the opportunity, too, to meet many different people that are involved in the cyber world in a multitude of capacities, and they have given me a more nuanced idea of how cybersecurity progresses both the state and the professionals that reside in it.
It has been so interesting getting a look into many professions and professionals involved in cybersecurity that I had not been exposed to prior to participating in this internship.
NATIONAL INTERN DAY: IT’S WAY MORE THAN MAKING COPIES, ESPECIALLY IN CYBER
Thursday, July 25, 2024
Blog topics:
EDITOR'S NOTE: This week's Indiana Cyber Hub blog is the first in a two-part series in celebration of National Intern Day and Indiana Intern Day. Part Two of the series will be posted on Friday, July 26th.
 Whether your career path is to focus on a career as a public relations strategist, or to work on building bridges as a field engineer, the value of gaining real world experience – as part of an internship or a co-op – is immeasurable.
Whether your career path is to focus on a career as a public relations strategist, or to work on building bridges as a field engineer, the value of gaining real world experience – as part of an internship or a co-op – is immeasurable.
After all, there are few experiences – aside from taking the classes required for your major, or the certifications that are necessary for a career in cybersecurity – that’ll provide you with the opportunity to perform work that is not only meaningful, but, more than that, one where you can benefit by being challenged with the responsibilities and assignments that you’re given – on a daily basis – by an employer; experiences that can help positively influence the decisions you’ll make about what it is you really want to do with your career that’s both rewarding and fun!
With that in mind, today, we celebrate National Intern Day and Indiana Intern Day; a “day”, both across the country and throughout the Hoosier State, for companies and organizations to honor and celebrate the hard work and effort of the people, who are dedicating their summer or a part of their school year to participate in an internship or co-op.
As someone who believes strongly in the value of mentoring, we want to be able to provide someone with a challenge, because as we like to say, once you start working, you’re no longer an intern, you are a part of our team.
That’s certainly true, as this summer, our team has had the pleasure of working with Lilly Stroud (pictured on the right), who is preparing for her senior year at the University of Cincinnati and getting ready to launch her career in public relations.
As our Communications Specialist, she has had the opportunity to play a lead role in working on everything from writing blogs and managing our social media marketing program on X, LinkedIn and Facebook, to helping us update our Indiana Cyber Hub website (and so much more).
In celebration of her work, as part of a two-part blog series, we sat down with Libby and asked her five questions reflecting on the time she’s spent with us and what she’s gained through her experiences in cybersecurity, PR and communications, and working as a part of state government.
In part one of our series, Libby discusses her interest in cybersecurity and shares what led to her decision to apply for the internship with the State of Indiana.
What is it about cybersecurity that interests you as part of your education and as something you might pursue as a career?
Cybersecurity interests me because it is an all-encompassing field that affects our daily lives in both good and bad ways. There are so many facets to cybersecurity that make it exciting to learn more about, and there are constantly new developments in the cyber world from cyber scams to data breaches - it’s always exciting! As far as a future career, I would be interested in pursuing a position doing PR in the cybersecurity space whether that be for a PR firm or in-house for an agency that deals with cybersecurity. Our world is ruled by cyber and when something goes wrong there are widespread consequences. The crises that are faced when an organization is facing a cybersecurity issue would be fun and challenging to handle as a PR professional!
Libby, you are studying public relations at the University of Cincinnati. What is it about working on the Indiana cybersecurity program that led to you applying to be an intern?
I applied to work on the Indiana cybersecurity program because it would allow me to get experience doing PR and communications in a field that I didn’t know much about. It would get me used to communicating about things that I’m not very educated on and that I would have to learn about over the course of the internship. I knew that by participating in this internship I would be introduced to two new career fields, cybersecurity and the public sector. I thought that it would be interesting to get more insight into what a job working for the state government looked like! I heard such great things about the work culture that comes with working in the public sector, and that was a major factor in me applying. It was important to me to not only gain experience, but to also work with someone who could serve as a mentor. I wanted to work closely with my supervisor to gain the critical knowledge I’d need to take with me into my career. The overview of the internship led me to believe that by being an intern, I would be able to network with impressive people in both the PR and cyber field and that I would learn more in this position than I have in any other internship that I’ve participated in before. And, let me just say, that couldn’t have been more true!
Be sure to come back and visit our blog page on Friday, July 26th, as we finish up our conversation – in celebration of National Intern Day and Indiana Intern Day – with Libby Stroud, as she talks about what she’s learned about cyber, her perspective as someone who’s “grown up” with technology and the Internet, and some insights into what she discovered what was most interesting about her experiences in working in cyber in the Hoosier state.
It’s National Lottery Day: Cybercriminals Are Taking Their Chances Winning Your Mega Millions
Wednesday, July 17, 2024
Blog topics:
 So, you’re trying your luck playing the lottery?
So, you’re trying your luck playing the lottery?
July 17th is National Lottery Day, and we’ve certainly all fantasized about how we would spend the lottery money if we won. Cyber criminals are aware of this and are capitalizing on peoples’ lottery dreams.
It might not surprise you to learn that the chances of someone being struck by lightning are actually more likely than the odds of winning millions in a lottery. For most of us, we play for fun while keeping our day jobs. Regardless, cybercriminals are taking their chances winning their own lottery off you.
The enjoyment of playing the lottery isn’t exempt from cyber scams, as lottery players are at risk of being targeted by cybercriminals trying to hit the jackpot. Bad actors have even gone as far as impersonating the Hoosier Lottery. They will send a letter or email to potential victims telling them that they have won the lottery and instruct them to call a number to claim their winnings. When the victim calls, they are greeted with a recording of the actual Hoosier Lottery hotline.
The scams don’t stop there- when do they ever, though, right? There are several red flags to look out for that indicate that a cyber criminal is testing their chances of hitting the lottery that makes you their payout, such as:
- A “lottery” notifying you that you have won the lottery. The Hoosier Lottery, and other state lotteries, will not reach out to you.
- Getting asked to pay fees to receive your winnings. Legitimate lotteries will not ask you for money or a payment in any form.
- The sender uses generic information in any emails or messages that are sent to you regarding the lottery. If they do not use personal information, the message is not for you.
- If you are being contacted, but you never bought a lottery ticket, you didn’t win the lottery.
Thinking about giving up on being the next mega millionaire? There are other options, if you would like to continue testing your luck!
The Hoosier Lottery has tips on their website for claiming your earnings in a way that’s safe and secure – where they encourage winners to send their ticket in via mail. It’s a great way to avoid getting caught in the crosshairs of a cybersecurity scam!
It’s an unfortunate reality that the possibility of winning the lottery can put just as much on the line as playing where cybercriminals are concerned, but that doesn’t mean that you have to hit the jackpot to safeguard your information and your money! Protect yourself from becoming a cybercriminal’s ‘Powerball’ by participating in these best practices for playing the lottery!
Hunting for Internships, Jobs Through Hoaxes
Wednesday, July 10, 2024
Blog topics:
 One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name, “Perspectives from the Campus”, we invite experts – immersed in the pursuit of educating their students – to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name, “Perspectives from the Campus”, we invite experts – immersed in the pursuit of educating their students – to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the latest installment of this series, David Dungan, who serves as the executive director at the Center for Security Services and Cyber Defense at Anderson University, discusses job and internship/co-op scams that are targeting college students.
By David Dungan
College students nowadays have grown up with technology and understand common cyber threats. They know how to navigate social media and memes with ease. However, as college students are beginning to find work opportunities, they’re experiencing a new type of scare: internship/co-op and job scams.
Internship/co-op and job scams attempt to defraud students out of money and labor by acting as legitimate employers that are looking to hire new employees. These companies may utilize a variety of schemes, such as asking students for their banking information, to pay money, or to buy equipment for remote work from a specific website. The company may send a student a check to “reimburse” any purchases, only for the check to bounce and the student to lose money.
These internship scams have also been used as a front for human trafficking, encouraging students to travel to a secondary location to perform tasks. Job recruiters will reach out to unsuspecting victims through recruiting websites, such as LinkedIn, wanting to meet for a job interview. The recruiter will then “stall” the victim during the interview asking them seemingly random questions, and while the interview is taking place, the victim’s car is tampered with (presumably to track the victim). Legitimate job recruiter sites remove tens of millions of posts annually that contain scam content from their website to help protect genuine users.
The Federal Trade Commission documented business and job opportunity scams are the fifth most prevalent type of fraud. Workers reported more than 80,000 job scams in 2023 accounting for $277 million in losses.
Job scams target specific types of employment, including nannies/caregivers, virtual personal assistants, mystery shoppers, government and postal job scams, or work from home opportunities such as reselling or reshipping jobs. Scammers may also pose as job placement services.
Among the warning signs students should look out for include:
- The company sends a check and asks you to return the remaining money you did not spend.
- The job recruiter contacts you without prompting or filling out an application.
- The recruiter contacts you through a generic email account instead of a business account.
- The company hires you without a formal interview.
- The job listing is vague and uses phrases such as “No Experience Necessary”, “Work Your Own Hours”, “Work from Home”, or “Earn $1,000 a week”.
- The job listing uses phrases such as “wire transfers”, “PayPal”, “Venmo”, or “money transfers” as a part of the ad.
- The employer pressures you to decide on the job offer quickly.
- Incorrect spelling or grammar in emails and/or job listings.
Some ways to protect yourself against job scams include:
- Look up the name of the company hiring you, using words such as “scam” or “complaint”.
- Contact the company or recruiter directly.
- Ask for the job details, such as duties and pay, in writing.
- Making sure that you don't pay money to the employer for a job, such as supplies or exam fees.
- Looking up the domain of the website and if the website was created recently with a free domain, this could be a red flag as well.
Students should reach out to trusted advisors at the school they're attending or mentors before accepting a job, internship, or co-op, especially if anything about the offer seems to be "too good" to be true. Finding a job or securing an internship or a co-op is a process that's stressful and there are a lot of factors that go into making a decision. Navigating through it all can be tricky. Students are encouraged to use all of the resources that are available -- and your instincts -- to help in recognizing a potential scam by noticing aspects that seem off about a prospective employer or job opportunity.
It's important, too, to remain cautious of scams even in the midst of something as exciting as landing that ideal internship, co-op, or job. The cost of attending school, not to mention all of the expenses that go into moving to another city, state (or even another country) to work for a company as part of an internship or a co-op, isn't cheap; all the more reason to do your homework and take the time to follow a few simple steps whenever you're online to keep your career and education on the right track!
PII Guidebook 2.0: Trusted Resource for Keeping Personal Information Secure (and it’s FREE)
Wednesday, July 3, 2024
Blog topics:
 By Ted Cotterill – Indiana Chief Privacy Officer and Tracy Barnes – State of Indiana Chief Information Officer
By Ted Cotterill – Indiana Chief Privacy Officer and Tracy Barnes – State of Indiana Chief Information Officer
When it comes to being a resource for cybersecurity and specifically, privacy and the responsible use of data, the State of Indiana’s strategy is to provide information that’s free, comes from trusted sources and knowledgeable experts, and most importantly, is accurate.
What’s more, the State’s cybersecurity resources are available to all Hoosiers, businesses, and local government – including our schools – on the Indiana Cyber Hub website. And that includes the newly launched PII Guidebook 2.0.
First developed in 2021 by a subcommittee of the Indiana Executive Council on Cybersecurity (IECC), whose membership is comprised of private and public sector leaders in privacy and cybersecurity, the PII Guidebook has been updated to reflect the rapidly changing regulatory landscape in the space. These updates are now being used by organizations and companies in Indiana to protect the personally identifiable information (PII) and data assets that they leverage as an important part of their day-to-day operations.
 Intended as a free, “how to” resource, the release of this updated guidebook comes at a critical time when more than 52 percent of all data breach incidents in global organizations involved a customer’s PII, making it the most frequently breached type of data.
Intended as a free, “how to” resource, the release of this updated guidebook comes at a critical time when more than 52 percent of all data breach incidents in global organizations involved a customer’s PII, making it the most frequently breached type of data.
Beginning with the definition of the term PII, the guidebook includes a list of sources and definitions, along with a summary of the categories of PII that must be protected. Throughout the guide, there is a great deal of helpful information intended to provide greater context and understanding of privacy, as it can be difficult for small and midsized organizations to maintain that proficiency in-house.
The Subcommittee has also included a section that provides an overview of the “current state of PII,” which encompasses a selection of important privacy developments that have occurred during the last decade, including the adoption of a new article in the Indiana Code concerning consumer data protection that was enacted by the Indiana General Assembly in 2023 and takes effect on January 1, 2026. Looking ahead, there are also a number of “future developments” that are being considered that could impact how sensitive data and, for that matter, our personal information may be protected in the years to come.
In our roles as the State of Indiana’s Chief Privacy Officer and Chief Information Officer, respectively, we are pleased to help share the PII Guidebook 2.0 with all Hoosiers. Indiana is making great strides in cybersecurity, privacy, and responsible data. For more information about the state’s data strategy – including a newly-adopted policy involving artificial intelligence (AI) systems, be sure to visit the website of the Office of the Indiana Chief Data Officer, and for the latest information on all things privacy and cybersecurity, check out the Indiana Cyber Hub website and be sure to take a look at the all-new Indiana Privacy Toolkit.
Protecting someone’s personal information is not always easy, even if you have a lot of resources or the personnel to sort through the regulations and make sense of it all. It’s our hope that the PII Guidebook 2.0 and the Indiana Privacy Toolkit will help Indiana organizations do just that.
AI in the Workplace: Navigating the New Frontier of Cybersecurity
Wednesday, June 26, 2024
Blog topics:
Artificial Intelligence (AI) is revolutionizing how we work, bringing unprecedented efficiency and innovation to businesses across industries. However, just like cryptocurrency in the financial world, AI introduces new cybersecurity challenges we must address. Let's explore the exciting world of AI in the workplace and discuss how we can stay ahead of potential risks.
The AI Revolution in the Workplace
AI is transforming everything from customer service to data analysis, helping businesses make smarter decisions and streamline operations. It's like having a super-smart assistant that never sleeps! But with great power comes great responsibility, and we need to be mindful of the new cybersecurity landscape that AI creates.
New Cybersecurity Risks Posed by AI
- More Sophisticated Phishing Attacks: Like crypto scammers who use ever evolving and sophisticated techniques, cybercriminals leverage AI to create more convincing phishing emails and deepfake voice or video content.
- Data Poisoning: Bad actors might attempt to corrupt the data used to train AI models, leading to biased or malicious outcomes.
- AI Model Theft: Valuable AI models could become targets for intellectual property theft, similar to how crypto wallets are targeted for their digital assets.
- Adversarial Attacks: Cybercriminals might try to manipulate AI systems by feeding them specially crafted input to produce incorrect results.
- Data Privacy Risks: Many popular AI tools store user inputs to improve their models. The AI company could retain or access any sensitive information you enter.
- Intellectual Property Protection: Sharing proprietary information or trade secrets with public AI tools could compromise your company's competitive advantage.
- More Personal Data Security Risk: Inputting personal identifiable information (PII) or confidential data into these systems can lead to PII capture and potential data breaches.
Managing AI Cybersecurity Risk
The good news is that we can proactively protect ourselves and our businesses. Here are some tips to help you navigate the AI cybersecurity landscape:
- Implement Robust AI Governance: Establish clear policies and procedures for AI development, deployment, and use within your organization. This is similar to how crypto investors need to research their investments thoroughly.
- Limit and Enhance Use Cases: Consider using private, on-premises AI solutions for sensitive tasks.
- Enhance Data Security: Protect the data used to train and operate AI systems. Use encryption and secure storage methods, just like you would protect your crypto wallet's private keys.
- Regular Security Audits: Conduct frequent assessments of your AI systems to identify vulnerabilities. Think of it as keeping a close eye on your digital investments.
- Employee Training: Educate your team about AI-related security risks and best practices. As we learn to spot crypto scams, we need to recognize AI-related threats.
- Use AI for Defense: Leverage AI-powered security tools to detect and respond to threats more quickly and effectively.
- Protect Sensitive Information in Generative AI Tools: While generative AI tools like chatbots and content creators can be incredibly useful, it's crucial to be mindful of the information we feed into them
- AI Doesn’t Keep Secrets: Treat AI tools like public spaces. If you wouldn't share the information in a crowded room, don't share it with an AI.
- Collaborate and Share Knowledge: Participate in industry forums and share experiences with peers to stay informed about the latest AI security trends and threats.
The Future is Bright (and can be Secure!)
AI in the workplace introduces new cybersecurity challenges, but it also offers exciting opportunities for innovation and growth. By staying informed and implementing robust security measures, we can harness the power of AI while keeping our digital assets and information safe.
Remember, just as the crypto market has its ups and downs, the world of AI will continue to evolve. Stay curious. Stay vigilant. And embrace the AI revolution with confidence!
Disclosure: AI was used to edit and suggest elaboration for this article. Those suggestions were then vetted and enhanced by the author, following TechPoint AI-use guidelines.
National Selfie Day: Celebrate By Practicing Selfie Safety
Friday, June 21, 2024
Blog topics:
 Selfies have taken the world by storm as a result of the development of smartphones and social media platforms. A whopping 92 million selfies are taken every day; that’s an average of seven minutes per day that we spend taking pictures of ourselves.
Selfies have taken the world by storm as a result of the development of smartphones and social media platforms. A whopping 92 million selfies are taken every day; that’s an average of seven minutes per day that we spend taking pictures of ourselves.
Today, Friday, June 21st, is National Selfie Day and what better way to celebrate by taking a few steps – while snapping those pics – to protect your-selfie from getting taken advantage of by a cybercriminal.
In this digital age, as we know, it’s easier than ever to take, send, and post pictures at any time. And you might ask yourself, "What danger could come from innocently posting pictures of yourself online for your friends to see?". Let’s just say, there’s a few things to keep in mind.
After all, the selfie phenomenon is a fun form of self-expression and way to capture the moment. Seems innocent enough… right? While your intentions may be harmless, scammers are not. They will find any avenue to get to your money, even if that means stealing your identity, and your selfie.
Over the last two years, about one in four people who reported to the Federal Trade Commission (FTC) about losing money to fraud, said the scam started on social media. Over those two years, identity fraud by way of social media, reached $2.7 billion.
It may seem like a strange concept – having your information stolen through the simple act of taking and posting a selfie. That said, it does happen.
Cybercriminals will use information from your social media posts, such as a birthday post, to collect data to steal your identity. Scammers will use the information they’ve gathered from social media to pretend to be you to open credit accounts.
Trying to halt the flood of selfies on social media, or pleading with scammers to change their tactics is like trying to empty the ocean with a teaspoon, but don’t worry! There are some strategies that you can use to protect yourself so that you can post your selfies safely. You can protect yourself against selfie scams by:
- Using different passwords for every social media account.
- Turning off location services.
- Considering what is in the background of your selfies and ensuring that no personally identifiable information is accessible through what’s in the background of your selfies.
- Utilizing privacy settings to help shut out social media scammers from accessing your personal information.
- Turning off automatic location-tagging so as to not expose the general whereabouts of you or your loved ones.
National Selfie Day also involves more than just sharing moments – it’s about safeguarding your privacy and preserving personally identifiable information (PII) from cybercriminals. And be sure to protect your selfie from getting scammed by engaging in these best practices for posting on social media!
Crypto Literacy: What Are Cryptocurrency Scams and How to Avoid Them
Wednesday, June 19, 2024
Blog topics:
 PERSPECTIVES FROM THE CAMPUS
PERSPECTIVES FROM THE CAMPUS
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name, “Perspectives from the Campus”, we invite experts – immersed in the pursuit of educating their students – to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the latest installment of this series, David Dungan, who serves as the executive director at the Center for Security Services and Cyber Defense at Anderson University, delves into the world of cryptocurrency. In addition to offering some helpful information about the types of scams cybercriminals are using when it comes to trying to steal someone’s assets, he discusses a few of the steps they’re using to mislead people when it comes to investing (or spending) the money that’s in their digital wallet.
By David Dungan
It wasn’t that long ago, cryptocurrency seemed to be all the rage; especially when you consider that the value of Bitcoin, in November reached more than $65,000 – before plummeting to $16.189 in less than a year.
Since that time, Bitcoin has regained its value, peaking at $71,631 in early April. But regardless of the peaks and valleys that often comes with almost any type of investment, cryptocurrency fraud has emerged as the “riskiest scam” for consumers, according to a recent report from the Better Business Bureau.
With all of that, it’s understandable to ask questions, such as how secure is cryptocurrency trading, and cryptocurrency?
It’s important to understand, too, what types of scams are out there and what you need to know to protect yourself to avoid being the victim of a cybercrime, in which 80 percent of Americans who were targeted in crypto and investment scams last year lost money. More recently, in February, a 70-year-old woman in California lost $720,000 for what she thought was a legitimate crypto investment.
Some crypto basics to keep in mind:
- Cryptocurrency, also known as digital currency, uses cryptographic functions to store transactions and balances in blockchains, which are shared, fixed records that record and track assets, common for digital payments.
- Cryptographic functions help secure data by encrypting and decrypting data with private and public keys.
- Encryption keeps your data safe by using mathematical models to rearrange the information in a way that only the parties that have the decryption key can rearrange it to access the data. Decryption works by converting an encrypted message to its readable format.
- Cryptocurrency users will use cryptocurrency wallets, or crypto wallets, to store their private encryption keys ,which work like passwords, that proves a user’s ownership of the cryptocurrency. These wallets allow users to exchange their cryptocurrencies.
Some of the more common scams you have seen recently involving cryptocurrency includes:
- Bitcoin Investment Scams -Scammers will pose as seasoned investors and request a fee or access to a victim’s funds.
- Rug Pull Scams - In this type of scam, fraudsters will set up a project and wait for the value of the project to be pumped up before “pulling the rug” and stealing as much of the value as they can.
- Phishing Scams -Phishing involves sending a victim a fake website link that will request personal details, in this case, a crypto wallet and private key.
Fortunately, there are several steps consumers can take to help protect themselves to avoid being a victim of a cryptocurrency scam that include:
- Watching Out for Promises of Huge Returns that claim that they can create huge returns on your crypto investment. Like other investments, crypto is hard to predict and get rich quick schemes are almost always scams.
- Thoroughly Research AI-Generated Investments -Whether you want to invest in a new crypto coin or a non-fungible token (NFT), it is wise to vet all your potential investments. Try to find as much information as possible about the project, or cryptocurrency, you want to invest in. Be sure to ask questions, such as: Who created the project? Are they reputable? Is it open source?
- Always Avoid Clicking on Links from Unknown Senders - To avoid phishing scams, it is important to not click on links if you don’t know the sender. Furthermore, scammers may impersonate people you do know, so double check each email address carefully.
While we certainly cannot predict the cryptocurrency market, we can evaluate the security of cryptocurrency wallets and exchanges as a way to help you protect your identity and keep your investments out of the hands of a cybercriminal!
National Homeownership Month – Celebrate “Home Sweet Home” By Avoiding Cyber Scams
Wednesday, June 12, 2024
Blog topics:
 It’s June! This month isn’t just about warmer weather; it’s also National Homeownership Month, marking one of the busiest times of the year for home purchases.
It’s June! This month isn’t just about warmer weather; it’s also National Homeownership Month, marking one of the busiest times of the year for home purchases.
Yet, it can seem, at times, as though the idea of owning a home has become a seemingly unattainable milestone for some Americans. But not all of it is for the reasons you might think.
Challenging economic factors aside, it doesn’t help that cybercriminals are now targeting the real estate market and prospective home buyers.
Buying a home is a process that, now, can be done digitally -- from start to finish – with the ability to search for homes, tour homes, and then buy a home online. For all of its simplicity, it’s a process that leads to a closing that can still leave some buyers vulnerable, right up to the very moment they’re supposed to get the keys.
Even if some of this is hard to believe, it’s important to protect yourself and your property out of the hands of would-be cyber scammers, who are looking to steal your money. According to the Federal Bureau of Investigation (FBI), in 2023, there were more than 9,500 internet-only real estate complaint cases, amounting to more than $145 million in losses, most of which will never be recovered,
Wire transfer fraud is the most common method that cyber scammers will use to try and defraud you, with real estate closing scams being one of the top five wire fraud schemes. In doing so, hackers will send an email or text message; they might even call you, claiming to be a representative of your title or escrow company and then they’ll ask for money to open your escrow account, tricking you into wiring money straight to the scammer’s bank account.
These bad actors have gotten creative, inventing various ways to steal money from you using a variety of real estate endeavors. They’ll create fake property ads that feature properties at unreasonably low prices, often using stolen pictures and descriptions from legitimate posts to produce listings that look real.
While the thought of being scammed out of a home, and thousands of dollars, is enough to make you forget homeowning altogether- not to fear! There are several steps that you can use to prevent yourself from getting scammed during what’s supposed to be an exciting and celebratory time!
- Don’t click on links or call a phone number sent through email as scammers can hack into email accounts and alter your messages to make it look like the cybercriminal is, actually, your realtor or lending company.
- Create a list of independently confirmed phone numbers for your realtor, lender, and title company, and be sure to use these numbers rather than any numbers that might appear in an unsolicited email.
- Be wary of any communications that intimidates you, or causes you to take any sort of immediate action, as these could be scammers that don’t want you to take any time to think clearly or verify anything.
- If you believe that you have been a victim of a real estate scam, contact your mortgage service provider immediately, and file a complaint with the Federal Trade Commission (FTC).
By being aware of real estate scams and proactively taking just a few steps to follow some helpful cybersecurity tips, a soon-to-be homeowner can help in better protecting themselves against almost any kind of attack on their assets.
And whether you’re a future homeowner, current homeowner, or you’re involved in real estate – you don’t have to be defenseless against fraud. There’s lots of legitimate real estate agents and cyber-friendly resources to help you fulfill your dream of being a homeowner!
Education Without Walls: Expanding Cyber Learning
Thursday, June 6, 2024
Blog topics:
 Today is National Higher Education Day and it’s fitting that we recognize the fact that education – at every level – is undergoing a remarkable transformation, as traditional classroom boundaries are being redefined through the integration of immersive learning.
Today is National Higher Education Day and it’s fitting that we recognize the fact that education – at every level – is undergoing a remarkable transformation, as traditional classroom boundaries are being redefined through the integration of immersive learning.
Through its surge in popularity, students have benefitted greatly from taking their learning “outside the classroom”. In doing so, they’ve been able to enhance their critical thinking skills and gain a greater level of engagement for the career path they’re on.
And now, at a time when careers in cybersecurity and national security are expected to grow at a rate of 20 percent in 2025 (with a median salary of $81,000), there’s a great example of immersive learning that’s occurring right here in Central Indiana.
Uniquely formed as an information security and threat intelligence non-profit organization, Anderson University hosts the Center for Security Studies and Cyber Defense (AUCSSCD). Students from both Anderson University and Ball State University are instilled with a wide range of professional competencies (both hard and soft skills) and the ethical behavior required for working in cyberspace and national defense.
In doing so, they’re able to learn the essential skills that serve the needs of the Center’s real-world clients while, at the same time, enabling the students to build on their experience by providing services that include live threat monitoring through the Center’s Security Operations Center (SOC), cybersecurity audits, and threat intelligence reports.
Working under the close supervision of senior security staff, the students, some of whom serve as paid interns, are afforded opportunities that include:
- Assessing a client's current security posture.
- Providing recommendations for improving their posture, based on a client’s budget and the resources they’ve devoted to security.
- Developing information security roadmaps, including system security plans, vulnerability management plans, incident response plans, as well as security awareness and training programs.
- Presenting key decision makers with accurate, unbiased evaluation (e.g., capabilities, costs, risks) of information security solutions and authored contracts outlining product delivery processes and project closure.
- Writing highly technical publications for use by a variety of businesses and organizations.
Of course, the knowledge that is gained by applying what a student learns in the real world is essential to the learning that goes into earning a bachelor’s degree in cybersecurity or national security studies. The cybersecurity degree is recognized as a National Security Agency (NSA) validated program of study and Anderson University’s degree in national security studies is one of the few undergraduate security studies majors in the country.
As we celebrate the many opportunities that we’re able to achieve that comes from all of the ways we can learn, the fact that it’s happening with careers in cybersecurity is reassuring not just for the students. Because, as we’ve discovered with a lot of things that happen in our world, it makes a difference for all of us, especially as we work on keeping our personal and financial information secure from the countless cyber threats or online scams we deal with on a daily basis. It’s good to know that we’ve got some people who are committed to finding a solution!
CISA Updates Toolkit with Nine New Resources to Promote Public Safety Communications and Cyber Resiliency
Wednesday, June 5, 2024
Blog topics:
Reprinted with the permission of the Cybersecurity and Infrastructure Security Agency (CISA), today’s blog first appeared on CISA’s website on May 13, 2024
The Cybersecurity and Infrastructure Security Agency (CISA) collaborates with public safety, national security, and emergency preparedness communities to enhance seamless and secure communications to keep America safe, secure, and resilient. Any interruption in communications can have a cascading effect, impacting a public safety agency’s ability to deliver critical lifesaving services to the community. Therefore, public safety agencies carefully plan, implement, and review communications capabilities for resiliency to maintain daily communications capabilities and prepare in advance for emergency events.
To assist public safety agencies with navigating the wealth of information available regarding communications resiliency, CISA created the Public Safety Communications and Cyber Resiliency Toolkit to identify and address emergent trends and issues, consolidate resources, educate stakeholders at all levels of government, and propose mitigations to enable resilient public safety communications. The Toolkit is designed to assist public safety agencies and others responsible for communications networks by providing the tools necessary to evaluate current resiliency capabilities, identify ways to improve resiliency, and develop plans for mitigating the effects of potential resiliency threats.
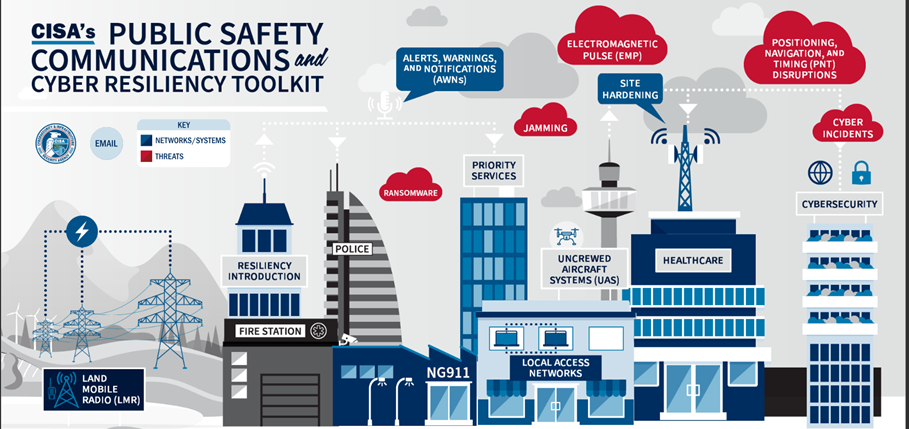 Through the use of an interactive graphic displaying components of the emergency communications ecosystem, Toolkit users can easily navigate through a number of topics and access applicable resources. Current topic areas include:
Through the use of an interactive graphic displaying components of the emergency communications ecosystem, Toolkit users can easily navigate through a number of topics and access applicable resources. Current topic areas include:
- Alerts, Warnings, and Notifications
- Cyber Incidents
- Cybersecurity
- Electromagnetic Pulse (EMP)
- Healthcare
- Jamming
- Land Mobile Radio (LMR)
- Local Access Networks (LAN)
- Next Generation 911 (NG911)
- Positioning, Navigation, and Timing (PNT) Disruptions
- Power
- Priority Services
- Ransomware
- Resiliency Introduction
- Site Hardening
- Unmanned Aircraft Systems (UAS)
As part of CISA’s commitment to provide the most up-to-date information in support of communications and cyber resiliency, the Toolkit is designed to be a living document, with the ability to grow and expand as new resources are developed and identified. Since its last update in March 2024, the Toolkit has been updated to Version 24.1 with nine new resources. Users are encouraged to revisit the Toolkit on a regular basis to take advantage of recently added information and resources. Check out the updates!
Avoiding Elder Scams: A Great Way to Celebrate Older Americans Month
Wednesday, May 29, 2024
Blog topics:
 PERSPECTIVES FROM THE CAMPUS
PERSPECTIVES FROM THE CAMPUS
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name, “Perspectives from the Campus”, we invite experts – immersed in the pursuit of educating their students – to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the latest installment of this series, David Dungan, who serves as the executive director at the Center for Security Services and Cyber Defense at Anderson University, on the occasion of Older Americans Month, shares his perspective regarding some of the cybersecurity scams that are being used to target senior citizens and some of the steps to follow for keeping your (and your family’s) personal and financial information safe and secure.
By David Dungan
At times, technology can seem as through it’s downright notorious for advancing at breakneck speeds.
With the recent developments involving such things as artificial intelligence (AI) and cryptocurrency, as well as all of the new (and emerging) ways in which we’re able to communicate with one another, users are forced to keep up with an ever-growing list of new tools. It can feel as though it’s overwhelming or that you’re going to be left behind. Because of that, malicious actors on the internet assume that older users are more vulnerable, resulting in a massive number of scams targeting individuals above the age of 60.
Malicious actors can also use AI and cryptocurrency to send various types of scams to older Americans. As a result, a recent article in Elder Fraud, in Focus revealed just how much of an impact that’s occurred, such as:
- The average victim of elder fraud lost $33,915 in 2023.
- There were more 101,000 victims reporting elder fraud crime in 2023.
- The costliest cases involved investment scams, with losses totaling more than $1.2 billion to elder victims in 2023.
- In a significant amount of elder fraud cases, cryptocurrency was used to help facilitate the scam.
These numbers clearly demonstrate how much is being taken from older Americans, but they don’t discuss the methods that bad actors are using. An article published by the National Council On Aging (NCOA) discusses what scam methods are the most popular for elder fraud. Some of the most effective methods of scamming include:
- Phone calls from scammers impersonating government officials demanding personal identifying information and/or money.
- Scammers calling an older adult telling them that they have won a lottery or prize, and to claim their winnings they must send a payment.
- Computer tech support scams claiming that it’s necessary for them to make payments or provide their personal information in order to receive help.
Older Americans, as well as their family members and caregivers should be as diligent as possible when using the internet to protect themselves from potential scams. The NCOA discusses tactics to avoid phone scams which includes the following strategies:
- Caller IDs can be spoofed, so make sure you know who you are talking to.
- Do not give out sensitive information over the phone.
- Ask plenty of questions about who they are and why they are calling.
- Ask family and friends if you are confused about a certain process.
If something seems out of place or too good to be true, it likely is, and the best thing you can do is to simply hang up.
The internet is continuing to change rapidly, and threat actors are constantly coming up with all kinds of ways to get your money. Whenever you’re online, be sure to look out for the warning signs of potential scams and take measures to keep yourself safe.
Of course, if you need help, or you believe you’re a victim of identity theft or other type of online crime, the state of Indiana offers a lot of great FREE resources. You can visit the “Report a Cyber Incident” page on the Indiana Cyber Hub website, or the Indiana Attorney General’s office website where you can freeze your credit, sign up on the state’s “Do Not Call” list to avoid robocalls, and more.
All of us, regardless of how old (or young) we are, can feel as though we’re going to be left behind while the digital world around us moves ahead. Yet one of the great things about technology is that you can slow it all down – or stop it altogether – simply by trusting your instincts and taking the time to do some homework on who’s calling, texting, or emailing you. And what better way than that to celebrate getting older!
Empowering Tomorrow's Tech Talent: A Guide to Ivy Tech's IT Toolkits
Wednesday, May 22, 2024
Blog topics:
 PERSPECTIVES FROM THE CAMPUS
PERSPECTIVES FROM THE CAMPUS
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name, “Perspectives from the Campus”, we invite experts – immersed in the pursuit of educating their students – to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the latest installment of this series, Shabbir Qutbuddin, who serves as the Assistant Vice President for the School of IT and Entrepreneurship at Ivy Tech Community College shares the features and benefits of Ivy Tech's IT Toolkits, a comprehensive collection of resources designed to empower students as a gateway for guiding them to a thriving career in the tech industry.
In today’s fast-paced, tech-driven world, starting a career or advancing in the tech industry requires a commitment to continuous learning and access to the right resources.
Understanding and leveraging technology is crucial for academic and career success.
Students with access to resources, such as career pathways, tools, and experiential learning, will likely be better prepared for college and career paths. At the same time, those without might face challenges in postsecondary education and have fewer opportunities for early career exploration. For high school students, a lack of access to educational resources can profoundly affect their long-term academic and career trajectories. To bridge this gap and ensure inclusivity and accessibility, we aim to increase awareness of these resources through career coaching so students may use them more effectively.
Ivy Tech Community College has curated the resources that can help launch or level up a career in tech into IT Toolkits, a comprehensive collection of resources designed to empower high school students, college students, and career changers across Indiana.
These toolkits offer a roadmap through various IT fields, including software development, cybersecurity, cloud technologies, data analytics, computer science, network infrastructure, and IT support. By providing resources and guidance tailored to different learning and professional development stages, these toolkits can be the gateway to a thriving IT career, offering students the tools they need to thrive in the tech industry.
Each toolkit is designed to be user-friendly, serving as a comprehensive guide that can take you from initial curiosity to professional expertise. They enable you to explore educational opportunities, competitions, certifications, programming languages, tools, blogs, forums, projects, volunteering, freelancing, events, professional associations, and jobs. These toolkits are intended to serve as your companion on your educational journey, helping you identify the skills necessary for a successful career in IT in a way that's easy to understand and navigate.
The toolkits assist individuals through academic exploration, continuing education opportunities, and skills enhancement prospects. They share information regarding applied learning options, aid in understanding industry trends, and support career development. Within these toolkits, resources are available to uncover opportunities for earning dual credits, engaging in accelerated learning programs, and pursuing self-directed education. They can help gain a competitive advantage by fostering career readiness, keeping abreast of emerging technologies, and encouraging applied learning. Furthermore, these toolkits are instrumental in expanding professional networks, providing access to expert insights, and assisting with job information.
Ivy Tech is committed to educating and connecting learners to the vast opportunities in the tech landscape. Whether you're a high school student exploring career options, a college student seeking to specialize, or a professional looking to pivot into an IT field, these toolkits will not just help you navigate the complex world of IT but also equip you with the information you need to succeed. Start leveraging these toolkits today and take your first step towards a promising future in technology, where you can shape the digital world with your skills and knowledge.
Help! Something Hurt My ACL (Access Control List)
Wednesday, May 15, 2024
Blog topics:
 PERSPECTIVES FROM THE CAMPUS
PERSPECTIVES FROM THE CAMPUS
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name, “Perspectives from the Campus”, we invite experts – immersed in the pursuit of educating their students – to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the latest installment of this series, David Dungan, who serves as the executive director at the Center for Security Services and Cyber Defense at Anderson University, discusses the significance of access control lists and how these rules help shape a company’s cyberstrategy and IT systems.
By David Dungan
When it comes to hearing about someone’s ACL, the reference, unfortunately, often refers to an athlete, whose season has just ended because they’ve torn their ACL (Anterior Cruciate Ligament).
It’s a devastating injury that requires, on average, around nine months to heal before they’re back in the game.
For a network administrator, the term “ACL” refers to Access Control Lists, that are the lists of rules that determine who can access what in a computer network. A properly configured ACL can save network administrators a lot of time and effort later by protecting against all kinds of unauthorized access and threats.
Network administrators often configure ACLs for switches, routers, and VPNs (virtual private networks), as well as a variety of systems, devices, and even files!
Many devices, such as Chromebooks, already have ACLs configured. However, if one is not yet configured, network administrators can set up their own ACL as an allowlist or a blocklist. In other words, the access control list can either explicitly deny (and implicitly allow) or explicitly allow (and implicitly deny) access. In other words, it enables them to keep a lid on things when it comes to keeping their network secure.
- Explicit denial means that a network administrator would have to list any IP addresses, protocols, and/or credentials they would not want to access a potential resource.
- On a switch, this rule may look like “deny tcp 192.168.5.0 0.0.0.0.255 eq telnet” if their intention is to deny a protocol.
- They may also input into their system “deny 192.168.5.0 0.0.0.0 10.250.0.0 0.0.0.255” if their intention is to deny a range of IP addresses.
Conversely, implicit denial (and explicit allow) means that a system administrator would need to manually input IP addresses, protocols, or any other users that would like to allow access to their resources. These lists likely have “Deny IP any any” or something similar.
Of course, not unlike the running back or lineman, who wants to stay on the field and avoid a hit that could cause an injury, network administrators should keep in mind the following best practices when implementing access control lists, including:
- Utilizing “implicit deny” whenever possible to block unknowns.
- Being specific when denying certain protocols and IP addresses.
- Making sure to block insecure protocols such as Telnet, POP3, SNMP versions 1 and 2, etc.
- Enabling alerts for ACL configuration changes to protect against unauthorized changes.
- Adding comments on changes to understand why these changes were made later on.
- Enabling logs for changes for auditing.
- Applying specific rules at the top (ex. “Deny TCP 10.4.8.0 0.0.0”) and generalized ones at the bottom (ex. “Deny ip any any”).
- Applying rules for:
- groups, if possible, to streamline access control.
- both inbound and outbound ACLs to protect against both inbound and outbound.
- Applying the ACLs close to where the network traffic is coming from.
While this list is not intended to be exhaustive or all-inclusive, implementing best practices gives network administrators an idea for configuring their ACLs and applying policies to ensure the protection of their networks. Network administrators should also follow device vendor instructions and advice when configuring these devices, as the vendors who have designed the network equipment have developed the best practices to keep it secure, and often include step-by-step instructions for configuring these ACLs.
In following these steps, there are several key benefits to access control security, such as:
- Enhanced security.
- Increased operational efficiency.
- Addressing compliance requirements.
- Customized access.
- Audit trails.
- Integration with other security tools.
Access control lists enable organizations to protect their sensitive information from unauthorized access. In today’s cyber-vulnerable world, it can be considered the most basic, yet crucial component of a comprehensive cybersecurity strategy and help your team stay in the game more securely.
Toolkit Offers Great, New “Handbook” for Better Understanding How Privacy “Works”
Wednesday, May 8, 2024
Blog topics:
 By Tracy Barnes
By Tracy Barnes
Whether you work in local government, a non-profit organization, or you’re a small business owner, there’s a lot of responsibility that goes into protecting the privacy of someone’s personal and financial information.
And, beyond the challenge that comes with protecting it, there’s quite a bit to try and understand – at any given moment – just how privacy “works” and why that’s important. Safe to say, it can feel a little overwhelming, especially when you consider what it’s worth – to a cybercriminal.
- According to a recent report, a cybercriminal could purchase your entire online identity for approximately $1,170; a “package” that would include a basic proof of identity, credit and debit card accounts, online banking information, and logins for everything from your bank and social media accounts to your store rewards cards, as well as your contact information.
The good news is, there’s a new online resource that’s not only FREE to download, but it’ll also help you better understand privacy in a way that makes sense for you and your organization.
Developed using the knowledge and expertise of leaders in privacy and cybersecurity – from the public and private sectors – the Indiana Privacy Toolkitprovides apractical resource that includes a step-by-step guide with information that’s tailored to fit your specific needs. The recently released toolkit was compiled by the Indiana Executive Council on Cybersecurity’s Privacy Working Group, and it’s available now with just a click, or visit the Indiana Cyber Hub website.
In addition to sharing with you a little bit of information about the history of privacy and what you need to know to get started, the Toolkit includes a seven-step process (and you can start wherever you like) to help guide you. You’ll find everything from the basics and what you need to understand for developing (both) a privacy notice and a privacy policy to the steps for when (not if) the worst happens, along with a strategy to make certain everyone understands you’ve got the situation under control. Think of it as your own, in-house privacy handbook.
As the Chief Information Officer for the State of Indiana and the chair of the Privacy Working Group, I’m pleased and proud to make this resource available, as we recognize the fact that the potential for a cyber incident is continuing to change the way we do business for all of us.
And, it is through these daily interactions, whether the task is a local resident paying their utility bill, a charity working to preserve the identity of their donors, or a small business securely providing payment to a vendor, privacy is a key component for making it all work seamlessly while, at the same time, allowing you and your organization more of an opportunity to focus on serving the people in your community.
Small Business and Cybersecurity: Paired Together, It Benefits All of Us
Tuesday, April 30, 2024
Blog topics:
 One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name "Perspectives from the Campus Series”, we invite experts -- immersed in the pursuit of educating their students -- to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name "Perspectives from the Campus Series”, we invite experts -- immersed in the pursuit of educating their students -- to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the latest installment of this series, David Dungan, who serves as the Executive Director at the Center for Security Services and Cyber Defense at Anderson University, joins in the celebration of National Small Business Week and discusses why it’s important for small- and medium-sized businesses to be able to access affordable – including free – resources to cybersecurity and highlights why it benefits all of us.
By David Dungan
When it comes to protecting our critical infrastructure, the conversation, appropriately, is focused on such things as our water and wastewater systems and electric power grids.
And without question, keeping these resources secure and protected from cyberattacks is a monumentally important priority for our nation, our state, and the communities where we live, work and play.
That said, there is another part of our community that would benefit from the opportunity of gaining a greater level of access to affordable – including free – cybersecurity resources that can be summed up in two words – small business.
It’s National Small Business Week, and whether your definition of a small business is the “mom and pop” accountant, who’s done your taxes for years, or it’s medium-sized company that’s growing rapidly, small to medium-sized businesses (SMBs) are one of the most essential parts of the American economy today, and it’s pretty big deal in the Hoosier State, consider:
- SMBs account for 43.5 percent of the United States GDPand they employ 61.7 million Americans.
- In Indiana, there are nearly 500,000 small businesses that employ 1.2 million people; a figure that accounts for nearly 45 percent of all employees statewide.
Yet, for all of the opportunities that exist out there, the average impact of a data breach on an organization with fewer than 500 employees – according to IBM’s 2023 Cost of a Data Breach Report – is $3.31 million; the average cost for every record that’s breached is $164.
And it doesn’t stop there, with the indirect costs that come from the disruption to the business itself and downtime, a (potential) loss in customers, not to mention the damage that can occur, as it involves a company’s reputation, credibility, or brand.
Fortunately, thanks to the important work that’s been done by various government agencies – at both the federal and state level – a variety of helpful resources, tips, and best practices have emerged to help SMBs better protect themselves while, at the same time, rely on solutions they can use to mitigate potential threats and, if the worse case scenario happens, they can have a plan in place to recover. What’s more, these solutions have been tailored in a way to fit the average SMB budget, including:
- The Center for Internet Security (CIS) offers 20 recommended controls, which act as a set of recommended guidelines on how an organization can secure their cyberspace.
- The Cybersecurity and Infrastructure Security Agency (CISA) offer its cyber guidance for small businesses and it also provides free cybersecurity training and exercise resources as a solution for help small business owners establish effective and practical mechanisms, identify lessons learned, as well as highlight areas for improvements in plans and procedures.
- The Federal Trade Commission also has developed a collection of cyber guides and resources that have been designed expressly for SMBs.
Here in Indiana, some of the programs and solutions, specific to cybersecurity, are right in the name, and all the resources are FREE-to-download on the Indiana Cyber Hub website, including:
- The GCA Cybersecurity Toolkit is a no-cost resource for small business owners as they improve their security. Available from the Indiana Small Business Development Center (ISBDC), it allows you to select from a wide range of tools to find the resources that best fit you and your business' needs.
- The Cyber Insurance Toolkit is intended to help businesses and organizations understand what cyber liability insurance is, what it covers and why it's become an increasingly important part of a company's risk management strategy.
- Drawing on the knowledge and expertise of insurance professionals and members of the legal profession, the Toolkit features a wealth of information from trusted sources -- everything from the types of questions to consider asking as part of an underwriting document to understanding how you can implement reasonable security controls (without spending a great deal of money) while, at the same time, exercising due diligence.
As a small business owner, it’s easy to feel as though the “one thing” (at any given moment) you’re trying to do to help your business grow is just out of reach. That’s why it’s important to keep in mind that when it comes to cybersecurity, it doesn’t mean you have to be defenseless, as there is a great deal of information (a lot of it free…) to help you stay better protected. It’s a win-win for all of us!
Securing our Supply Chains: Safeguarding National Resilience
Wednesday, April 24, 2024
Blog topics:
 PERSPECTIVES FROM THE CAMPUS
PERSPECTIVES FROM THE CAMPUS
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name "Perspectives from the Campus Series”, we invite experts -- immersed in the pursuit of educating their students -- to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the latest installment of this series, David Dungan, who serves as the Executive Director at the Center for Security Services and Cyber Defense at Anderson University, shares some important information regarding the significance of our supply chain. As we celebrate National Supply Chain Integrity Month in April and National Supply Chain Day, Dungan provides his perspective on why cybersecurity is critical for making sure businesses stay protected and the supply chain is secure.
By David Dungan
When it comes to cybercriminals taking aim at a critical sector of our economy, there are few bigger targets than our supply chain.
And whether you’re talking about the massive docks that operate as maritime superhighways to deliver products and goods across the country and around the world, or those that rely on what is known as the Information and Communications Technology (ICT) supply chain, it can impact our entire life cycle; encompassing everything from our hardware, software and managed services to the people, whose livelihoods rely on the efficiency and security of its operations.
April is National Supply Chain Integrity Month and April 29th is National Supply Chain Day, and it’s a good opportunity to understand just how vast our systems reach and what we can do to help make sure it stays secure and protected.
In the modern era of the internet, the number of IoT devices has exponentially expanded, as has the amount of threat vectors. In fact, it’s estimated that the number of active IoT devices globally will reach 24.1 billion by 2030. An example of what we’re talking about can be found right in our own home, while watching TV.
Adding a smart TV to your local network at home adds another vector where, if not properly secured, could expose your network to a threat actor. The same principle applies to businesses, as the more entities are involved with a business, the risk for a cyber incident or cyberattack increases.
Some of the most common sources of supply chain attacks involve commercial software, open-source supply chains, and foreign products. And, just within the last year, there has been a notable surge in these types of attacks involving numerous vendors; a concerning trend that underscores the need for more robust security measures.
Among the resources that are available and are free to download includes the “Best Practices in Cyber Supply Chain Risk Management” from the National Institute of Standards and Technology (NIST) and a free cybersecurity guide from the National Motor Freight Traffic Association (NMFTA).
That said, it’s a challenge to ensure that every step in a business's supply chain is completely secure, especially when you consider the sheer number of levels that exist within the supply chain in the modern era. Nonetheless, there are several measures that can be taken to help mitigate potential cyber threats.
- Fully understand supply chain management risks and threats.
- The necessary personnel should take time to understand the current threat landscape, not just for their own business, but for industry partners within their supply chain.
- Assess your cybersecurity measures.
- After taking the time to understand all current threats in the landscape, the cybersecurity team should install the necessary hardware and software protocols to counter assessed threats, as much your budgets and operations will allow you to do.
- Treat cybersecurity as an ongoing process.
○ Cybersecurity is a never-ending race; at times, it can seem as though it’s a marathon without a finish line. With the rate of change always accelerating, companies need to routinely schedule and reevaluate their own defenses. The average cost of a supply chain related attack is $4.45 million dollars. Even for a small business, the average cost of a breach is estimated at $25,000.
By prioritizing cybersecurity measures and adopting a proactive approach to risk management, a business is better able to protect themselves against attacks in their supply chain. Not only does it help safeguard their own operations, it allows them to contribute to the very economic environment, in which they compete in.
Telecommunicators Possess Sprinter’s Mindset to Relay Life Saving Information to First Responders, 911 Callers
Wednesday, April 17, 2024
Blog topics:
 With the Olympic Games just around the corner, there’s a fitting analogy to be made when it comes to just how important, crucial, really, that the role of public safety telecommunicators and dispatchers provide in responding to an emergency.
With the Olympic Games just around the corner, there’s a fitting analogy to be made when it comes to just how important, crucial, really, that the role of public safety telecommunicators and dispatchers provide in responding to an emergency.
Because if you’ve ever watched one of the relay races, in which a team of four (very fast) men and women compete against one another to win, the importance of the first runner is significant for the fact that they need a much more explosive takeoff than the others since they’re leg begins by standing still.
And that’s not unlike the public safety telecommunicators and dispatchers, who must respond so quickly with every 911 call or text from someone who’s in distress. It’s in that moment, they’re expected to get off to a fast start, effectively manage the situation and obtain the essential information – before they hand off the proverbial baton, so to speak, and relay it all to emergency medical service providers, firefighters, law enforcement officers and others. Telecommunicators also give important instructions to callers to help save lives.
To honor their vital contributions, we celebrate National Public Safety Telecommunicators Week, at this time of year. Here in Indiana, Gov. Eric J. Holcomb proclaimed the third week of April 2024 as Public Safety Telecommunicator Week in Indiana and the Indiana Department of Homeland Security and IDHS Executive Director Joel Thacker encourages public safety agencies and residents statewide to recognize the important work these professionals do and to share appreciation for them.
At a time when digital technology and cybersecurity is more important than ever, in keeping these systems secure and protected, including our 911 centers across Indiana – and throughout the country -- the work of these professionals is continuing at a rapid pace in an ever-changing, you-can’t-always-predict-what’s-going-to-happen-next routine.
In response, public safety agencies possess the ability to rely on practical solutions, including four steps to help mitigate potential threats. And, through the state, there are a wealth of recently updated, free-to-download resources, including the Indiana Emergency Manager Cybersecurity Toolkit 2.0 that features a wide range of best practices and detailed plan templates, as well as an Emergency Manager Cyber Situational Awareness Guide and a Cybersecurity Training and Exercise Guide. All of these materials are ideal tools for helping an emergency manager to begin conversations with their team and even their partners to arrive at solutions that make sense as simply and directly as the complexity of the effort allows.
Nationally, there are more than 90,000 public safety telecommunicators in the U.S., answering more than 240 million calls to 911 each year, and, in Indiana, there are more than 2,000 telecommunicators on the job, protecting Hoosiers every day.
As we salute their tireless efforts, you can visit the Telecommunicators Week page on the Indiana Department of Homeland Security website and read just a few stories highlighting their efforts, as recognized by the Indiana Statewide 911 Board in 2023.
It’s safe to say, as evidenced by their actions, and those who serve, that their quick response, is something that’s deserving of a podium finish, knowing that another race awaits!
CYBERSECURITY: A PEOPLE PROBLEM WE CAN SOLVE
Wednesday, April 10, 2024
Blog topics:
 When it comes to someone suggesting that cybersecurity is a “people problem”, one of the things that came to mind is a recurring bit – known as the “Mr. Obvious Show” that airs on “The Bob and Tom Show”, a nationally-syndicated morning radio program.
When it comes to someone suggesting that cybersecurity is a “people problem”, one of the things that came to mind is a recurring bit – known as the “Mr. Obvious Show” that airs on “The Bob and Tom Show”, a nationally-syndicated morning radio program.
The “long time listener, first time caller” always ends up acknowledging that he “didn’t make the connection”, as Mr. Obvious hilariously expresses, all at once, his amazement/frustration with the situation. It’s an example of the fact that sometimes it’s OK to add a little bit of humor to help us accept the fact that some situations just aren’t as deep as we might think to overcome and that the answer is right in front of us.
All kidding aside, cybersecurity is a people problem; we still act surprised, at times, that we accidently clicked on the wrong link or, worse, we allowed ourselves to be convinced it was OK to authorize a payment to a trusted vendor, only to discover later that our company just fell victim to a business email compromise. On top of that, according to the 2023 ISC2 Cybersecurity Workforce Study, there are a couple of things we need to keep in mind:
- The global cybersecurity workforce continues to grow. We’re up to 5.5 million people who work in cyber, an increase of nine percent since 2022, yet the gap we need to fill grew by 13 percent. Because of that, it means that in 2023, we needed four million – more – cybersecurity professionals to reach what is defined as “full capacity”.
- As all of this is happening, 75 percent of the professionals, surveyed in the report, said the current threat landscape is the most challenging it’s been in the past five years.
Of course, there’s a lot of things we can (and should) do, but one of the options that’s available is to continue expanding the field of job candidates by including and hiring (even) more people, who are neurodivergent.
One of the things we’re learning, coming out of the pandemic, is that we’ve dramatically redefined what we think about when it comes to working a job in a “typical office culture”. In that sense, working remotely is just the tip of the proverbial iceberg.
Moreover, as noted in a 2022 article in The Wall Street Journal, “people who are neurodivergent offer key talents and skills to enhance America’s workplaces.” This is especially true in the cybersecurity sector, with people whose traits, such as hyperfocus, precision, persistence and the ability to identify patterns, can make for an especially good fit.
April is National Autism Acceptance Month, yet neurodiversity also includes people, who’ve been diagnosed with conditions ranging from Attention-deficit hyperactivity disorder (ADHD), Dyslexia, mental health conditions, such as bipolar disorder to social anxiety, Tourette syndrome and Williams syndrome.
The fact is, companies that have successful neurodiversity workforce programs have changed the way they recruit, interview, hire, and manage their employees. In doing so, they’ve followed four steps, including:
- Placing more emphasis on performance than on communications.
- Providing opportunities for employees to work and express themselves in different ways, not always adhering to one cultural norm.
- Encouraging managers to foster clear guidelines and expectations, with meeting agendas prepared in advance and meetings documented clearly afterwards, so that nothing that gets missed or misinterpreted.
- Doing work in teams where each person can work to their strengths, contributing where they are best suited, and relying on others for areas where they struggle.
As a result, companies are discovering that the accommodations they’ve made are right in line with what all their employees view as good management practices.
As more people, who are neurodivergent are provided the opportunity to pursue a career in cybersecurity, we’ll achieve even greater progress with getting ahead of the cyber incidents and cyberattacks that are out there. And with it, more of us can end the call -- we’re making to our cyber, IT and information security staff – that we’ve made the connection and the Mr. Obvious in all of us will be a little happier!
World Backup Day – It’s Something We Can All Celebrate
Thursday, March 28, 2024
Blog topics:
 PERSPECTIVES FROM THE CAMPUS
PERSPECTIVES FROM THE CAMPUS
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name, “Perspectives from the Campus”, we invite experts – immersed in the pursuit of educating their students – to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the latest installment of this series, David Dungan, who serves as the executive director at the Center for Security Services and Cyber Defense at Anderson University, joins in the celebration of World Backup Day and shares his perspective on the importance of backing up our data, whether it’s on our mobile devices or laptops, and reminds us that it’s easy to do (even when we’re at our busiest).
By David Dungan
This Sunday, March 31st is World Backup Day.
It’s one of those special, not-so-official (yet fun) “days” that we’re able to commemorate by doing something that’s actually has a purpose and helps all of us.
Originated in 2011 by a Reddit group to highlight the importance of establishing a virtual sustainability policy and protecting data through the creation of safe backups, it’s become a practice that we need to follow every day. And, that is true, whether you are a small business owner dealing with customers PII (personally identifiable information) or a non-tech, savvy individual with a personal computer
In this incredibly data driven world we live in; it is essential to secure the data which defines our lives. As the amount of essential data increases, the attack surface for virtual threat actors increases proportionally. Both users and companies need strong data backups, despite making use of different kinds of data. Having redundant copies of data also protects against human error in computing, hardware failure, virus attacks, power failures, and natural disasters.
In the current day business climate, data drives nearly every action taken in the workplace to help a firm operate efficiently and effectively. Despite our relatively new dependance on data, businesses around the globe don’t always go to the necessary lengths to protect the data driving so much of the business world. While committing resources to having a redundant copy of data does not itself yield a profit for the business, the lack of it can cost the company exponentially more in a potential cybersecurity attack.
While businesses undoubtedly have much to risk in terms of data loss, individual citizens are also susceptible to risks that are (often) easily solved by backups. For example, an individual could lose their personal device and not be able to recover important data such as photographs and contacts; items that could be easily restored with a backup created in the cloud or by using an external hard drive.
While it is challenging to fathom the notion that any individual, much less any company, could fall victim to data loss; the wide amount of threat vectors combined with the large potential risk posed by the lack of data highlights the incredible need to have a reserve copy of data for both businesses and individuals alike. If proactive measures are taken to create data backups via cloud storage, external hard drives, or through other means, users are able to mitigate the potentially devastating effects of data loss and ensure the continuity of our lives.
And that right there is a reason to celebrate!
Cybersecurity Plan Allows Hoosiers’ Eyes to Focus on Solar Eclipse
Wednesday, March 27, 2024
Blog topics:
By Joel Thacker
 When it comes to experiencing the Total Solar Eclipse on Monday, April 8th (FYI – it’ll be one you won’t want to miss, considering the next one is coming on September 14, 2099), it’s understandable that most of our collective attention will be on the skies as we are plunged into roughly 230 seconds of late afternoon darkness.
When it comes to experiencing the Total Solar Eclipse on Monday, April 8th (FYI – it’ll be one you won’t want to miss, considering the next one is coming on September 14, 2099), it’s understandable that most of our collective attention will be on the skies as we are plunged into roughly 230 seconds of late afternoon darkness.
Yet while all of that happens, it’s important to keep in mind that there are plans that have already been formed to make sure what’s happening on the ground – with our critical infrastructure – that will make it seem as though it’s just another (albeit memorable) Spring day in Indiana.
If you wonder why that’s important, hundreds of thousands of people are expected to visit the Hoosier State to get a better look at the eclipse. More than 3.5 million Hoosiers live in the path of totality.
In fact, according to a recent story in Forbes, data from GreatAmericanEclipse.com, as many as 581,000 people could drive into its path through Indiana, making it the second-busiest state on eclipse day – after Texas. After all, Indiana is also the final place where it’s possible that four minutes of the solar eclipse totality will occur.
That’s why public safety professionals from the Indiana Department of Homeland Security (IDHS), together with a large group of our state partners, as well as officials from communities, large and small, have formed a strategic plan to ensure that everyone is able to travel safely in and out of wherever they go. Counterparts in other states have also been helpful in understanding the magnitude of this event.
At the same time, Indiana’s plan is designed to help ensure cybercriminals aren’t able to distract us with any sort of cyber incidents, especially as it regards our local governments, businesses and schools. In doing so, Indiana is treating this as a three-day event, rather than three-and-a-half minute activity, so as to be fully prepared to help ensure that everyone’s experience is achieved safely.
Just as the IDHS plans for and responds to natural disasters and emergencies, during the eclipse, the state will operate its emergency operations center, observing the event as it takes place and being prepared to assist when needed. Additionally, the work that’s being done ahead of time covered everything from communications and operations, education and the public’s safety and health to logistics and resources, as well as the transportation, viewing, lodging and local support that would be necessary.
As part of that strategy and planning, the state worked closely with numerous utilities, large and small, in communities from across Indiana, as well as energy companies and mobile phone providers, to pull it all together. The state also hosted a series of “eclipse coffee talks” that made it possible for emergency management directors to discuss a range of topics and share solutions.
 The Indiana planning resource, eclipse2024.in.gov, is a great tool to help everyone understand where and how to enjoy the eclipse, including the importance of proper eyewear and the challenges that some of our cities and towns could experience during the course of it all.
The Indiana planning resource, eclipse2024.in.gov, is a great tool to help everyone understand where and how to enjoy the eclipse, including the importance of proper eyewear and the challenges that some of our cities and towns could experience during the course of it all.
IDHS is one of the agencies whose job description is defined as looking out for the well-being of all Hoosiers. It is an around-the-clock responsibility that public safety personnel proudly embrace. IDHS has led planning efforts for this event for more than year to learn from other states that have experienced an eclipse event and prepare manpower and resources.
If you work in public safety and need help planning for the April 8 event, the state also offers a tool to help your efforts by downloading the Indiana 2024 Total Solar Eclipse Special Event Planning Guide.
Whether you’re at home, at work, at school, or with your family, or you’re visiting our state for the eclipse, we hope your experience is safe and memorable!
Small Business in Indiana is a Big Deal
Wednesday, March 20, 2024
Blog topics:
 When it comes to hearing about a statistic or a fact related to something we (thought) we already knew about a particular subject, it shouldn’t come as much of a surprise, right?
When it comes to hearing about a statistic or a fact related to something we (thought) we already knew about a particular subject, it shouldn’t come as much of a surprise, right?
After all, we live in a digital world, in which information comes to us in every conceivable form. And because of that, you might say we’ve become accustomed to having all kinds of details suddenly grab our attention at any given moment. That being the case, what in the world of “getting to a point” are we talking about? OK, fair enough.
Did you know that 99.4 percent of the businesses in Indiana are small businesses, who are responsible for providing employment for more than 1.2 million Hoosiers?
That’s important for a couple of reasons.
Today is the 8th annual National Small Business Development Centers (SBDC) Day – recognizing the work of nearly 1,000 SBDCs across the country (including here in Indiana), who are supporting entrepreneurs in the pursuit of small business ownership. This year’s theme is “Nurturing Dreams, Growing Futures”.
The Indiana Small Business Development Center, housed within the Indiana Economic Development Corporation (IEDC), helps small businesses start, grow, finance, innovate, and transition through no-cost, confidential business advising and training. Established in 1985, it has worked with more than 50,000 entrepreneurs and small businesses. The Indiana SBDC is comprised of a network of 10 regional offices located across the state.
Among its key programs is one focused on cybersecurity. For a small business owner, understanding the kinds of vulnerability that’s out there and mitigating cyber threats are, often, some of the biggest challenges on a day in and day out basis.
In partnership with the Global Cyber Alliance, the Cybersecurity Toolkit contains critical resources designed to protect a small business and everyone they serve, including their customers and employees.
The Toolkit features six cybersecurity tools that can be tailored to best fit the needs of a small business including:
- Know What You Have – Devices and Applications
- Update Your Defenses – Updates, Patches and Vulnerability Management
- Beyond Simple Passwords – Passwords and Two-Factor Authentication
- Prevent Phishing and Malware – DNS Filters, Anti-Virus and Ad-Blockers
- Backup and Recover – System Backups
- Protect Your Email and Reputation – Email Authentication and Brand Monitoring
Another important component of the Toolkit are the cybersecurity resources that are available, ranging from the Indiana SBDC, Data Assured Toolkit (in partnership with the Delaware SBDC) and the Indiana Procurement Technical Assistance Center (PTAC) to the Purdue University Manufacturing Extension Partnership (MEP), an additional partnership between the Indiana PTAC and Purdue MEP, and Purdue cyberTAP.
Together with Indiana’s reputation as a top-tier state for cyber governance, small businesses, as well as local government and schools – all of whom have been impacted by cyber incidents and cyberattacks, are able to benefit from the wealth of free resources, effective tools and organizations dedicated to helping all Hoosiers continue to build on their awareness for all things cyber.
Adding to the celebration is the cyber guidance for small businesses available from the Cybersecurity Infrastructure and Security Agency (CISA) that examines everything from the role of the CEO and the security program manager to the IT Lead for achieving the highest security posture. Also available is the U.S. Small Business Administration’s (SBA) best practices for preventing cyberattacks and some helpful information that's available from the Federal Communications Commission.
It all adds up to creating an environment for a business to grow while, at the same time, not having to start from scratch when it comes to seeking advice as it relates to cybersecurity; something that’s changing even as we discuss it.
What's in a Credit Score? Plenty
Wednesday, March 13, 2024
Blog topics:
 If you’ve seen any of the commercials highlighting the importance of your credit score (including how you can improve it), chances are you’ve had that conversation with yourself, a spouse or significant other, or maybe even your kids (as teens or young adults) – about what’s involved with those three-digit scores on your credit report.
If you’ve seen any of the commercials highlighting the importance of your credit score (including how you can improve it), chances are you’ve had that conversation with yourself, a spouse or significant other, or maybe even your kids (as teens or young adults) – about what’s involved with those three-digit scores on your credit report.
The fact is, understanding (at any given moment) what is happening with your credit score and how it’s calculated isn’t always easy to explain. It’s a little like expecting someone to know “off the top of their head” the formula that major league baseball uses to figure out a player's slugging percentage.
Fortunately, March is National Credit Education Month and that makes it a good time to share some information about the steps you can take to protect yourself from cybercriminals when it comes to your credit report and your credit score, as well as all of the personal and financial data that goes into it.
A few quick facts to keep in mind:
- Credit reports are a detailed history of your credit use. The data in them is used to calculate your 3-digit credit scores.
- Having good credit makes it easier for us to do everything from buying a home or car or renting an apartment to signing up for a cell phone plan or getting a student loan.
- There are five major components that FICO uses in an equation to produce your credit score.
- The accuracy of your credit score is also important, as more than 90 percent of home and auto insurers use credit ratings to decide who to cover and what premiums they charge.
Of course, as it is with a lot of things, cybercriminals try and use a variety of scams to steal your identity along with your good credit. One of the methods they use is known as a “credit repair” scam.
It’s important to keep in mind that there are a lot of reputable agencies and organizations that offer credit counseling services. You can ask them for free information about their services it can provide you and they’ll do it without requiring you to provide any details about your situation.
A “credit repair” company will start out by asking you to pay them upfront, even before they’ve provided you with any services. If you see an ad or receive an offer for someone to repair or “fix” your credit, there are several warning signs if the company:
- Pressures you to pay up-front fees.
- Requests you to dispute accurate information in your credit report.
- Refuses or avoids explaining your rights to you.
- Tells you to not contact any of the nationwide credit reporting companies directly.
Credit repair companies are subject to numerous federal laws, including the Credit Repair Organizations Act and often the Telemarketing Sales Rule, both of which forbid credit repair organizations from using deceptive practices and from accepting up-front fees. These laws prohibit many deceptive practices by credit repair organizations.
Instead, a better approach to managing your credit online is to proactively follow just a few steps with your own cybersecurity to help you stay better protected, including:
- Turn on two-factor authentication whenever possible.
- Change your passwords often.
- Consider using a password manager.
- Consider signing up for identity theft protection.
- Consider using credit freezes or fraud alerts.
Building and maintaining a good credit history is hard work and there’s no easy solutions or a “quick fix” to improving your credit score.
But, if you think about it, you can celebrate National Credit Protection Month and (soon) Opening Day of the baseball season by being a lot like that major leaguer, in that, you’re ready to go. You’re not swinging at any bad pitches or you’re throwing your best pitch to strike out every batter that comes to the plate!
#SlamtheScam, Celebrate National Consumer Protection Week
Wednesday, March 6, 2024
Blog topics:
 Whether you’re trying to improve your credit, shop for a used car, or keep your kids safe online, #cybercriminals seem to have a knack for trying to run some sort of scam for whatever it is we’re trying to do.
Whether you’re trying to improve your credit, shop for a used car, or keep your kids safe online, #cybercriminals seem to have a knack for trying to run some sort of scam for whatever it is we’re trying to do.
Here in Indiana, in 2023, according to the Federal Trade Commission (FTC) Consumer Sentinel Network, there were nearly 70,000 reports of fraud, totaling a loss of $92.4 million. That’s enough, some days, to discourage even the most tech-savvy among us, to question what we can do, collectively, to protect ourselves.
In a campaign that began on Sunday, it’s National Consumer Protection Week; it’s a time – each year – when agencies and organizations at the federal, state, and local government levels join together with consumer protection groups to share information 1) about the rights we have as consumers and 2) to help all of us to improve (even more) our ability to spot, report, and avoid these types of scams.
This year’s theme is #SlamtheScam. And, while it’s true that we might not have to deliver the kind of hits you’d see on a Sunday afternoon in the NFL to stop a cybercriminal from stealing our identity, there are some steps you can take to stay upright (as those announcers would say) and avoid being taken down for a big loss that includes:
- Protecting documents that contain personal information (and keeping it all in a secure place).
- Always asking questions before giving out your Social Security number.
- Maintaining a high level of protection by using strong passwords and multi-factor authentication
- Making sure you NOT give your personal (or financial) information to someone who calls, emails, or sends you a text message, as it could be a cybercriminal trying to steal your identity.
- If you answer and it’s not who you expected, don’t hang on, hang up!
On this website, our State of Indiana Cyber Hub, you’ll find a great deal of resources and services, as well as best practices and tips for people of all ages, including for parents/families, students, businesses, and local government (including our schools). The Indiana Attorney General’s office is also a great resource for protecting your identity for everything from freezing your credit and avoiding robocalls to information on what causes a security breach to occur and what you need to know if that breach has impacted your personal information.
Of course, amid all the celebration, if you think that your organization has been impacted by a cyber incident or cyberattack or you’re an individual who is a victim or identity theft, be sure to visit the Report a Cyber Incident page on the Indiana Cyber Hub website and you’ll find all of the steps you’ll need to report the cybercrime. In doing so, you’ll help others avoid getting sacked!
CISA and EPA Collaborate on Water and Wastewater Sector Cyber Resources
Wednesday, February 28, 2024
Blog topics:
 Reprinted with the permission of the Cybersecurity and Infrastructure Security Agency (CISA), today’s blog first appeared on CISA’s website in a news release distributed on February 7, 2024.
Reprinted with the permission of the Cybersecurity and Infrastructure Security Agency (CISA), today’s blog first appeared on CISA’s website in a news release distributed on February 7, 2024.
The Cybersecurity and Infrastructure Security Agency (CISA) and the Environmental Protection Agency (EPA) recently hosted a CISA Live event on LinkedIn, titled Boosting Water Sector Cybersecurity. The event featured CISA Deputy Director Nitin Natarajan and EPA Director of Water Infrastructure and Cyber Resilience Division David Travers, highlighting the critical importance of water sector cybersecurity.
The livestreamed event shared resources specifically developed for the Water Sector and featured the Water and Wastewater Sector Cybersecurity Toolkit, which was jointly released by CISA and EPA on January 30, 2024. This toolkit marks a crucial step in bolstering the sector’s resilience against evolving cybersecurity challenges by providing practical safeguards and solutions.
“This toolkit is a testament to the power of collaboration in enhancing our national cyber defense,” said CISA Deputy Director Nitin Natarajan. “Our work in the water sector is coordinated with the Environmental Protection Agency (EPA), federal partners, state and local authorities, and the members of the water sector coordinating council including owners/operators and industry organizations, among others, to defend against today’s threats and collaborate to build a more secure and resilient infrastructure for the future. We look forward to seeing a measurable reduction in risks to the water sector through the resources provided in this toolkit.”
The Water Sector is the foundation for the nation’s health, safety, economy, and security. Yet faces significant cyber and physical risks amidst resource constraints. The toolkit was developed with the water sector and equips sector members with actionable insights to elevate their cybersecurity posture in one place.
“Cyber threats present a risk to the essential drinking water and wastewater services that people across the country rely on every day. EPA, CISA and other federal agencies are working together to support cyber security best practices," said EPA Assistant Administrator for Water Radhika Fox. "This toolkit provides easy access to resources for water utilities to enhance cyber security measures.
Key features of the Water Sector Cybersecurity Toolkit include a newly published Cybersecurity Incident Response Guide and essential services such as free cybersecurity assessment services, free cyber vulnerability scanning, technical assistance support, cybersecurity performance goals alignment, and cyber hygiene tools. This arsenal of resources emphasizes the toolkit’s value in enhancing cybersecurity readiness across the Water Sector. CISA and EPA will update the toolkit periodically to include new resources and respond to the evolving needs of the sector.
For more information on the Water Sector Cybersecurity Toolkit, please view the recorded CISA Live event and visit cisa.gov/water.
Stand Up to Bullying, Using Technology for Good
Wednesday, February 21, 2024
Blog topics:
 For all the advancements and progress that we achieve as a society in today’s increasingly digital world, we often find ourselves lamenting whatever it is we think we’ve lost.
For all the advancements and progress that we achieve as a society in today’s increasingly digital world, we often find ourselves lamenting whatever it is we think we’ve lost.
In the business world, such things are sometimes referred to, simply, as a “negative byproduct”, or an “unintended consequence”. If it’s something that happens, as a part of our everyday life, for most of us, we adjust, right? After all, one of these days maybe we’ll look back and laugh a little more at a time (before the Internet) when our phones were mostly mounted to a wall.
Unfortunately, bullying and, specifically, cyberbullying isn’t something that’s so easily explained and what we’ve lost is measured in how it impacts someone’s life and well-being. This is especially true, given the fact that someone can be bullied using a digital device, such as a phone or a computer, but it also happens over social media, in a text, an email, or instant messaging, or even when you’re online playing a video game.
That might be why, too, at a time when at least one-third of middle and high school students have reported being a victim of cyberbullying and, a recent study indicated that 30 percent of the adults surveyed said they were bullied at work, it’s more than a good bit of timing for us to take some time out of our day on Friday February 23rd for International Stand Up to Bullying Day.
What has become an event that is observed twice a year in 25 countries, it all began with a simple act of kindness. In 2007, two 12th graders – from the Canadian province of Nova Scotia – stood up for a fellow classmate after being picked on for wearing a pink shirt. Together, they purchased 50 pink shirts at a discount store and emailed their classmates asking them to wear the shirts to support the student who had been bullied. Not only did the students wear the shirts, but many others also joined in, by coming to school in their own pink clothes. By the following year, International Stand Up to Bullying Day had gone viral in many countries across the world.
Kind-hearted efforts, such as this, are needed, especially when you consider how much screen time most of us (not just teenagers and young adults) spend looking at our phones or mobile devices. Because of this, it’s easy to see why there’s never been a greater opportunity to go after someone with hundreds of calls or messages in just a matter of minutes or a few hours. Worse than that, the intensity of it all can be compounded, as evidenced by the fact that it’s not unusual for a group of people (of any age) to bully one person with tragic consequences.
To get started, StopBullying.gov is a great resource and if you or someone you know is being bullied, there are steps you can take to keep yourself and others safe from bullying. And whether you’re a kid, teenager, or an adult, the website includes information on what you can do.
If you have done everything you can to resolve the situation, the website features additional information to connect you or the person who is being impacted to talk with someone now.
You can call or text 988 to chat with Lifeline. There are also resources for veterans and you can also find a counselor or other mental health services locally.
If you are being bullied online, there are also things you can do to help protect yourself, including:
- Change your privacy settings.
- Block (and un-friend) any harassing accounts, email addresses or phone numbers.
- Keep your personal details private.
- Take a break from your phone or computer.
- Save harassing emails, texts, or messages.
- Report bullying where it happens.
- Tell an adult that you trust.
- Don’t respond to mean or threatening messages.
- Report any serious threats to the police.
Here in Indiana, you’ll find additional resources on the Indiana Cyber Hub, with links to trusted sources, such as CISA, Federal Trade Commission (FTC), and KidsHealth.org.
Maybe if you think about, we can achieve a better outcome for connecting with one another, simply, by following the words of author Angelica Hopes, from The S. Trilogy, and “…always remember the three R’s of life – respect for self, respect for others, and responsibility for all (of) your actions”.
Apply for a Scholarship, Avoid a Scam
Wednesday, February 14, 2024
Blog topics:
 When it comes to the cost of an education – be it for college, vocational school, or a program to earn a certification -- there’s always one thing that a guidance counselor or career coach will remind you and your family to do when it comes to paying for it all.
When it comes to the cost of an education – be it for college, vocational school, or a program to earn a certification -- there’s always one thing that a guidance counselor or career coach will remind you and your family to do when it comes to paying for it all.
And the advice is, be sure to apply for as many scholarships and grants as you can. After all, it’s estimated that nearly $100 million in scholarships go unclaimed each year, and $2 billion in student grants go unclaimed. That’s good news, as there are a LOT of scholarships and grant money that’s available annually from trusted sources so long as you’re willing to put the work in to apply – and the only roadblock, more often than not, is a lack of applicants. On a side note, there are some unique opportunities (that are legit actual scholarships) to help make your education more affordable that might surprise you.
It’s good information, too, as this is the time of year when a lot of people are applying for school; maybe that’s why February is Financial Aid Awareness Month.
Because with all of the money that’s out there, cybercriminals are using the opportunity to rely on a variety of scams to steal a student’s identity or money, or that of a family member. In 2022, in an article in Forbes, it was reported that scammers were estimated to have stolen $5 billion from Americans in student loan-related scams.
Often times, cybercriminals will try and convince you that they’ll “help” you get financial aid, or a scholarship and it begins with a social media post, email or, even, a letter in the mail. As one example, it takes on the appearance of an invitation, suggesting that you’ve been selected for a particular scholarship or financial aid package. According to the Federal Trade Commission (FTC), there are six signs of a scam involving the phrases they often use. If they hear any of these phrases or a variation of it, walk away.
Here are a few key steps to follow, including:
- Fill out the free FAFSA form to apply for financial aid.
- Never pay anyone to fill out or process your FAFSA.
- Talk with a guidance counselor (if you’re in high school) or the financial aid office (if you’re planning to attend a college or vocational school) about your financial aid and scholarship options.
- Never pay at a seminar on how to get financial aid or scholarships. Especially if they pressure you to pay.
- Do your research before you pay anyone for help with financial aid or scholarships.
- Share these ideas with others who are looking for financial aid, too. You can help them avoid a scam.
As with any cybercrime, if you believe you’ve been the victim of a scam – or you want to report the details of a scam that could potentially impact someone, contact the FTC at: ReportFraud.ftc.gov/, or, if you’re here in Indiana, visit the Indiana Cyber Hub website and go to the Report a Cyber Incident page.
It’s been said that “knowledge is power” and there’s something satisfying about being able to learn a new set of skills that could help improve your quality of life. And regardless of the path you choose to follow, be sure to keep in mind that there are plenty of free resources out there so that no one gets in your way!
Romance Scams: Protecting Yourself is More Than a “Matter of the Heart”
Wednesday, February 7, 2024
Blog topics:
 When it comes to cybercrimes, romance scams are anything but a sweetheart deal.
When it comes to cybercrimes, romance scams are anything but a sweetheart deal.
It’s enough to cause someone, who we might’ve referred to as a “hopeless romantic”, to give up on the “Power of Love”. Or, at the very least, for some of us, we wouldn’t be trying to decide as to whether or not we need to reach out to the producers at MTV’s “Catfish”.
Yet, at a time when almost a third of Americans said they’ve used an online dating service or app and fully 10 percent of people who are in a relationship said they met their partner online, the cybersecurity steps we’re needing to take to meet someone online – as a way to begin a relationship – is not unlike the tips we’re reminded to follow with our bank accounts, credit cards, social media profiles, and, yes, even our own personal information.
With Valentine’s Day a week away, it can feel, at times, it’s more of a transaction than it is about, maybe, falling in love, especially when you consider:
- In 2022, Americans lost $1.3 billion to romance scams.
- That’s a number that may be even higher when you consider that some people – embarrassed by what happened to them – are reluctant to come forward and report that they’ve been a victim.
- Forty percent of romance scam victims said the contact began on social media.
If you’re not familiar with how these scams work, it begins when a bad actor creates a fake online profile. From there, they engage you in a conversation, be it online or on the phone, and, often, it’s not long before they’re pursuing you with a not-so-innocent flirtation.
There’s a pattern to their deception, with more red flags than you could throw after a crash at a NASCAR race, including:
- The person asks for money for an urgent matter, such as a medical expense, or even a plane ticket to visit you. Never send money to someone you haven’t met in person.
- The person requests a hard-to-track form of payment, such as a preloaded gift card.
- He or she claims to live far away from you; often in a foreign country, or they’ll tell you they’re in the military and serving overseas.
- The person breaks promises to see you in person, or they want to move the conversation you’re having from the dating app to other forms of messaging, such as WhatsApp, Signal, or Telegram.
- The relationship feels like it is moving very fast.
If you suspect that someone is trying to take advantage of you (or a friend or family member), it’s important to take action and immediately stop communicating with the person. Also, be sure to:
- Note any identifiable information you have on them, such as an email address or phone number.
- Be sure to take screenshots and write down any contact information.
- If you’ve been scammed out of money, contact your bank or credit card company.
- File a report with law enforcement.
- Report the scam to FTC and the FBI.
- Here in Indiana, you can also visit the Indiana Cybersecurity Hub website and click on the “Report a Cyber Incident” page.
As with anything you post on social media, it’s always a good idea to think about what you’re sending, what it reveals about you, and who can see it.
- You can also consider setting your social media profiles to “private”, as it makes it harder for cybercriminals to target and communicate with you.
- Always “think before you click” on any message that pushes you to do something immediately or asks you for personal information.
- Never share any personal or financial information via email or text if you do not know the sender.
- You can also do what is known as a reverse image search of the scammer’s profile picture.
- In doing so, you may see that the image belongs to an entirely different person or that it’s affiliated with different (or multiple) online identities.
- If that’s the case, there is a good chance that the person – behind the fake profile – is trying to scam you.
* * *
Enjoying the company of someone we can trust is one of those things we’ve come to discover that we can’t always take for granted. What is it Forrest Gump said, “life is like a box of chocolates, you never know what you’re to get”. But, as with a lot of things in life, we can do our best to avoid trouble, simply by trusting our instincts and being aware of our surroundings – even when we’re online.
Happy Valentine’s Day!
Identity Theft Awareness Week: Protecting Your Personal Data – A Reason to Celebrate
Wednesday, January 31, 2024
Blog topics:
 When it comes to dealing with cybercriminals and identity theft, it’s too bad we can’t just hit the “easy button” when we need it, especially when it comes to preventing someone from using our name or personal information to commit (all kinds of) fraud.
When it comes to dealing with cybercriminals and identity theft, it’s too bad we can’t just hit the “easy button” when we need it, especially when it comes to preventing someone from using our name or personal information to commit (all kinds of) fraud.
If you’re wondering how the button fits into all of this, you might be interested to know that, back in 2005, a New York ad agency created a clever TV commercial for the Super Bowl that featured an office retailer’s solution for handling – what you might say – some of life’s everyday challenges. Heck, they even made it an in-store product.
- Of course, there’s nothing easy or funny about the fact that identity theft occurs every 22 seconds in the U.S.
- And according to the Federal Trade Commission (FTC), in 2022, there were more than 1.1 million reported cases of identity theft.
Yet for all of the information that you’ll see about cyber crimes and data breaches, there is an opportunity for all of us to better understand how we can better protect our personal data. And while it’s not something that will cause you to run down to Party City and celebrate, it is Identity Theft Awareness Week.
Here in Indiana, the Attorney General’s office reminds Hoosiers to follow five steps for protecting you and your family, including:
- Do not conduct any sensitive transactions, including purchases, on a public Wi-Fi network.
- Create a unique password for each online account and change it often.
- Don’t click on anything in unsolicited emails or text messages.
- Be careful with the information you and your family share on social media. Sharing things like pet names, schools, and family members can give scammers the hints they need to guess your passwords or the answers to your account security questions.
- Place a security freeze on your credit reports to block an identity thief from opening a new account or obtaining credit in your name and keep new creditors from accessing your credit report without your permission.
In addition to the FTC’s website, Nerdwallet.com features everything from the seven types of identity theft and the warning signs to the 10 ways identity theft happens. There’s even a video. HINT: For all the technology we can access, you can have your personal data stolen without even using your smartphone or computer.
If the worst case scenario happens and you believe you’re a victim of identity theft (or your organization is impacted), be sure to report it! The Indiana Cyber Hub website’s Report a Cyber Incident page offers an easy-to-follow, step-by-step process for what you need to do.
Most importantly, you’ll want to take immediate action and know your resources; FREE help is available (that’s your EASY button…no purchase required).
Data Privacy - It's What's Trending
Wednesday, January 24, 2024
Blog topics:
 When it comes to the types of things that catch our attention, there’s the trends we see, especially when it comes to fashion (think sequins…) and food (alternatives to chocolate, yes, you read that correctly).
When it comes to the types of things that catch our attention, there’s the trends we see, especially when it comes to fashion (think sequins…) and food (alternatives to chocolate, yes, you read that correctly).
Yet, when we’re our phone, iPad, or laptop and we’re on social media, it’s all about what’s trending; for everything from Taylor Swift’s travel schedule to make it in time to be at the Super Bowl and how she might go about it to data privacy (after all, it’s Data Privacy Week and Sunday, January 28th is Data Privacy Day).
The fact is data privacy is something that should be trending for all of us. The challenge is two-fold. It’s a balance we deal with, in terms of who has access to our personal data and financial information while, at the same time, understanding how do we protect our data in a way that we avoid becoming a victim of a phishing, vishing or smishing attack.
Fortunately, there’s a lot of trusted resources, who share a lot of great information about the steps you can take proactively for keeping secure your personal information. Here’s a few of the 10 must-know tips from the National Cybersecurity Alliance, including:
- Encrypt your data with a VPN (Virtual Private Network) service.
- Don’t save your passwords on your browser.
- Avoid using public Wi-Fi.
- Update all your tools, devices, apps and operating systems.
- Don’t click on unfamiliar attachments and files.
If you’re a small business owner, or you work in local government, at a school, or as part of a non-profit organization, data privacy is an important priority. Some days, it can seem as though that there aren’t enough people or programs to deal with the more sophisticated types of cyber incidents or cyberattacks that are occurring these days.
Yet, just as there’s lots of help available for when we’re out on our own, there is a great deal of free-to-download information related to data privacy to help make sense of it all, including right here in Indiana with the PII Guidebook from the Indiana Executive Council on Cybersecurity, as well as from CISA and the International Association of Privacy Professionals (IAPP).
Of course, because all of this is trending, you’ll want to bookmark our Indiana Cybersecurity Hub website as a FREE resource, not only for all things cyber, but to check back soon for an (even more) updated PII Guidebook and an all-new Indiana Privacy Toolkit that we think you’ll find useful to gain a better understanding of the latest trends in data privacy. And, you guessed it, it is what’s trending (right there with Taylor)!
Attention Shoppers: “National Use Your Gift Card Day” is January 20th
Wednesday, January 17, 2024
Blog topics:
 When it comes to gift giving, there’s few things in this world that are easier to do than purchasing someone a gift card.
When it comes to gift giving, there’s few things in this world that are easier to do than purchasing someone a gift card.
After all, there’s no struggling with trying to figure out someone’s size, or their favorite color. What’s more, a gift card can be practical (i.e., buying a gas card for a college student who’s out of state). It also gives us the opportunity to show our appreciation for a family member, friend, or co-worker to enjoy a nice evening out or provide them with a reason to get in a little shopping. Of course, if they really want to get away, there’s even gift cards they can use to book a flight on their favorite airline!
It’s also (VERY) big business.
To celebrate, this Saturday, January 20th is National Use Your Gift Card Day. It’s a great time to reach into your wallet, purse, or desk drawer, and treat yourself to something nice. How big a deal is this? In 2022, gift card sales in the U.S. topped $195 billion and it’s expected that, in 2023, sales are estimated to reach $204 billion. And this year, that figure is projected to be more than $220 billion. Add to that, nearly 60 percent of gift card recipients will spend more than the value they have on the gift card.
Yet, for all of the popularity that comes with giving a gift card or receiving one, it’s estimated that $15 billion in gift cards (annually) go unused! With all those options out there – and the money that it represents -- it’s no surprise that gift cards have become a popular target for cyber criminals. In 2022, consumers reported 48,800 cases of gift card fraud, accounting for more than $228 million in total losses. On top of that, gift card fraud and imposter scams (the most reported fraud category in 2022) often go hand-in-hand, creating even more of a problem.
Scammers like gift card cards because they are, often, easy to break into and also because they do not have the same level of security authentication as it is with a credit or debit card.
What’s a shopper or a gift card giver to do?
According to an article in Consumer Reports, there are a few things you can do to protect yourself, including:
- Buy gift cards online. Get them directly from retailers, chain restaurants, or other issuers. Criminals don't have easy access to those cards. This is especially important if you're purchasing a high-value gift card.
- Avoid purchasing in-store cards with easily accessible numbers and PINs. To stay safe, it’s a good idea to purchase gift cards that are in well-sealed packaging, or those that are kept behind a counter. If the cards are out in the open on a rack, look closely at a wide assortment of the cards and inspect the bar-code numbers to see if there are duplicates, or if the packaging has been tampered with. If the cards aren’t in view of surveillance cameras or store employees, you’ll want to purchase those cards elsewhere.
- If you receive a card as a gift, change the security code as soon as possible. Register the card when you get home, change the PIN, and use the card as soon as you can. The longer a card sits around, the more likely a cybercriminal is to steal the balance.
- Try to get stolen funds back. Some card issuers use cybersecurity defense systems, and they may be able to distinguish between honest and fraudulent transactions on your gift card. If your card has been drained, it’s important to call the issuer, report the incident and ask for reimbursement.
- Secure your home computer. Criminals can also gain access to your gift card numbers and PINs by hacking your computer. To help prevent that, make sure your security software is up to date, and always create and use strong password, or a password generator, and enable multifactor authentication on every site where it’s available.
Have fun this weekend and here’s another “Pro Tip” when it comes to gift cards, don’t let someone try to convince you to purchase gift cards and give them the numbers as a way to pay a bill or make it appear as though you’re helping someone – only a cybercriminal will try and do that.
You can visit the Federal Trade Commission’s (FTC) Consumer Alert website to learn more about other ways to stay cybersafe. And before you leave home this weekend, be sure to grab those gift cards and join in the celebration!
Indiana State Police Partnering in Human Trafficking Awareness Initiative
Monday, January 8, 2024
Blog topics:
 All this week, the Indiana State Police (ISP) Commercial Vehicle Enforcement Division (CVED) is partnering with the Commercial Vehicle Safety Alliance (CVSA) for CVSA's Human Trafficking Awareness Initiative on January 8-12.
All this week, the Indiana State Police (ISP) Commercial Vehicle Enforcement Division (CVED) is partnering with the Commercial Vehicle Safety Alliance (CVSA) for CVSA's Human Trafficking Awareness Initiative on January 8-12.
During this annual initiative, the ISP's CVED personnel will work on raising awareness about human trafficking by distributing outreach materials to commercial motor vehicle inspections.
Commercial motor vehicle drivers, crisscrossing America, are in a unique position to identify potential incidents of human trafficking and raising their awareness and providing drivers with the tools to identify and report signs of human trafficking is the goal of this campaign. CVSA’s Human Trafficking Awareness Initiative will be conducted across North America – in the U.S. from January 8 -12; in Canada from February 19-23; and throughout Mexico from March 11-15.
 According to the United Nations, human trafficking is the recruitment, transportation, transfer, harboring, or receipt of people through force, fraud, or deception with the aim of exploiting them for profit. Men, women, and children of all ages and from all backgrounds can become victims of this crime, which occurs in every region of the world, including North America. Human traffickers often use violence, fraudulent employment agencies, and fake promises of education and job opportunities to trick and coerce their victims.
According to the United Nations, human trafficking is the recruitment, transportation, transfer, harboring, or receipt of people through force, fraud, or deception with the aim of exploiting them for profit. Men, women, and children of all ages and from all backgrounds can become victims of this crime, which occurs in every region of the world, including North America. Human traffickers often use violence, fraudulent employment agencies, and fake promises of education and job opportunities to trick and coerce their victims.
The CVSA, together with the Indiana State Police Commercial Vehicle Enforcement Division, is collaborating with Truckers Against Trafficking to engage and equip the commercial vehicle industry in the fight against human trafficking.
To report suspected human trafficking, please call the National Human Trafficking Hotline at (888) 373-7888 or text INFO to 233733.
NATIONAL TECHNOLOGY DAY: CELEBRATE NEW YEAR, RESOLVE TO BE MORE SECURE
Wednesday, January 3, 2024
Blog topics:
 Now that we’re a few days into a new year, the confetti’s been cleaned up in Times Square and from all of the stadiums that hosted a college football bowl game.
Now that we’re a few days into a new year, the confetti’s been cleaned up in Times Square and from all of the stadiums that hosted a college football bowl game.
And, yet, in less time than it takes to stage one final drive down the field or take a knee and run out the clock, a successful ransomware attack occurs every 40 seconds and attempts are made every 11 seconds.
With clock management like that, it’s almost as if some guy already knew what plays you were going to call. But, when it comes to protecting your company’s critical systems or protecting your own personal and financial information when you’re online, you’re going to want to have a better game plan.
To help make sure your year gets off to a better start , let’s begin by celebrating National Technology Day on Saturday, January 6th. It’s the perfect time to take advantage of more of the cybersecurity resources and best practices to help protect our tech-infused mobile devices, smart home products and, most importantly, our critical systems.
As with most of the things we try to improve, as part of our everyday lives, the effort begins at home. SecurityinFive.com offers a great take on the eight essential personal cybersecurity tips that’ll help you start 2024 with a digital clean slate, including:
- Updating your passwords
- Enabling two-factor/multi-factor authentication
- Reviewing app permissions
- Keeping your software and devices updated
- Being cautious with emails and links
- Securing your home network
- Regularly backing up your data
- Educating yourself about the latest cyber threats and best practices
Conversely, if (even part of) your job involves the responsibility of making sure things (and we mean servers, backup systems, employee cyber policies, etc.) run smoothly, there’s a great article from ISACA Global about the five things information security, IT and cybersecurity professionals should consider putting on their “to do” list that’ll help an organization improve its performance. This is especially true, as it involves security risks and dealing with potential threats and malicious actors. Among the five steps to consider taking includes:
- Building your AI Knowledge
- Architect Security for the Cloud
- Refocusing Security on the Human Element
- Building Security Governance
- Doing Your Boring Stuff Well
We’re often reminded that all of us can do more to avoid being a victim of identity theft, or to work at a company or organization that is impacted by a phishing attack or a data breach.
At times, it can seem like a tall task.
According to a recent report from IBM, the global average cost of a data breach in 2023 was $4.45 million, a 15 percent increase over three years. And the average total cost of a ransomware breach rose to $5.13 million. That’s 13 percent higher compared to 2022.
Fortunately, there are a lot of free cybersecurity resources available through the State of Indiana, including:
- Indiana Executive Council on Cybersecurity (IECC) and the Indiana Cyber Hub website for the benefit of all Hoosiers, businesses, local government and schools.
- Indiana Office of Technology (IOT) – featuring a wide range of services designed to assist local government.
- Indiana Department of Homeland Security (IDHS) leads the Hoosier State’s emergency planning and operations, first responder training and fire and building safety. DHS also provides a key role with resources, such as the free-to-download Emergency Manager Toolkit 2.0 and other tools that can be used to help communities stay safe and protected.
- Together with the important work in cyber that is performed by the Indiana National Guard and the Indiana State Police, cybersecurity is a top priority. Add in the strong partnerships that exist with federal agencies, such as the Cybersecurity Infrastructure and Security Agency (CISA), there is a significant and ongoing commitment to capitalize on utilizing technology to create an even greater level of awareness for cyber in a way that’s intended to help all of us.
In doing so, we’re able to push it over the goal line when it comes to taking down more of the bad actors and cybercriminals that are out there. Happy New Year!
A FEW CYBER TIPS FOR WHILE YOU’RE AWAY FOR THE HOLIDAYS
Wednesday, December 27, 2023
Blog topics:
 With a few days left before the New Year, there’s a few things – that not unlike making sure you bought a gift for your all of your in-laws this year – you’ll want to make sure you’ve taken care of when it comes to your company's cybersecurity.
With a few days left before the New Year, there’s a few things – that not unlike making sure you bought a gift for your all of your in-laws this year – you’ll want to make sure you’ve taken care of when it comes to your company's cybersecurity.
Over the holiday season, the global number of attempted ransomware attacks has increased, year-over-year, by 30 percent. Add to that, there is an average increase of 70 percent in the number of attempted attacks that occur in November and December, compared to January and February.
Also, according to a recent article in Security Intelligence, a report from the retail and hospitality sector highlights the fact that imposter websites, product-focused phishing attempts and phishing attempts impersonating executives all tick up during the holidays. And there is the (continuing) rapid rise in social engineering attacks.
As you finish celebrating the holidays and you and your co-workers are coming in and out of the office, there are five things that you can do to protect your business, employees and customers, including:
- Have a response team in place – It's critical to know who can be called in the event a cyber incident or cyberattack occurs. Be sure, too, to clearly establish, in writing, who’s on call and when.
- Consider managed detection and response – The reality is, with the increasing complexity of malicious and automated cyber threats, many organizations lack the security skills and resources to handle a sophisticated or advanced type of threat. To help offset those challenges, some companies transfer security tasks to a managed detection and response (MDR) provider.
- Be EXTRA careful with downloads, clicks, messages and emails – For most of us, the holidays are hectic enough, as we balance what we need to do at work with whatever plans we might have to be with our family and friends. Because of that, we let our guard down and that’s exactly what cybercriminals are counting on. Remember, too, the majority of malware still gets into computers and systems due to human error. The best approach is to be wary of any and all communication, even if it appears as though it’s coming from a trusted source and all of us should treat any unsolicited message with the highest level of suspicion.
- Be sure to lockdown privileged accounts - It’s common for intruders to penetrate networks by escalating privileges to the administration level, where they can then deploy malware. High-level access is rarely required on holiday breaks or weekends. As a result, some security experts recommend locking down privileged accounts.
- Establish clear isolation tactics - Isolation stops attackers from making any further ingress on your company’s network and from spreading malware to other systems or devices. It’s not unusual for security teams to disconnect a host, lock down a compromised account or block a malicious domain. Another tip - scheduled and/or unscheduled drills can help make sure everyone is prepared and the procedures that have been put into place will perform adequately in the event of a breach.
It's important to keep in mind that not all of these suggestions can (or will) be achieved overnight. But, following best practices with your cybersecurity – at work and at home – is, really, a never-ending task that has become an important part of our everyday lives.
Managing all of this – as we go – also makes it easier for everyone to be better engaged when it comes to managing their own personal cybersecurity and, as a result, the company or organization that you work for, is better protected. Looking to learn more? There is a great article on Tripwire (featuring "10 Essential Tips") and, as always, CISA is a great source for all things cyber, especially when it comes to avoiding social engineering and phishing attacks.
Best of all, it allows each of us an opportunity to, maybe, take a day off, catch up with a friend over lunch, or just crash out on the couch. Or, if your kid is home from college, you had a chance to watch a lot of football (it was Boxing Day...) and check out teams, such as Nottingham Forest, in the Premier League.
Interested in a Career in Cyber? Certifications Can Create Opportunities
Wednesday, December 13, 2023
Blog topics:
 PERSPECTIVES FROM THE CAMPUS
PERSPECTIVES FROM THE CAMPUS
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name, “Perspectives From The Campus Series”, we invite experts – immersed in the pursuit of educating their students – to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the latest installment of this series, David Dungan, who serves as the Executive Director at the Center for Security Services and Cyber Defense at Anderson University, discusses the significance of certifications in pursuing (or advancing in) a career in cybersecurity.
By David Dungan
Cybersecurity is one of the largest growing industries in the United States today. According to a report from the U.S. Bureau of Labor Statistics, cybersecurity employment for positions like information security analysts is projected to grow by 32 percent by 2032.
Add to that, there are more than 570,000 cybersecurity job openings in the U.S. If you’re wondering as to how that measures up, it’s important to recognize, in 2022, the demand for cybersecurity professionals grew at a rate that was twice as fast as the workforce.
After all, it could be said that we’ve gotten to a point – with technology and all of the cyber threats and incidents that we’ve experienced - you could say that there is not a staff, company, or industry that wouldn’t benefit by having an extra person or a team to protect its data and keep its critical systems safer and more secure.
Not only is cybersecurity offering great opportunities, but there are also many different pathways for finding a job in the field. And there’s one thing you can do – as a candidate – that’ll help you stand out – certifications.
Obtaining a certification is a great way to gain the skills, knowledge, and experience to advance your career. Many companies and organizations also prefer candidates who’ve completed a certification to validate the level of knowledge someone possesses about best practices.
When comparing prices and reputation of certifications, some of the most essential entry-level cybersecurity certifications include programs, such as: CompTIA Security+, Cisco Certified Network Associate (CCNA), Microsoft Certified: Security, Compliance, and Identity Fundamentals, and ISACA Cybersecurity fundamentals.
- CompTIA Security+-This is one of the most well-known entry-level certifications in the industry and is often a requirement or highly recommended asset for entry level jobs. The certification covers many topics such as network security and IT risk management.
- Cisco Certified Network Associate (CCNA)- This certification focuses on network security. Topics covered include network access, IP services, automation, interpreting components of a routing table, and configuration source NAT using static and pools.
- Microsoft Certified: Security, Compliance, and Identity Fundamentals- This certification is the most entry-level, yet still useful certification today. It is aimed at students and business users and helps grow baseline knowledge of a broad array of cybersecurity topics, focusing mostly on their use within Microsoft 365 and Azure environments.
- ISACA Cybersecurity Fundamentals- This is another cybersecurity certification which builds on the entry-level niche for people wanting to get into cybersecurity. The certificate covers four cybersecurity related domains- threat landscape, information security fundamentals, securing access, and security operations and response.
In addition to the advantages that are gained by earning a degree in cybersecurity at a college or university, certifications are also available for job seekers, who are more experienced.
Overall, obtaining certifications in addition to a degree might seem like a daunting task, but taking the extra initiative to pick up these certifications will improve your knowledge of the field you’re working in, as well as your professional standing within the industry.
For more information about a career in cyber, visit the Indiana Cyber Hub, ISC2, or the NICCS Interactive Cybersecurity Career Map.
STAYING CYBERSAFE ON PUBLIC WI-FI
Wednesday, December 6, 2023
Blog topics:
 PERSPECTIVES FROM THE CAMPUS
PERSPECTIVES FROM THE CAMPUS
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name, “Perspectives From The Campus Series”, we invite experts – immersed in the pursuit of educating their students – to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the latest installment of this series, David Dungan, who serves as the Executive Director at the Center for Security Services and Cyber Defense at Anderson University, discusses the importance of protecting yourself when using public Wi-Fi.
By David Dungan
When accessing public Wi-Fi, there are two main cybersecurity issues you should stay aware of: fake access points and packet sniffers.
A fake access point, also referred to as a “pineapple”, is a Wi-Fi network -- disguised as a public access point -- which is controlled by a malicious actor who may be trying to steal your information. Let's say you are sitting in a Starbucks, and you see an open Wi-Fi network called “Starbucks_Official” that offers full bars of connection. What you may not have noticed is that farther down on the list of networks is another Wi-Fi network called “Starbucks”. The fact is, the “Starbucks_Official” access point is not legitimate and it’s coming from a device that’s been designed to let you access the internet while, at the same time, snooping on all the information you access through it.
Often times, it’s not unusual for threat actors to make it appear as though their fake networks are stronger and, as a result, more convincing than the network they are trying to impersonate to encourage more people to click on them.
Another threat to be aware of are “packet sniffers” who maliciously use legitimate tools, such as Wireshark, Firebug or Fiddler, that are designed to receive all the information going through a Wi-Fi network. While it can’t see encrypted information like a pineapple may be able to, you might be surprised by just how much of the information you send and receive online is unencrypted.
According to the National Security Agency (NSA), the two most important things you can do when using public wi-fi and to stay safe from packet sniffing is to use a personal or corporate-owned VPN (virtual private network) and to visit websites that you connect with that includes https:// in the address bar and not just http://.
If you don’t have a device of your own, most libraries have public computers for anyone to use. While using their devices are a useful resource for accessing the Internet, it’s important to stay safe when using them. Public devices allow almost anyone to have uninterrupted access to them making them susceptible to tampering. It's important to be aware that devices and programs can be used to log keystrokes and steal data from public devices. These tools can be hard even for professionals to detect, so the best practice is to act as though they do exist and determine what risks you are willing to take based on that information.
Also, any time you use a public device, it’s a good idea to imagine that someone is looking over your shoulder and seeing everything that you are doing. This means that you should avoid putting any kind of personal password into these devices, so as to avoid making any searches that could raise any flags and avoid accessing online banking and shopping portals. The Cybersecurity Infrastructure and Security Agency (CISA) also offers some great information to keep in mind and use for staying safe when using public Wi-Fi.
Remember, any time you are using public resources to access the Internet, it’s OK to ask yourself as to what information you might be revealing to other people and how much of a risk you are willing to take with sharing that information. Stay safe out there!
CYBERCRIMINALS UNWRAP HOLIDAY SHOPPING SCAMS, DON’T BUY IT
Wednesday, November 29, 2023
Blog topics:
 Traditions are a funny thing.
Traditions are a funny thing.
It wasn’t that long ago, or so it seems, the holiday shopping season officially started on Black Friday; a momentous occasion, we celebrated by camping out – in the middle of the night – to be the first in line to buy the hottest toy or high- tech gadget. Or we lost our minds jockeying past one another to try and get the last item on the shelf.
While it’s true, times have changed (a little) and with it, we get the opportunity to experience new traditions. In doing so, we’ve come to embrace technology as a way to make our lives easier, not only during the holidays, but with a lot of other things as part of our everyday life.
According to Adobe Analytics, Americans spent $9.8 billion in online purchases on Black Friday – an increase of nearly eight percent compared to a year ago. Add to that, although the doors to the stores were “closed” on Thanksgiving, according to the same report, we managed to spend $5.6 billion, in between carving our turkeys, gathering with our families, and watching football.
With all of this activity going on, cybercriminals are, once again, playing the role of the “grinch” (minus, of course, the change of heart and happy ending). By one estimate, nearly 75 percent of Americans experienced at least one type of holiday scam last year. As a result, $281 million dollars were lost to online shopping and non-delivery scams alone. According to Aura.com, there is some great information about a variety of holiday-themed scams you’ll want to avoid, including:
- Social media ads that lead you to fake online stores. Fraudsters use ads on social media to try to get you to go to fake stores that steal your money, credit card details, or personal information. In the worst case scenario, you could even become the victim of identity theft.
- Fake delivery notification texts. Scammers send fake text messages claiming that a package you’re waiting for has been delayed or that you need to pay a fee before it can be delivered.
- Fraudulent charities that steal your money. Con artists create fake charities or GoFundMe campaigns to trick you into sending money or sharing your personal information.
- Bogus deals on hard-to-find items or airline tickets. Many schemes take advantage of popular holiday items or inflated travel costs to get you to buy fake tickets or items.
- Fake surveys, giveaways, and other phishing emails impersonating well-known brands. Scammers send emails (as well as texts and phone calls) claiming to be from companies you know, such as Amazon or Walmart. These messages use social engineering tactics to steal your passwords, personal information, and financial details.
 Even with all of that, there are plenty of steps you can take – before making a purchase or a donation – to stay protected, such as:
Even with all of that, there are plenty of steps you can take – before making a purchase or a donation – to stay protected, such as:
- Learning the signs of a fake or unsecured website.
- Researching retailers before you start shopping (and visit the Better Business Bureau’s Scam Tracker Website).
- Securing your online accounts with strong passwords and two-factor authentication.
- Watching out for scam phone calls.
- Only buying gift cards from trusted vendors (avoiding auction sites).
As it’s often been said, if a deal seems too good to be true, it probably is.
Trust your instincts and don’t let what seems like a good deal cloud your judgment. If it’s a donation, it’s OK to do some research to make sure the cause you’re supporting is real and the organization is a legitimate one. To learn more, visit the Better Business Bureau’s Charity Checker or Charity Navigator. The Federal Trade Commission also offers great advice for giving; everything from the five things to do before you donate to the tips highlighting the safest ways to donate on social media and crowdfunding sites.
If something does happen and you think you’ve been a victim of a scam, be sure to report it!
Here in Indiana, you can go to the Indiana Cybersecurity Hub website (that you’re on) and click on the link “Report a Cyber Incident”. The website features the steps you’ll want to take to report the cybercrime and the FREE resources that are available to help you.
Here’s hoping that you have a (cyber) safe holiday, as you click your way through to find something for everyone on your list!
Traveling for the Holidays? Being Cyber Ready is the Easiest Dish You'll Fix This Year
Wednesday, November 22, 2023
Blog topics:
 By Joel Thacker and Tracy Barnes
By Joel Thacker and Tracy Barnes
The good folks at AAA announced this week that 55.4 million Americans will be traveling 50 miles or more -- in planes, trains and automobiles -- to celebrate Thanksgiving; a figure that includes 1.25 million Hoosiers, who’ll hit the road, take to the skies or ride the rails, beginning today through Sunday.
And whether your plans involve heading somewhere to be with family and friends, or you’re hosting everyone at your place, you’ll want to take just a little bit of time (we’re talking just a few minutes, here and there) to follow a few simple steps to stay cybersafe; tips that’ll help keep your mobile devices secure while, at the same time, protect your personal and financial information, regardless of where you’re at.
After all, cybercriminals, at this time of the year, you might say, are working overtime in an effort to try and steal our identity or gain access to our bank accounts or credit cards, by trying to run up all kinds of fraudulent charges. In fact, according to a report, published in 2021, researchers observed a 70 percent average increase in attempted ransomware attacks in November and December compared to January and February.
Instead, be sure to check out this “tip card” from the Cybersecurity Infrastructure and Security Agency (CISA) with what you need to know before you leave, as well as what to keep in mind once you arrive at your destination.
Before You Go:
- Update your mobile software. Treat your mobile device like your home or work computer. Keep your operating system software and apps updated, which will improve your device’s ability to defend against malware.
- Back up your information. Back up your contacts, photos, videos and other mobile device data with another device or cloud service.
- Set up the "find my device feature" on all your devices. This will help you find your phone, tablet or laptop, in case you lose or misplace it, and it might allow you to disable or remove any data from it, if it gets in the wrong hands.
- Keep it locked. It’s a good idea to get into the habit of locking your device when you are not using it. Even if you only step away for a few minutes, that is enough time for someone to steal or compromise your information. Be sure, too, to use strong PIN codes and passwords.
While You’re Away:
- Avoid using public Wi-Fi networks. Open Wi-Fi networks at places such as airports present an opportunity for attackers to intercept sensitive information.
- Turn off Bluetooth when not in use. Cyber criminals have the capability to pair with your device's open Bluetooth connection and steal personal information.
- Stop Auto Connecting. Disable remote connectivity and Bluetooth, as some devices will automatically seek and connect to available wireless networks.
- Be sure to use the same process with your headphones, ear buds, or any entertainment system that you have in your vehicle.
- This will allow you to disable these features so that you are able to connect wirelessly or with your Bluetooth network – when you want to.
- Be cautious when charging. Avoid connecting your device to any computer or charging station that you do not control, such as a charging station at an airport terminal, train station, or at a travel center or convenience store.
- Remember your physical security and be sure that you don’t leave your device unattended in public or any areas that are easily accessible (e.g., taxis, airplanes, and in your hotel room).
For all the fun experiences and memories that are created from being together with one another during the holidays, there’s a lot of stuff that can stress us out (like trying to decide if the homemade sugar cream pie we just baked, using Grandma Alma’s recipe, is as good as the original…).
Fortunately, it’s easier than that, and all we have to do is spend some of our screen time to better protect ourselves whenever we’re online. For more cyber-friendly travel tips, visit the National Cybersecurity Alliance and the Center for Internet Security and, as always, for the latest resources, best practices and more, for all things cyber in the Hoosier State, visit our Indiana Cyber Hub.
Happy Thanksgiving!
Demystifying Your Data: What’s with the Cookies?
Wednesday, November 15, 2023
Blog topics:
 One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name "Perspectives From the Campus Series”, we invite experts -- immersed in the pursuit of educating their students -- to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name "Perspectives From the Campus Series”, we invite experts -- immersed in the pursuit of educating their students -- to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the latest installment of this series, David Dungan, who serves as the Executive Director at the Center for Security Services and Cyber Defense at Anderson University, discusses the importance of protecting your personal information when it comes to websites that use cookies and what it means when data brokers collect information from you.
By David Dungan
“This website uses cookies”
How many times a day do you see a website that says something along those lines? Unfortunately, they are not referring to macadamia or chocolate chip.
Data brokers use web cookies (a small piece of code that attaches to your browser) to track what kinds of websites you visit and what you do on them. Data brokers also use these cookies to build detailed profiles of your interests and your personal identifying information (PII), including your gender, sexual orientation, and race, as well as major life events, and more.
These brokers then anonymize the information and put it into targeted interest groups to sell to advertisers. It’s a big business. It is estimated that the industry is worth $200 billion per year, with up to 4,000 data brokering companies worldwide.
How do they do it? In a matter of speaking, we provide it to them. By that, they use a few simple steps to obtain information, including:
- Your web browsing history - every time you use a search engine, social media app, or fill out an online quiz, you’re leaving an electronic trail.
- Public sources - This includes everything from birth certificates and marriage licenses to court records and census data.
- Commercial sources - In other words, your purchase history, what you’ve bought, when you bought it, how much you paid for it, and whether you used a loyalty card or coupon.
- Your consent - When you sign up for things like a rewards program, you may have given your consent for your data to be shared without necessarily realizing it (that is, unless you read the fine print).
Fortunately, just as we try to avoid giving into the temptation of eating our way through an entire box of Girl Scout cookies, let’s just say, too quickly, there are six best practices you can follow to better protect your privacy and security when using browser cookies. Among the steps you can take, includes:
- Clear cookies regularly.
- Adjust your privacy settings.
- Be careful when downloading apps or software.
Next time you see a popup asking you to agree to web cookies, it's a good idea to take a moment to carefully consider what that means and remember that it’s OK to deny any cookies you believe are unnecessary to prevent others from exploiting your personally identifiable information.
RESOLVE TO BE RESILIENT - PROTECTING OUR CRITICAL INFRASTRUCTURE
Wednesday, November 8, 2023
Blog topics:
 The message contained in today’s blog was authored by the Cybersecurity and Infrastructure Security Agency (CISA), with information provided by the Indiana Department of Homeland Security.
The message contained in today’s blog was authored by the Cybersecurity and Infrastructure Security Agency (CISA), with information provided by the Indiana Department of Homeland Security.
November is Critical Infrastructure Security and Resilience Month, a nationwide effort to raise awareness and reaffirm the commitment to keep our nation’s critical infrastructure secure and resilient.
Proactively protecting these resources is vital for preserving the safety and security of all Hoosiers. This year’s theme is “Resolve to be Resilient”. Weather is becoming more extreme, physical and cyberattacks are a persistent threat, and technology is advancing in ways that will change our future very quickly. We must prepare by accepting that it’s our responsibility to strengthen critical infrastructure and protect the vital services it provides.
We can do this by embracing resiliency and building it into our preparedness planning—and then exercising those plans. The safety and security of the nation depends on the ability of critical infrastructure to be able to prepare for and adapt to changing conditions and to withstand and recover rapidly from disruptions. This starts with building resilience into infrastructure investment.
One of the key components to creating an added measure of preparedness is by having a well-crafted Cyber Incident Response Plan (CIRP). In addition to helping define everyone’s roles and responsibilities, the plan should include a robust communications strategy that outlines how the information will be disseminated both internally and externally, in the event of a cyber incident or cyberattack.
Public-private partnerships, as evidenced by the work that’s been achieved over the past 7 years by the Indiana Executive Council on Cybersecurity (IECC), continues to play a critical role for leveraging our shared commitment by identifying vulnerabilities and mitigating risks through protective programs and training, as well as offering a wide range of best practices, resources, and tips, as featured on the Indiana Cybersecurity Hub website.
Attacks cannot be completely prevented from happening, but we can minimize their impact by building resilience into our infrastructure and into our society. For more information, visit CISA’s Critical Infrastructure Security and Resilience Month web page.
Cybersecurity for Education Toolkit 2.0 Connects Our School Communities
Wednesday, November 1, 2023
Blog topics:
 When it comes to making headlines, it might surprise you to know that, more and more, there are two things that are catching our attention these days -- education and cybersecurity.
When it comes to making headlines, it might surprise you to know that, more and more, there are two things that are catching our attention these days -- education and cybersecurity.
More than that, these two topics are linked together tighter than Taylor Swift and Travis Kelce.
Our K-12 school communities influence the quality of life we experience in our cities and towns. And, by every measure, it’s safe to say that cybersecurity is an integral part of our everyday life.
Three years ago, as we were trying to figure out how we were going to get all of our students back in the classroom while still dealing with a national health crisis, the Indiana Executive Council on Cybersecurity -- together with the Cybersecurity Infrastructure and Security Agency (CISA) and the Indiana Department of Education (IDOE) -- created the Cybersecurity for Education Toolkit. Filled with a wide range of best practices, tips, and resources, it was designed not just for teachers, students, or administrators.
Instead, the free-to-download guide was geared for everyone in a school community, including staff and school board members and superintendents, as well as the rest of us, regardless of whether or not you had kids in school. Knowing that many families were working from home while, at the same time, sharing space with their kids, some of whom were taking classes online, the guide served as a helpful tool to keep families secure whenever they were online.
Now, just as the school year began in early August throughout Indiana, the IECC worked closely with our partners at CISA and IDOE to produce a sequel -- Cybersecurity for Education 2.0 Toolkit.
Offering an even greater variety of easy-to-understand information, the benefits of the Toolkit are intended to build on everyone’s knowledge about cybersecurity and the importance of practicing good habits as it relates to:
- Students protecting their schoolwork and their identity/personal information.
- Teachers and staff managing their lesson plans while keeping their student’s data secure (including their grades and assignments).
- Superintendents and administrators protecting their students and keeping their facilities and critical systems protected
- Parents and families learning more about cyber with useful tips and free resources
- School Board Members using it to help with conducting its business on behalf of the school corporation and community it serves.
Best of all, the Toolkit is formatted as a PDF that can easily be saved as a Word document to enable you to cut and paste, copy and/or repurpose all of the materials as needed to share with your colleagues at school, or as information to be provided to your students, or a family can use at home.
Among the resources that are included are the four tips from CISA that administrators, teachers and students should follow for keeping anyone who relies upon computers in your school district to be safe.
There are articles that offer cyber-friendly tips for students of every age group from elementary school to high school. There’s even a guide on how to best protect yourself on social media. And, as many people continue to work remotely, there’s list of questions to consider when setting up a network at home featured in the Toolkit.
If you’re an administrator or a superintendent, there is a wealth of trusted state and federal resources to help guide your school corporation’s approach for being cyber safe for everything from your technical infrastructure to improving your cybersecurity posture, including:
- Indiana Cybersecurity Hub - State of Indiana Cybersecurity Website
- IDOE School Cybersecurity Moodle Community
- CISA Shields Up
- CISA.gov - Partnering to Safeguard K-12 Organizations from Cybersecurity Threats
- MS-ISAC
- K12 Six
At a time when a student’s school file, with enough personal information to steal someone’s identity, is worth as much as $1,000 on the dark web, the connection between cybersecurity and education, is unprecedented and more important than ever.
In addition to the Toolkit, the Indiana Cyber Hub website offers information for teachers and students, including resources for cyber and IT internships and there’s a link to a cyber careers page for anyone wants to turn their knowledge into a full-time job. Check it out today!
Updating Your Software: Necessary for (Avoiding) Evil
Wednesday, October 25, 2023
Blog topics:
 When it comes to our ‘personal’ cybersecurity, the threats, and incidents -- from cybercriminals and nation-state actors -- are more prevalent than ever.
When it comes to our ‘personal’ cybersecurity, the threats, and incidents -- from cybercriminals and nation-state actors -- are more prevalent than ever.
As recently as this past Sunday -- in an episode of “60 Minutes” -- we heard from five of the world’s foremost intelligence experts about some of the threats posed by China and the Cybersecurity Infrastructure and Security Agency (CISA) has identified Russia as a “top cyber threat”.
Of course, while it’s true that some of the percentages still continue to rise, it’s a great time to continue the conversation on how we can protect ourselves.
Thankfully, there are steps we can take to prevent a breach of our own personal information. One of the ways to do this is to keep all our device's software up to date. By now, we’re familiar (used to?) with all those annoying little pop-ups that appear at the top of our screens saying that a software update is ready to be installed. But these notifications are vital. Providers release these updates, as a way to continually fix or upgrade the systems and their elements. The “updates” help us do several things, including:
- Improving the performance of our devices
- Providing security updates
- Fixing design 'bugs' and protecting us against vulnerabilities that have been identified as needing to be repaired (also known as "patches")
All updates to the software programs we use are to our benefit. If you don't install them, it limits your ability to be fully protected. There are three ways to ensure these updates are being installed.
- Keep track of your notifications
- Watch out for notifications from your settings app. Your device will tell you when an update is ready to be installed and that’s when you want to make sure that you follow through with the update (it rarely takes more than a few minutes).
- Update your devices manually
- If you see the notification, and can’t trust yourself to come back to it, then update it immediately and take the time away from your device to decompress and “take a break” away from technology. Time away from a screen is never a bad thing, and you can be content that when you come back to it, you will be better protected.
- Turn on your automatic updates
- If you do not want to update your devices manually, you always have the option to have your device, do it automatically. Doing this will tell your device to update to its latest version around your usage schedule so it doesn’t interrupt you, making it as painless as possible.
To keep yourself protected, it’s a good idea to make sure you understand the needs of your device. Providers will always make things easiest for you to do something, so that you won't have to think about it beyond leaving your device alone for a set amount of time.
If you want to learn more, be sure to check out these tips from CISA on keeping your devices updated along with a handy “how to” tip sheet to help fix any unwanted security risks.
Remember, too, October is Cybersecurity Awareness Month and it’s the perfect time to use these best practices every day as a way to stay secure and better protected whenever you’re online.
How Can You Protect Your Digital Footprint Online?
Wednesday, October 18, 2023
Blog topics:
PERSPECTIVES FROM THE CAMPUS
 One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name "Perspectives From the Campus Series”, we invite experts -- immersed in the pursuit of educating their students -- to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name "Perspectives From the Campus Series”, we invite experts -- immersed in the pursuit of educating their students -- to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the latest installment of this series, David Dungan, who serves as the Executive Director at the Center for Security Services and Cyber Defense at Anderson University, joins in the celebration of Cybersecurity Awareness Month and shares his perspective on how we can protect our digital footprint online.
By David Dungan
From the time we’re born, with every step we take, we create and leave behind a footprint that’s uniquely our own. And it’s no different when we’re online.
Unfortunately, when it comes to the digital world, in which we live, learn, work, and play, we reveal a lot more about ourselves than we might realize and that’s one of the things that cybercriminals are counting on -- when it comes to trying to steal your money or your identity.
In fact, according to a recent report, the number of Hoosier victims of identity theft has nearly doubled in the last five years. If reading that leaves you feeling as though someone is trying to trip you up, consider:
- Indiana ranks 11th nationally for the greatest rate of increase in identity theft.
- Incidents in the state increased by more than 94 percent; a rate that’s much higher than the national average of 62 percent.
- Data from the Federal Trade Commission also shows credit card fraud reports in Indiana increased by more than 122 percent, and bank fraud increased by nearly 158 percent over the same period.
- Already this year, there have been more than 3,300 reports of identity theft across the state.
Fortunately, there are some steps you can take (and resources are out there) to help avoid running into problems when it comes to preventing someone from making it appear as though they’re you.
This is especially true when it comes to social media.
Regardless of the platform you’re on, it’s easier than ever and it’s fun to share tidbits of our lives with the people we care about. It’s that kind of sharing that cybercriminals are looking for, to help themselves to your personal and financial information. Before you post anything, it’s essential to review (and re-read) what you’re saying or sharing and it’s a good idea to get into the practice of using the same precautions when you’re looking through the content that’s on your feed, or any of the sites that you might visit while you’re on Instagram, LinkedIn, Twitter/X or Facebook.
To stay protected, be sure to check out these social media safety tips from the National Cybersecurity Alliance, including:
- Prize your personal info
- Check your settings
- Enable MFA (multi-factor authentication)
- Passwords - Think long, strong, and unique
- Share with care
- Posts are like ghosts
Additionally, remember that there’s a LOT of personally identifiable information that you’re already sharing -- including your date of birth, your phone number, and your address -- and that’s just the beginning. There’s also references to where you work and all of that is out there, along with the information for your family members and your friends. Don’t forget, too, there’s lots and lots of pictures and videos that you’re in.
Protecting all of that may seem, at times, more than a little overwhelming when you stop and really think about it. But that’s why that when you’re posting anything that you’re mindful of who you’re tagging (and that goes for your accounts, too) and who’s tagging you in their photos, videos, and posts. Among the other things you can do is to disable the cookies on websites that you visit
If you're wondering just how easy it can be to have your accounts compromised, a dedicated cybercriminal may be able to find your location based only on a photo. Moreover, anyone can figure out what kind of house you have, the brands of products you buy, your relative wealth, and more. That’s why it’s also important, in all situations, consider what someone who doesn't like you may do with the information.
One of the other things to consider are the private messages we send. Despite what we might think, private messages are not always just between you and your contact. While they may not be accessible to the general public, companies like Meta (i.e., Facebook, Messenger, and Instagram), Alphabet (i.e., Gmail, Hangouts), Apple, or X/Twitter possess the capability to access your private messages or data on their platforms, and gain information about you from what you're posting.
To learn more, there's a wide range of cybersecurity best practices, free resources and tips from trusted sources, such as CISA, National Cybersecurity Alliance, and the Indiana Cyber Hub.
At the end of day, the path we follow -- as part of our everyday life -- takes us to the experiences and adventures that define us, but if we take just a few precautions, it’ll help make sure that the digital footprints we create and leave behind are genuinely ours.
Multi-Factor Authentication: Easier to Use Than Telling Your Teenager "No"
Wednesday, October 11, 2023
Blog topics:
 By Joel Thacker and Tracy Barnes
By Joel Thacker and Tracy Barnes
If you think about it, a cybercriminal is a lot like a teenager, who has a knack (at least, every once in a while) for wearing out Mom or Dad to get something they really want.
At first, they might try to reason with you with a request that seems simple enough. Yet, as you take some time (maybe just a minute or two…) to learn more about what they’re planning (and what they’re really asking you for), that’s when their scheme starts to fall apart. Soon after that, you find yourself saying, “wait a minute”, before, of course, you’re suddenly responsible for ruining their life, weekend and/or they’re night out.
Depending on your age and generation and, regardless of how you might’ve been raised, admit it…you were once that clever teen, or you’ve come away with just a little bit of satisfaction knowing that your kid wasn’t able to pull one over on you.
In the cyber world, it’s kind of the same thing.
The request is an email, a text message, or even a phone call. What’s more, whoever it is, might be someone you think you know -- a family member, a co-worker, or even your boss. The fact is, for most of us, it’s human nature; we want to please someone by doing what they’ve asked us to do. Or we want to feel as though we have the ability to take someone at their word.
October is Cybersecurity Awareness Month and, for all of us, one of the reasons to celebrate is there’s, actually, a lot of things we can do to make our lives easier and protect ourselves whenever we’re online.
Following on the theme, “Secure Our World”, this week’s focus is to enable MFA, also known as Multi-Factor Authentication. Whenever we log into our accounts, whether it’s our checking account, or we’re spending some time on Instagram, we are sharing our personal information and confirming our identities. MFA provide us with an extra level of security, simply by entering a code that is texted to our phone or mobile device, or it’s one that is generated by an authenticator app.
Even if our passwords are compromised, an unauthorized user won’t be able to meet the second part of the requirement. Because of that, you’re able to experience that “wait a minute” moment and, instead, ruin the plans that a cybercriminal had for your money or to use your identity to steal from someone else.
The Cybersecurity Infrastructure and Security Agency (CISA) offers a great video to learn about all of the benefits MFA can provide and the fact that you don’t have to be some sort of tech expert to set it up on all of the accounts that it’s available to install it on. There’s also a handy tip sheet that’s free to download to get you started.
To learn even more about all things cyber, including here in Indiana, we invite you to keep coming back to the Indiana Cyber Hub website for all of the latest FREE resources, best practices and tips for all Hoosiers, businesses, and local government, including our schools. You can also sign up today to subscribe to our blog (it’s FREE) and we invite you to follow us on social media on Twitter/X, LinkedIn and Facebook.
Three Rules of Running (A Cyber-Safe Company)
Wednesday, October 4, 2023
Blog topics:
 PERSPECTIVES FROM THE CAMPUS
PERSPECTIVES FROM THE CAMPUS
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name "Perspectives From the Campus Series”, we invite experts -- immersed in the pursuit of educating their students -- to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the latest installment of this series, David Dungan, who serves as the Executive Director at the Center for Security Services and Cyber Defense at Anderson University, joins in the celebration of Cybersecurity Awareness Month and shares his perspective on how three rules of running can be applied to the responsibility of running a cyber-safe company.
By David Dungan
Cybersecurity and running can both be uncomfortable, especially with little training. It is not always easy to push yourself during a race when others are far ahead or when your sides are cramping from exhaustion. Nevertheless, you finish the race in your own time, celebrating because you have accomplished your goals. The practice of managing a company’s cybersecurity practices offers some similarities that most of us can appreciate; even if we’re the type of person whose experience with running is tuning into the Olympics to see who wins the gold in the 100-meter race.
After all, it can be exhausting keeping up with the newest trends. There’s also the challenge of keeping up with others, who have more resources; defined by an ability to implement cybersecurity policies that are more extensive, or because they’re able to invest more heavily in the latest software. More than that, there’s three rules of running -- preparing for the race ahead, keeping personal goals and priorities in mind, and staying engaged during the race -- to run our own cyber-safe companies.
Preparing for the race ahead
Companies and runners occasionally have difficulties determining where to start when they begin training or when they’re trying to reach a goal. Fortunately, government agencies offer resources such as self-assessments to identify how much you and your employees know about cybersecurity and how well your company is positioned with its information security. One of the best examples that’s available is the State of Indiana’s Cybersecurity Scorecard. In less than 15 minutes, the Scorecard is an online tool that will provide you with a score - and a report - of where your organization stands with its cybersecurity. What’s more, it’s FREE and was created, specifically, for the office manager, executive or IT manager to complete. Like with running, you don’t have to be an expert to do the assessment, and it gives you some valuable information to begin a conversation with your leadership or staff. In that sense, it compares favorably with the type of assessment (and feedback) that a coach, or someone who’s a more experienced runner would give you -- ahead of your next race. Companies can also learn about best practices and government standards with supplemental resources to begin addressing potential security flaws and vulnerabilities.
Focusing on personal achievements and goals
Not everyone will run a race at the same pace, and the same is true for cybersecurity and how it’s used within a lot of companies. Each company’s resources will vary due to its relative size or industry, so companies should do the best they can with the resources they have available and focus on their own policies and standards like a runner might focus on achieving a personal record. Internal policies and standards alongside external compliance standards should set the goals for each company. Not all businesses will be required to meet every compliance standard, so it is important to distinguish between what’s necessary (and not absolutely required), so as to avoid investing in products or resources that are either too expensive or won’t be fully utilized in a way that makes a difference.
Staying engaged during the race
One of the more difficult aspects of maintaining a cyber-safe company is keeping the interests of employees and other stakeholders while implementing security awareness training. For some people, no matter how much you feel as though you’re challenging them, learning best practices or new policies can be overwhelming and, well, a little boring.
To avoid that, runners often stay engaged by listening to music or a podcast during their run. Companies can utilize similar tactics by implementing a variety of educational materials such as knowledge assessments, videos, posters, and polls. We can learn in a variety of ways, from employee feedback to continually improve training lessons and measuring knowledge retention to ensure everyone is aware of their roles in a cyber-safe company. Additionally, it is important to celebrate any step that’s made towards running a cyber-safe company, as it incentivizes the collective efforts of a company and promotes a culture of security awareness. People will feel more invested if you celebrate their accomplishments and the progress they’re making.
Running enthusiasts of all ages experience different challenges, and the same can be true for companies. However, no matter a company’s size or industry, it is vital to keep running a cyber-safe company to prevent injury to a company’s vital information, while at the same time, protecting its customers, critical systems, and its reputation due to a potential cybersecurity incident or a cyberattack.
No matter someone’s reason for running (a cyber-safe business), it is always a step in the right direction when you proactively plan and prepare for ensuring what challenges are out there to keep you and your company on the right track.
Cybersecurity Awareness Deserves Year-Round Celebration
Monday, October 2, 2023
Blog topics:

By Joel Thacker and Tracy Barnes
While it might not possess the glamour and tradition of the Macy’s Thanksgiving Day Parade, or generate the kind of promotional opportunities we often see with the Super Bowl, Cybersecurity Awareness Month is an event that’s not only worth celebrating, it’s one that deserves our attention year round.
Following on the proclamation, on Sunday, by Indiana Governor Eric Holcomb designating the month of October as “Cybersecurity Awareness Month”, Indiana is continuing in its cyber readiness to keep all Hoosiers safe and secure and protect our critical infrastructure that’s essential to everyday life.
In its 20th year, the Cybersecurity Infrastructure and Security Agency (CISA), in partnership with the National Cybersecurity Alliance (NCA), announced this year’s theme is “Secure Our World”; it is an ideal illustration of the significance that cyber possesses for all of us.
And, just as we don’t limit ourselves to a single day, week, or month, to remind each other to be thankful of our family, friends, and co-workers, it’s important for each of us to continuously follow a few simple habits and “stay safe” behaviors whenever we’re online, whether we’re at home, at work or at school. And it’s especially true whenever we’re on social media or engaging in anything that involves our personal or financial information.
Keeping ourselves secure is achieved by focusing on four simple -- yet critical -- actions; steps that all of us should implement and continuously strengthen, including:
- Recognize and report phishing
- Use strong passwords
- Turn on multi-factor authentication
- Update software
Here in Indiana, cybersecurity continues to be a priority and the progress we’ve achieved comes at a critical time, as the severity and frequency of a cyber incident or cyberattack includes not only data breaches, but it’s also crossing over to more sophisticated attacks on the physical operations of water utilities, hospitals, schools, and local governments.
To help stay at the forefront of being prepared, the Indiana Cybersecurity Hub website features a wide range of FREE resources, best practices and tips, as well as free-to-download toolkits involving emergency management, education, and healthcare (and more) that have been developed by professionals to help build on your cybersecurity awareness. There’s even an Indiana Cybersecurity Scorecard to give you a good idea (in less than 20 minutes) of your organization’s overall cyber posture.
To keep it all moving forward, the Indiana Executive Council on Cybersecurity is continuing in its work, as outlined in the state’s cybersecurity strategic plan, positioning the Hoosier State nationally as a top-tier leader, among all states for cyber governance.
We invite everyone to join in the celebration of Cybersecurity Awareness Month and use the opportunity to connect with our family, friends, and co-workers and do our part to help keep one another safe whenever we’ve online. And, be sure to visit the Indiana Cyber Hub online for the latest cyber information on Twitter/X, LinkedIn and Facebook.
Cyber Threats Take Aim at Our Trust
Wednesday, September 27, 2023
Blog topics:
 PERSPECTIVES FROM THE CAMPUS
PERSPECTIVES FROM THE CAMPUS
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name "Perspectives From the Campus Series”, we invite experts -- immersed in the pursuit of educating their students -- to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the latest installment of this series, David Dungan, who serves as the Executive Director at the Center for Security Services and Cyber Defense at Anderson University, shares some important information regarding four cyber threats and what you need to know to stay protected.
By David Dungan
When it comes to cyber threats, it’s a matter of trust.
For a scheme or a scam to be successful, cybercriminals are relying on the notion that we will trust whatever it is we’re seeing or being asked to do in an email, or what we’re doing when we’re setting up a device at home (products we now refer to as the “Internet of Things”) and that it’s OK and, otherwise, is considered safe and secure. Unfortunately, as we’ve discovered, that’s simply not true.
This year, there are four cyber threats that have emerged as providing the greatest risk for consumers and while they’re not new, it reminds us of the importance that comes with protecting ourselves when we’re online.
IoT Insecurities
The beloved Alexa, a smart tv, and the newest cars all have one aspect in common: these products are considered a part of the “Internet of Things” (IoT) because they are devices connected to the internet or a network that can automatically collect and transmit data.
The Open Worldwide Application Security Project (OWASP) has reported on several top risks involving IoT, including weak passwords, outdated components, lacking update capabilities, and insecure privacy protections. Attackers can also use infected IoT devices as bots for Distributed Denial of Service (DDoS) attacks to disrupt or degrade a network.
Before you buy an IoT device, it’s a good idea to do some research before purchasing it, so as to help avoid purchasing a device with some known exploits. If the devices have update capabilities, be sure tto install these as soon as possible.
Ransomware
Ransomware is malware that affects devices or a network of devices by holding the system and its files “hostage” by demanding the user pay for access to their own devices and data. Victims can get ransomware through spam, malicious advertising, or forms of phishing. Fortunately, there are steps that you can take to mitigate the risks of cybersecurity attacks, such as maintaining backups, frequently updating systems, utilizing secure configuration settings, implementing antivirus software, and educating yourself about any potential risks. In the event that you or your company are a victim of a ransomware attack, the Cybersecurity Infrastructure and Security Agency (CISA) offers a Ransomware Response Checklist to help you respond and recover.
Pig Butchering Schemes
Pig butchering schemes occur when the attacker works to gain the victim’s trust before manipulating the victim to willingly invest in the attacker’s false investment scheme. Once that happens, the attacker disappears with their pilfered funds, leaving the victim broke and heartbroken.
You can distinguish pig-butchering schemes by noting if the attacker sends unsolicited messages, is an unknown contact, refuses to participate in video chats, requests financial information, or invites you to invest in their newest vague financial scheme, makes an irrational claim, or insists with urgency that you need to make the investment.
A good rule of thumb is to give yourself time and scrutinize the legitimacy of any supposed investment opportunities.
Phishing Scheme Variants
Phishing scams utilize online interactions to trick individuals into revealing sensitive information regarding themselves or their financial information. Smishing can occur through text messages, vishing through phone calls, or social media attacks. This can result in divulging sensitive information for future attacks, extortion, or an attempt at financial fraud of an individual or an organization.
These phishing schemes all have an underlying solution: do not interact with suspicious calls, text messages, emails, or fraudulent interactions online.
In Indiana, whether you are an organization experiencing a cyber incident or cyberattack, or you’re an individual who is a victim of identity theft, you can visit the Indiana Cyber Hub website’s Report a Cyber Incident page featuring a step-by-step process that’s easy to follow. The Consumer Protection Division of the Indiana Attorney General’s Office also offers a variety of free resources to help you. And the Indiana State Police Cyber Crime Unit also provides law enforcement officers to assist in criminal investigations involving the use of digital media as an integral part of the crime.
If you or someone you know is the victim of identity fraud or cybercrime, the FBI’s Internet Crime Complaint Center is another essential reporting tool to submit suspected cybercrimes. This helps to prevent internet crimes by promoting the sharing of information about threats.
Email Scams: It’s ‘OK’ Not to Click, Protect Yourself
Wednesday, September 20, 2023
Blog topics:
PERSPECTIVES FROM THE CAMPUS
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name "Perspectives From the Campus Series”, we invite experts -- immersed in the pursuit of educating their students -- to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the latest installment of this series, David Dungan, who serves as the Executive Director at the Center for Security Services and Cyber Defense at Anderson University, shares his expertise as it relates to the growing issue of email scams - including the tactics cybercriminals use to try and steal our personal and financial information and the steps we can take to protect ourselves.
 By David Dungan
By David Dungan
If we can agree that sending and receiving an email is one of the most effective and beneficial ways to communicate with one another (that’s ever been created...), it probably explains as to why it’s become a primary tool for cybercriminals to steal our money, credentials, and other sensitive information.
In 2020, people ages 21 and under lost roughly $71 million, and since January 2020, businesses have collectively lost $3.1 billion to business email compromise (BEC). Not only have email scams resulted in financial losses, but it has also resulted in identity theft and damage to the reputations of many companies. What’s more, it’s caused us to experience a collective lack of trust in using email to communicate with one another.
Tactics Involved with Email Scams
Attackers use various kinds of tactics within email scams: impersonation, email spoofing, malicious links, and fake invoices. Attackers often impersonate a third-party vendor, a customer, an employee, or a CEO to establish trust with the victim, or create a sense of urgency in an impersonation attack. This typically causes the victim to act quickly without considering that the email may be a scam.
Malicious links are links created to distribute malware like ransomware. Once the victim clicks on the link, they can be redirected to a spoofed website that the attacker created, recording the victim’s credentials if they input their login information, or downloading malware onto the victim's machine.
Invoice scams are when attackers send fake bills for goods or services that the victim never ordered. The victim may not look at the details of the invoice and pay it, potentially exposing confidential banking information. Instead of the money going to the real third-party vendor, the money is sent to the attackers.
How to Spot Email Scams
There are numerous tactics used to decipher email scams from legit emails. Follow these “red flags” to help you decipher the difference:
- The email claims that you must log into a website, or your account will be closed, with a link to an attacker-controller website.
- The email claims that your payment or personal information is invalid, and it must be sent to the attacker either through email or on a website.
- It attached invoices for a payment that you know you did not make.
- It conveys a sense of urgency or confidentiality.
- It claims that you could receive a government refund and asks for sensitive data such as a social security number, address, and banking information.
- It requires you to submit private data to obtain free products, coupons, or money.
How to Protect Against Email Scams
You can protect yourself and others from email scams by educating employees on the tactics used by scammers, installing email filters and email defenses, updating operating systems, and installing security software enforcing MFA (multi-factor authentication), as well as backing up data, and installing firewalls that contain web isolation technology.
As email scams continue to increase, it is important to use these practices to avoid becoming a victim of these attacks. You can also utilize an email provider that has fraud prevention built into the system.
There are also a wide range of free resources, best practices and tips that can help you stay safe, such as the Federal Trade Commission and CISA (Cybersecurity Infrastructure and Security Agency) offers an easy-to-use guide for recognizing and avoiding email scams that includes everything from get-rich-quick schemes and health and diet scams to important information on how the scams work with real world examples that you might have already seen in your inbox.
Remember, too, that it’s OK not to click on any link, especially if you’re not sure about the source, the offer or what someone is asking you to do. Cybercriminals are relying on you to act on your feelings -- such as curiosity and the desire to please others -- to get what’s yours and that’s true whether you’re at home, at work, or at school.
Social Engineering: How It’s Evolved & How to Avoid It
Wednesday, September 13, 2023
Blog topics:
PERSPECTIVES FROM THE CAMPUS
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name "Perspectives From the Campus Series”, we invite experts -- immersed in the pursuit of educating their students -- to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the latest installment of this series, David Dungan, who serves as the Executive Director at the Center for Security Services and Cyber Defense at Anderson University, shares his knowledge and expertise on how social engineering has evolved and the steps you can take to avoid it.
 By David Dungan
By David Dungan
Social Engineering manipulates people into doing one’s own bidding, likely by performing a specific task or giving up sensitive information. The attacker’s plan tends to follow a guideline of gathering information about the victim, establishing a relationship with the victim, exploiting the victim to do the attacker’s bidding, and then the attacker moves on to accomplishing their goal.
Before the Technology
Many reference the story of how the Greeks infiltrated Troy using the Trojan Horse or the biblical story of the snake tricking Eve as proof of social engineering.
However, the introduction of technology such as phones and computers has made this process easier by eliminating human interaction and allowing individuals to trick automated authentication processes.
Forms of Technology Exploitation
Phones were one of the first techniques to make the practice of social engineering easier through the removal of face-to-face interactions.Vishing is the process of social engineering using phones. Attackers will pose as individuals, such as a bank official, and will call or leave a voicemail message to lure the victim into sending sensitive information through social engineering. Smishing is another way attackers can socially engineer mass quantities of individuals through sending texts, posing as authentic entities with malicious links.
What's more, it's become a (very) big issue, as the Federal Trade Commission says nearly 200,000 people have been targeted this year alone. And, last year, people lost a total of $2.6 billion to imposter scams.
Phishing can target numerous individuals at once through a mass email. Phishing is where an attacker attempts to convince a victim into divulging information, such as tricking someone into thinking they won the lottery and need to provide sensitive information to claim their prize; or attackers may urge an individual to download malware onto their computer, masking the download as an important file or update.
Social Media
Social Media has made it easier to social engineer individuals through the collection of information on victims, different mechanisms to attack, and attackers being able to exploit a broader audience.
Many individuals often leave a digital footprint on social media, disclosing information such as their full name, city, country, birthday, etc. Attackers can use this information while researching a victim.
Additionally, attackers can harvest data by creating fake log-in pages for social media, collecting the victim’s username and password.
The Future of Social Engineering
Mitnick Security predicts deepfakes will be the newest technology to trick victims into giving up information by faking audio and video of real individuals. Additionally, they predict attackers will leverage social media credentials since numerous web applications will allow individuals to verify themselves through social media authentication measures.
We can protect ourselves against social engineering by not giving out personal information to unsolicited requests, not sharing information with individuals we do not know and trust, or on untrustworthy platforms. If you are skeptical of the legitimacy of a message, such as if the message were from the company it claims to be from, contact the company yourself and do not reply to the message. Similarly, do not open emails or text messages that do not seem legitimate or click on links or attachments in those emails/text messages.
Experts recommend if someone clicks on a malicious link or divulges personal information, they should notify the IT team (if applicable), disconnect the device from their network, change their passwords, scan the networks for malware, notify credit agencies of potential fraud, check for identity theft on bank statements and other financial statements, and contact the agency the attacker imitated to inform them of the incident.
Overall, social engineering is based on the same principles, just carried out through different means. It is meant to take advantage of the vulnerabilities of humans. Therefore, we need to consider the humans behind the computers when protecting against attacks through comprehensive user training and using spam filters whenever possible to prevent human contact with social engineering tactics. To learn more, the Cybersecurity and Infrastructure Security Agency (CISA) is a great resource that’ll help you make sense of it all, and better protect yourself against these types of attacks.
Three Ways Cybercriminals Target High School Students
Wednesday, September 6, 2023
Blog topics:
PERSPECTIVES FROM THE CAMPUS
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name "Perspectives From the Campus Series”, we invite experts -- immersed in the pursuit of educating their students -- to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the latest installment of this series, David Dungan, who serves as the Executive Director at the Center for Security Services and Cyber Defense at Anderson University, discusses three ways that cybercriminals use to target high school students and shares some helpful tips on keeping your digital life safe and secure.
By David Dungan
Whether you’re a senior, preparing for what’s ahead after you graduate, or you’re a freshman, who’s just trying to figure out where your first class is at, being a high school student is tough enough without having to worry about a cybercriminal stealing your personal information.
 According to a study, released earlier this year, found that a student’s personal information is valued at $1,010 on the dark web - that’s one student. The fact is, a cybercriminal can acquire and utilize a student’s credentials for a wide variety of goals, and this often makes high school students a target. Typically, there are three common ways cybercriminals will use to try and steal a high school student’s personal -- and financial -- information, including: botnets, ransomware attacks and impersonation attacks.
According to a study, released earlier this year, found that a student’s personal information is valued at $1,010 on the dark web - that’s one student. The fact is, a cybercriminal can acquire and utilize a student’s credentials for a wide variety of goals, and this often makes high school students a target. Typically, there are three common ways cybercriminals will use to try and steal a high school student’s personal -- and financial -- information, including: botnets, ransomware attacks and impersonation attacks.
- Botnets - Cybercriminals add high school students to a botnet by redirecting them to malicious links, promoting ,malicious software, or harvesting students' data in "free" online tools. These mechanisms infect the high school student's machines, making them part of a larger bot-network. Botnets can have repercussions for the user, such as having the user blocked from certain websites due to their account being connected to malicious activity or becoming a suspect for illegal activity.
- Ransom Attacks and Ransomware - Ransom attacks are schemes involving credentials or sensitive information of the user falling into the attacker’s possession, which the attacker uses as leverage to exploit that user. Some attackers may use ransoms to coerce students into using their parents’ credit/debit cards to pay the ransom. Ransomware attacks occur using malware that prohibits a user from accessing their own digital accounts, files, media, online storage, and other forms of data.
- Impersonation Attacks -- An impersonation attack is a general use term for methods of deception that allow a threat actor to gain access to information that would otherwise be inaccessible to them. Two types of impersonation attacks relevant to students include spoofing and form jacking.
- Spoofing is a type of impersonation attack that involves a threat actor pretending to be from an entity they are not, while form jacking involves an attacker stealing a user’s data through the user’s direct connection to a website or portal.
- Students are at the greatest risk of form jacking due to the sensitive nature of the information, shared, for example, when registering for school, as students frequently fill out documentation requesting their full names, date of birth, Social Security numbers, as well as family information, and other details related to such things, as jobs or even scholarships.
To protect yourself, high school students should begin safeguarding their internet usage by practicing good habits of digital security, such as:
- Never sharing personal information with anyone or any place you do not trust.
- Using secure web pages by searching for “https://” instead of “http://” in front of a web address.
- Web browsers will also display a lock in the web address bar to denote a secure web page.
- Ensuring the validity of unknown email addresses by checking with official sources first.
- If something seems illegitimate, contact the assumed sender to ensure they sent the email that was received.
- Using two-factor/multi-factor authentication.
There is no definitive way to absolutely prevent someone from becoming a victim of identity theft, but practicing cyber-safety goes a long way toward preventing and/or reducing the extortion of data, so as to help high school students focus on what matters most to them.
Password Breaches and Prevention - What You Need to Know
Wednesday, August 30, 2023
Blog topics:
 PERSPECTIVES FROM THE CAMPUS
PERSPECTIVES FROM THE CAMPUS
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name "Perspectives From the Campus Series”, we invite experts -- immersed in the pursuit of educating their students -- to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the third installment of this series, David Dungan, who serves as the Executive Director at the Center for Security Services and Cyber Defense at Anderson University, discusses some of the methods cybercriminals use to try and steal your personal and financial information and he’ll share his expertise on what you need to know to stay safe, whether you’re at home, at work, at school, or you're on social media.
By David Dungan
By now, with all the advancements we’ve made with cybersecurity, you might think we’ve figured out how to keep our passwords from being hacked.
Yet, for all of the progress that’s been achieved, passwords are bypassed through the use of password-cracking tools, scamming techniques, and other methods of social engineering. Too often, a cybercriminal only has to use some social skills for an unaware person to deliver the requested information effortlessly.
Social engineering attacks are difficult to circumvent due to the craftiness of modern attackers. These include tactics such as phishing, pretexting, baiting, and scareware. Let’s take a closer look at what we’re talking about, what you should look for, and some tips you can use to better protect yourself, including:
- Phishing
- Phishing attacks target victims for personal identifying information (PII).
- The goal is for the attacker to manipulate the victim into releasing crucial information critical to business security and personal security. This usually pertains to social media, finances, and other assets.
- Phishing attacks usually occur through email but can also be carried out through other communication-focused platforms. Smishing, or SMS phishing,is a branch of phishing that involves the attacker disguising themself as a reputable organization through text messages.
- Pretexting
- Pretexting is a social engineering attack where the attacker pretends to be a trusted official, family member, or friend of the victim. The attacker attempts to acquire background information on the victim to know some of their real-world connections and relationships to carry out their attack. Attackers can find this information online and on social media such as Facebook.
- Baiting
- Baiting is an attack used to persuade targets to fall for malicious media.
- Digital baiting refers to media sent over the internet, sent to victims, and marked as important documents or luring media files. These files are typically embedded with malware capable of harming a user’s device, as well as stealing personal information.
- Physical baiting involves the attacker providing a storage device such as CDs or USBs to a target hoping the target connects this device to their system. This would give the attacker access to private information of the company/individual, and potentially spread the malware across the network.
- Scareware
- Scareware is a tactic that uses fear to manipulate targets via phone calls, messaging, or online into disclosing private information, downloading hazardous material, or even visiting unsafe websites.
- Bad actors can either convince the target to release this information or simply extract critical data through the use of malicious software should the target downloads the malware. This is a huge issue for personal and business security since the stakes are always high.
The most strategic way of combating password breaches is by staying up to date on new methods cybercriminals use. Among the organizations that promote cyber-awareness include Cybersecurity Infrastructure and Security Agency (CISA) and the National Cybersecurity Alliance. These organizations provide timely updates on new cyber threats and tech updates. There are also articles out there, with some easy-to-follow reminders to help you stay protected whenever you're online.
A Bump In The Roadmap...
Wednesday, August 23, 2023
Blog topics:
Like many schools and businesses alike, we are constantly looking to improve our cybersecurity posture… keeping the ‘bad guys’ out is more and more of a challenge, with large-scale data breaches hitting the news almost daily.
During the fall of 2021, we partnered with one of our trusted vendors and completed a network security assessment as part of our network security roadmap. A few weeks later, we were running a trial of a next-gen antivirus solution in a few of our buildings, when we received an alert in the middle of the night that there was suspicious activity on our network. We investigated, found the affected PC, and remediated. The next night, another alert on a different PC. Another remediation. We decided to expand our two building anti-virus trial to all buildings for more complete visibility into what was happening. Night three, I was waiting. Sure enough, around the same time of night, another alert. Upon further investigation, we thought it was best to take the entire school district of over 10,000 students and 1,200 staff members offline as we and our vendor partners determined the extent of the intrusion.
If you’ve not had a discussion of what a total technology shutdown would look like in your district, I would highly encourage you chat with your administration team and include that information in your disaster recovery plan. For us, it was important to be the ones controlling access, as we were not sure what would come if the game of cat and mouse were to continue. While our teachers rely heavily on technology for their daily instruction, this event encouraged them to return to some of their earlier teaching practices and school remained open and teaching continued during this event.
The proactive nature of our ‘technology lockdown’ allowed us to control what services remained online during our investigation. Thinking back, I cannot imagine not having this option. Accommodations were made for some of the operational functions (payroll, bus routing, nutrition services) to continue. Telephones, security cameras, copiers, A/V systems all may be affected in the event of a true ransomware situation. As we were not in that situation, all of these systems were operational. A communications backchannel was established through our district’s mass communication system. All passwords were reset and had to be distributed to all staff and students in-person in an efficient manner. Over 13,000 stickers with new, temporary user credentials were strategically deployed. Schools utilized PA announcements in a way that they hadn’t in many years and went back to distributing printed copies of things that may have been emailed in the past. While it was important to let school families know that their students were not accessing technology at school, the messages could not be incredibly detailed as the investigation began. Families were informed that the access didn’t include the student information system.
While school life continued as normal as possible, the investigation involved conversations with a local partner recommended by the Indiana Department of Homeland Security and our school administration. At the conclusion of the investigation, it was determined that no sensitive files were accessed, and no ransomware was discovered on the network. It showed that the perpetrator seemed to attempt to use our network to make fraudulent purchases online, and most-interestingly, the initial access coincided with the date and time of our network security assessment. We engaged in a strategic restart of the network to minimize the risk and isolate any further attempts to compromise the network. After a few days, the district was back online with the next-gen anti-virus software fully in place.
Hearing of other districts’ incidents involving ransomware and encrypted files, I know we were fortunate in our case. In the weeks and months after our intrusion, many ‘what if’s…’ followed: What if this ‘system’ or that ‘tool’ was also affected, etc.? How would we take attendance if our student information system became inaccessible?
All of this helped us further re-shape our disaster recovery plan, and the year-long security roadmap we were following was accelerated to about five weeks with nearly total buy-in from our staff.
If you’ve not had a chance to develop a disaster recovery plan for your district, I would highly recommend you complete that. Many resources beyond the Technology Department need to be involved in the planning for and execution of such plan. The Indiana Cybersecurity website contains some great resources to incorporate into your plan. Purdue CyberTAP offers no-cost cybersecurity assessments, which we took advantage of last year. This assessment gave us additional ideas for our plan as well. IN-ISAC also publishes timely notifications of threats and vulnerabilities which you can sign up for here.
Dangers of USB Attacks: How You Can Protect Your Cyber Self
Monday, August 21, 2023
Blog topics:
 PERSPECTIVES FROM THE CAMPUS
PERSPECTIVES FROM THE CAMPUS
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name "Perspectives From the Campus Series”, we invite experts -- immersed in the pursuit of educating their students -- to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the second installment of this series, David Dungan, who serves as the Executive Director at the Center for Security Services and Cyber Defense at Anderson University, discusses the importance of protecting your personal information when it comes to USB devices and ports, as well as other forms of removable media.
By David Dungan
USB devices, CDs, SDs, and SIM cards make our lives easier in many ways, but it's important to understand the inherent vulnerabilities of these devices so you can keep your private information safe and secure.
One common attack relies on social engineering to infect devices. It starts with someone leaving a USB flash drive in common public places (even a parking lot), on someone’s desk, or it’s addressed to an individual with the hope that a person will plug it into their computer.
Call it curiosity or a desire to simply help someone, you might be tempted to insert the removable media to see who it belongs to, or to access the information (if they think it belongs to them), or if they need to plug in the removable media for a specific task. The problem is these devices act like a remote keyboard when the victim plugs them into their device. The removable media devices have pre-programmed keystrokes that can place malware on your computer, delete important files, open a backdoor for persistent access, and more.
Essentially, with a removable media attack or USB drop attack, the attacker can program the device to perform any actions that they would be able to perform, just as if they were sitting at your computer. You can protect yourself from this kind of attack by never plugging an unknown removable media device into your computer or mobile device.
Another common attack involves public USB ports that, more and more these days, are found in cafes, airports, and hotels. While these may be convenient if you’re traveling and your phone’s battery is running low, but you could be handing over your personal information directly to a malicious attacker. This type of attack works by modifying the port to include a device that will interact maliciously with your phone. A similar attack uses a malicious USB cable to steal private information.
To protect against attacks like these, never plug a phone into an unknown USB port and never use a charging cable that is not trustworthy. If you need to plug it into an unknown USB port, you can use a data blocker to prevent malicious devices from interacting with your phone. This data blocker works by not including the USB lines that transfer data in the port that connects to the suspicious device. It is important to plan ahead so that the next time you’re out in public and need a charge, you have your own charger or portable battery.
The bottom line is simple: all of us need to be wary of removable media that is not our own and take precautions whenever we’re plugging our devices into an unknown or, otherwise, suspicious USB port or charging station. If you want more information about these types of devices, Verizon and the National Cybersecurity Alliance also offers lots of great tips and best practices that you’ll find helpful.
Guarding Our School’s Digital Future: One Byte at a Time
Wednesday, August 16, 2023
Blog topics:
As a superintendent, I am always concerned about safety and security. Traditionally, that has meant protecting our students and staff members from physical harm. Unfortunately, now, it includes something that might not be on everyone’s radar but is crucial in today's digital age: the protection of computer data in K-12 schools. Just as we lock our classroom doors and set alarms for our schools, we need to secure our digital spaces. Think about it: schools are treasure troves of sensitive information. From student records to faculty details, all of it is vulnerable without the right protection.
First and foremost, tackling this behemoth requires a team approach. We can't leave cybersecurity to a single person. Creating a leadership task force is essential. This should include the sharpest minds in our school community: technology directors, network administrators, system administrators. These are the folks that understand the intricate details of our school’s digital backbone and can devise a plan to safeguard it.
As we chart the course of securing our schools, we need to ensure support at all levels: hardware, software, people, and processes. It's like piecing together a jigsaw puzzle – all parts need to fit perfectly. And while doing so, we must ensure that our school environment remains just as welcoming and safe as before, not turning it into some high-security tech fortress that makes its use too cumbersome.
There is a lot to this effort and it sounds expensive. But here's the silver lining: there's help available. Schools can utilize state-funded grants to help invest in cybersecurity solutions like KnowBe4. And trust me, this is an investment that promises significant returns, not just in terms of data safety but in the peace of mind of parents, staff, and students.
One of the best roadmaps to follow for this journey is the 18 CIS Critical Security Controls. These controls are a golden standard in cybersecurity, a comprehensive guide to building a robust infrastructure. By adhering to these, we're not just throwing on a security blanket; we're constructing a digital fortress, brick by brick.
And, let's not forget the human element in all this. No matter how strong our walls are, there's always the risk of someone inadvertently leaving the gate open. To prevent this, it's imperative to run email phishing campaigns to educate and test staff on how to recognize threats. Additionally, routine tabletop exercises can simulate potential security scenarios, ensuring that when (not if) a threat occurs, our team knows exactly what to do.
Without question, the digital era has brought countless blessings to our educational system. But with these benefits come risks. Hence, the importance of guarding our school’s digital future, one byte at a time!
Press Your Luck – No Whammy, No Whammy…How a Game Show from the 80’s Got Our District Moving in the Right Direction for Data Privacy and Protection
Wednesday, August 9, 2023
Blog topics:
 By Dan Layton
By Dan Layton
If you read the title above and your mind instantly wanders to the corny animations of Whammy and Sammy stealing all the money from contestants on what was the most technically advanced gameshow in 1983, your mind works like mine, and you are probably wondering what a gameshow has to do with creating a robust data privacy and protection system for your school district.
Like many of you reading this post, I knew my district was taking several steps to ensure we protected the information we had collected. We only collected what we needed, we had a robust firewall, we had hired a good network team, we had an authenticated wireless network, and we, although most of us didn’t know it well, threw the acronym FERPA out there from time to time when it came to sharing information about our students.
There was obviously more to it, but all in all, nothing bad had happened and we were doing just fine as a district. We had gotten by with a less than stellar strategy: hope. We simply hoped nothing bad would happen that we would undoubtedly react to the best we could. We were not taking crucial preemptive steps to ensure privacy and protections. We had our ores in the water, but we were all rowing in different directions at different speeds. With the ever-evolving landscape of AI enabled security threats and information protection, it became more and more evident to me, “Hope was not a strategy.” Hope was not going to train our staff and students, hope was not going to read privacy policies, hope was not going to negotiate contracts from a data protection perspective on behalf of our young learners. We simply needed something more, but what was it that we needed.
This brings me back to the gameshow. Michael Larson, an ice cream delivery man from Ohio, took the same “hope is not a strategy” approach after watching other contestants on Press Your Luck simply hope to avoid a whammy to win, “big bucks.” The game, if you have never seen it, consists of an electronic board with 18 shuffling electronic tiles of money and whammies. If you land on money, you collect. If you land on a whammy, you lose your money and your turn. Larson started to video record every episode and repeatedly play them until he eventually found a pattern in which tiles #4 and #8 always had big dollar amounts and extra spins, never a whammy. He taught himself how to consistently land on those two tiles. He then used what was left of his savings to buy a plane ticket to Los Angeles to try out for the show. He went to California with a strategy other than hope.
At the time of filming, the most money ever won on a gameshow was around $36,000. Michael Larson with his preparation and strategy, walked away with over $110,000 in cash and prizes. Larson knew hope was not a strategy and he did everything he could to make sure he was ready for anything that came his way on the show. He would eventually take over 40 consecutive turns on the board without hitting a whammy, shattering the previous record of 8. At first CBS thought Larson had cheated and refused to pay up but, after review, realized he had simply put in the work and beat what they thought was a foolproof system.
The lesson from Press Your Luck is a mirror for all of us, as we journey through the digital realm and create a learning environment that is safe, secure, and trusted by our students, staff and community of stakeholders. We can hope or we can prepare. Lucky for us, the blueprints for preparation have already been developed by many groups from CoSN’s Trusted Learning Environment, the Indiana Executive Council of Cybersecurity (IECC) to best practices from the MS-ISAC.
I knew the trajectory we needed to take. I knew we had to start with step one of this strategy; we had to create urgency around data privacy and protection with key decision makers and those on the front lines. Luckily, I had a great story to tell about Michael Larson and a game plan for how we would accomplish our goals of ensuring we could run school and protect the data of our students and staff.
SCHOOL’S IN: STAYING SAFE ONLINE IS WHAT EDUCATION IS ALL ABOUT
Wednesday, August 2, 2023
Blog topics:
 By Brad Hagg
By Brad Hagg
As students are preparing to transition back to school for the 2023-2024 school year, it’s a great time to reflect on not only the incredible digital tools that they are using to accelerate learning each day, but also how important it is that students are making wise choices when using these powerful solutions.
First, students and caregivers should be very careful about what information they are sharing and with whom they are sharing it. As families complete registration processes all over the state, it would be very easy for a cyber threat actor to imitate school personnel or send messages to steal valuable personal or financial information.
If you receive an unsolicited request for personal information or a form of payment, reach out to your school through a separate phone call or email before sharing any information to confirm that it is, indeed, your local school making the request.
Next, it is important to remind students to practice excellent digital citizenship when engaging with others online. A good rule of thumb for students (and for everyone) is to ask yourself if you would say what you’re about to type or text if the person was standing right in front of you. Another good tip is to ask yourself if you would make the post if you knew a grandparent was going to read it.
Just like we tell our children not to talk to strangers, students shouldn’t have an online conversation unless they are absolutely sure they know who they are talking to, and that it is someone they trust. Students should always show any message that seems strange or offensive to an adult that cares about them. Online predators may threaten to hurt relatives of a student they are talking to if the student discloses the conversation. They may also threaten to disclose embarrassing or uncomfortable information about the student. We should make sure that students understand that these situations are definitely when they need to reach out to a trusted adult for help. Talking about situations like these with students before they occur helps us prevent them from causing harm.
When family members communicate openly with each other and plan ahead for how to use these digital tools, they can build some excellent memories and be positioned for a great year of learning! For more tips, don’t forget to take a look at all of the incredible resources in the NEW Cybersecurity for Education Toolkit 2.0. Download it today!
Why Is Cybersecurity Essential For Local Businesses?
Wednesday, July 19, 2023
Blog topics:
 PERSPECTIVES FROM THE CAMPUS
PERSPECTIVES FROM THE CAMPUS
One of the strengths of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the colleges, universities, and other institutions of higher education throughout our state. Hence the name "Perspectives From the Campus Series”, we invite experts -- immersed in the pursuit of educating their students -- to offer their knowledge for finding solutions in cybersecurity that benefit all Hoosiers.
In the first installment of this series, David Dungan, who serves as the Executive Director at the Center for Security Services and Cyber Defense at Anderson University, shares his perspective on why cybersecurity is an essential tool for local business owners.
By David Dungan
The world is digital. Present-day business infrastructures depend on technology that provides simplicity but may be easily exploited. Small businesses are subject to cyberattacks, usually due to deficits in their security infrastructure.
The Cybersecurity & Infrastructure Security Agency (CISA) stresses that small businesses have valuable information, such as health, financial, and personally identifiable information on employees and financial data of customers. Small businesses are usually more vulnerable and at higher risk of cyberattacks compared to larger firms due to fewer resources for cybersecurity than larger businesses.
Small businesses should upgrade their security infrastructure to decrease the odds of a successful cyberattack.
Cyberattacks are usually viewed as external threats, but this may not always be the case. Most cyber-related incidents actually occur within the company itself, whether it was done on purpose or on accident. International Business Machines (IBM)classifies these threat actors into four different categories:
- The Pawn is an innocent employee, unaware of the implications of their digital actions. Essentially, this employee could be easily duped by outside threats. If they were to receive an inauthentic email from their district manager, asking for personally identifiable information, this employee will mistakenly send the requesting entity the information asked of them.
- The Goof is an employee that does not properly follow company security protocols. This individual may enter restricted parts of the company, or they may take their work home, risking the exposure of business information to outsiders.
- The Collaborator is the “undercover employee.” This employee has ulterior motives, which mainly involve working with other organizations that may be competitors.
- The Lone Wolf is the employee who works alone against the company, perhaps for financial gain or malicious intent. The situation becomes worse if this person has an elevated privilege level and access.
Common Cyber Threats to the Workplace
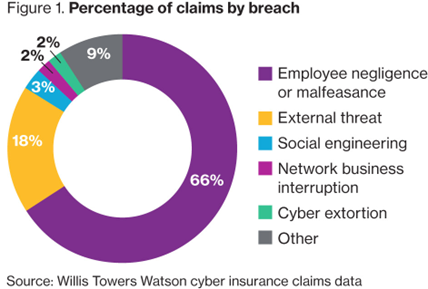 (World Economic Forum, 2017)
(World Economic Forum, 2017)
How Can Local Businesses Start Preparing?
There are a variety of ways an organization can start improving its security infrastructure, including:
- Employ qualified cybersecurity professionals
- Utilize identification cards
- Install/Upgrade security cameras if they are more than five years old
- Assess the cyber awareness of employees on a regular basis
- Update staff on any new hires
- Define company limitations and designate no-access/restricted zones
There is always more an organization can do to improve its security capabilities. It is great to have security procedures in place, but those protocols must be continuously revised and updated to ensure a secure working environment.
There is no way to guarantee against a cyberattack, but businesses can upgrade their security posture, making it more difficult for attackers to access and breach their assets.
Plan for the Inevitable: The Importance of Cyber Response Plans
Wednesday, July 12, 2023
Blog topics:
 By Joel Thacker
By Joel Thacker
Cybersecurity threats have become an increasingly pervasive concern in today's digital landscape. The ever-evolving nature of cyber threats necessitates a proactive and comprehensive approach to protect critical infrastructure and sensitive data. Cyber incidents can range from data breaches and network intrusions to ransomware attacks and beyond. The consequences of these incidents can be devastating, leading to financial losses, reputational damage, and disruption of essential services. By having a well-crafted Cyber-Incident Response Plan (CIRP), organizations can better prepare, respond, and recover from such incidents.
One key aspect of a CIRP is establishing clear roles and responsibilities for incident response. This ensures all stakeholders understand their roles and can swiftly and effectively respond to cyber incidents. Organizations can minimize confusion and improve coordination during high-pressure situations by defining these roles in advance. CIRPs should also include a robust communication strategy outlining how the information will be disseminated internally and externally during a cyber incident. Timely and transparent communication is crucial to maintaining public trust and confidence and mitigating the potential impact of the incident. Of course, all plans should have alternative methods of communication should technology be temporarily interrupted.
Prevention is always better than resolving after the fact, and a well-designed CIRP should prioritize proactive measures such as continuous monitoring, vulnerability assessments and threat intelligence sharing. By implementing strong cybersecurity controls, organizations can detect and address potential vulnerabilities before they are exploited, reducing the likelihood and impact of cyber incidents.
The evolving nature of cyber threats requires organizations to regularly update and test their CIRPs to ensure their relevance and effectiveness. Cybersecurity is rapidly changing, and organizations must stay informed about emerging threats, trends, and best practices. Regular reviews and updates to the CIRP help address new challenges and incorporate lessons learned from previous incidents.
In today's interconnected world, a cyber incident can have far-reaching consequences. A robust Cyber Incident Response Plan is paramount for organizations to effectively mitigate risks, respond promptly and recover swiftly from cyber incidents. The Indiana Department of Homeland Security encourages all organizations, regardless of size or sector, to prioritize developing and implementing a comprehensive CIRP. By doing so, we can collectively strengthen our cybersecurity posture and safeguard our critical assets from evolving cyber threats.
You can access a host of critical resources by visiting the Indiana Cyber Hub at in.gov/cybersecurity.
Make the Call: Celebrate National Cell Phone Courtesy Month by Protecting Your Mobile Security
Wednesday, July 5, 2023
Blog topics:
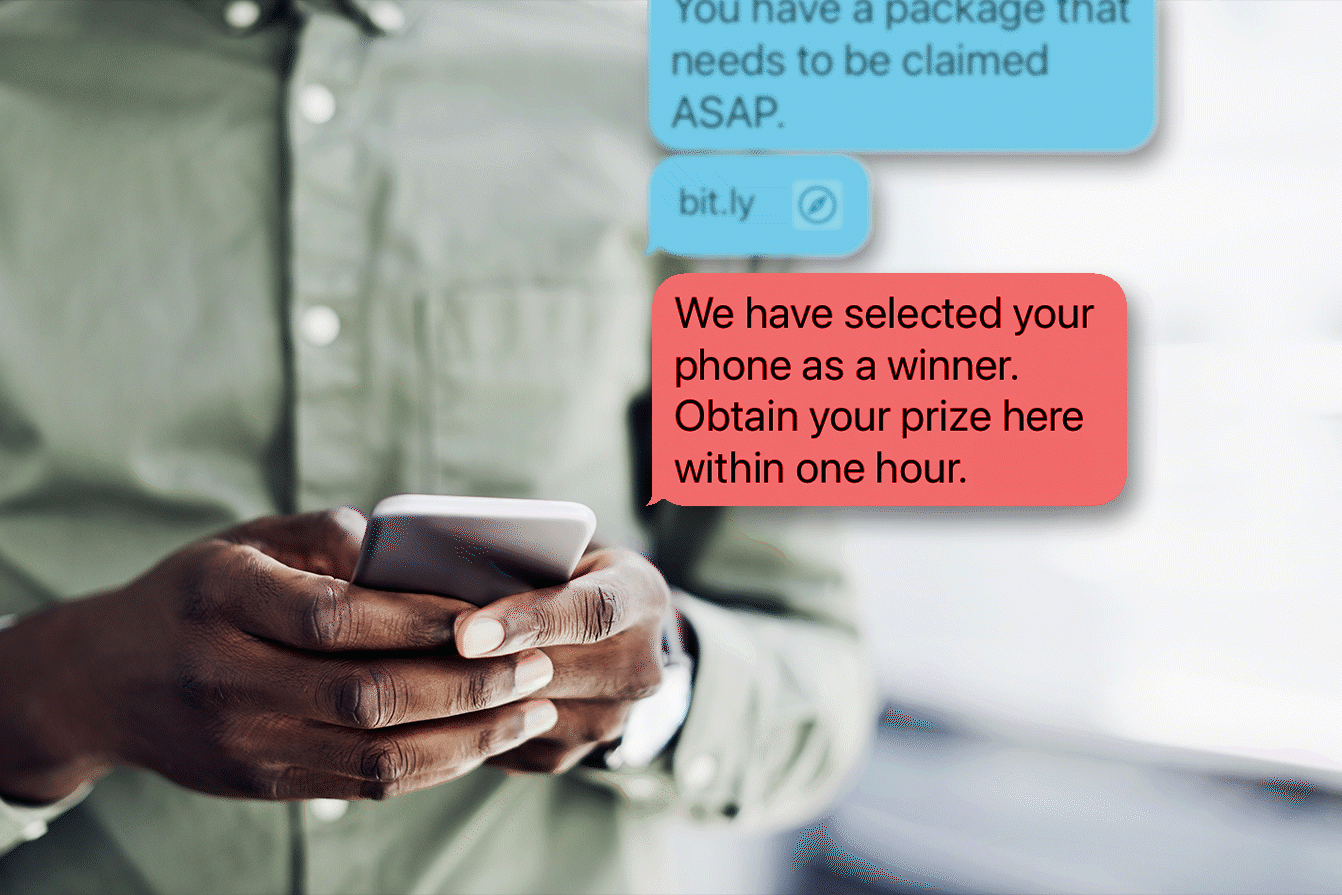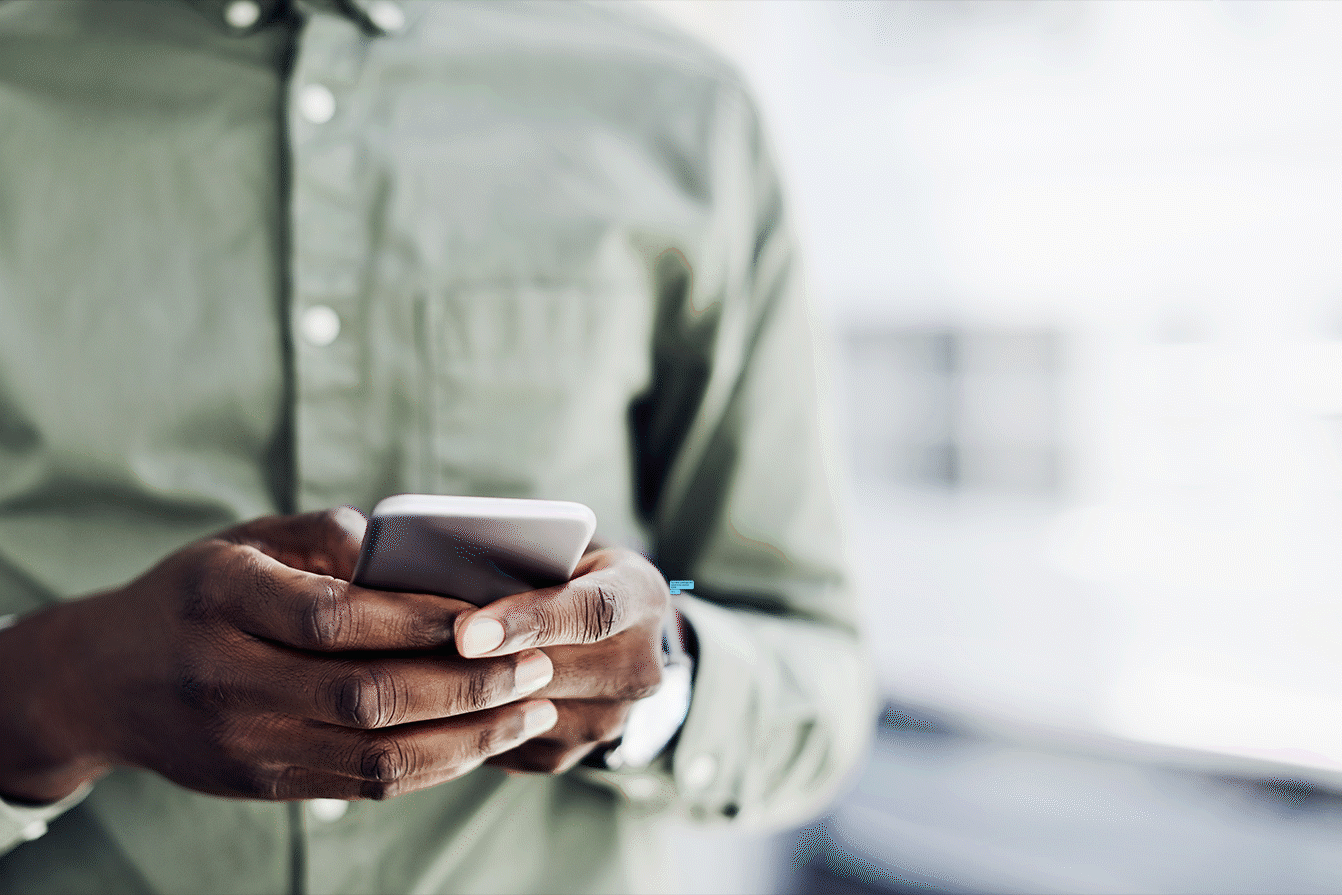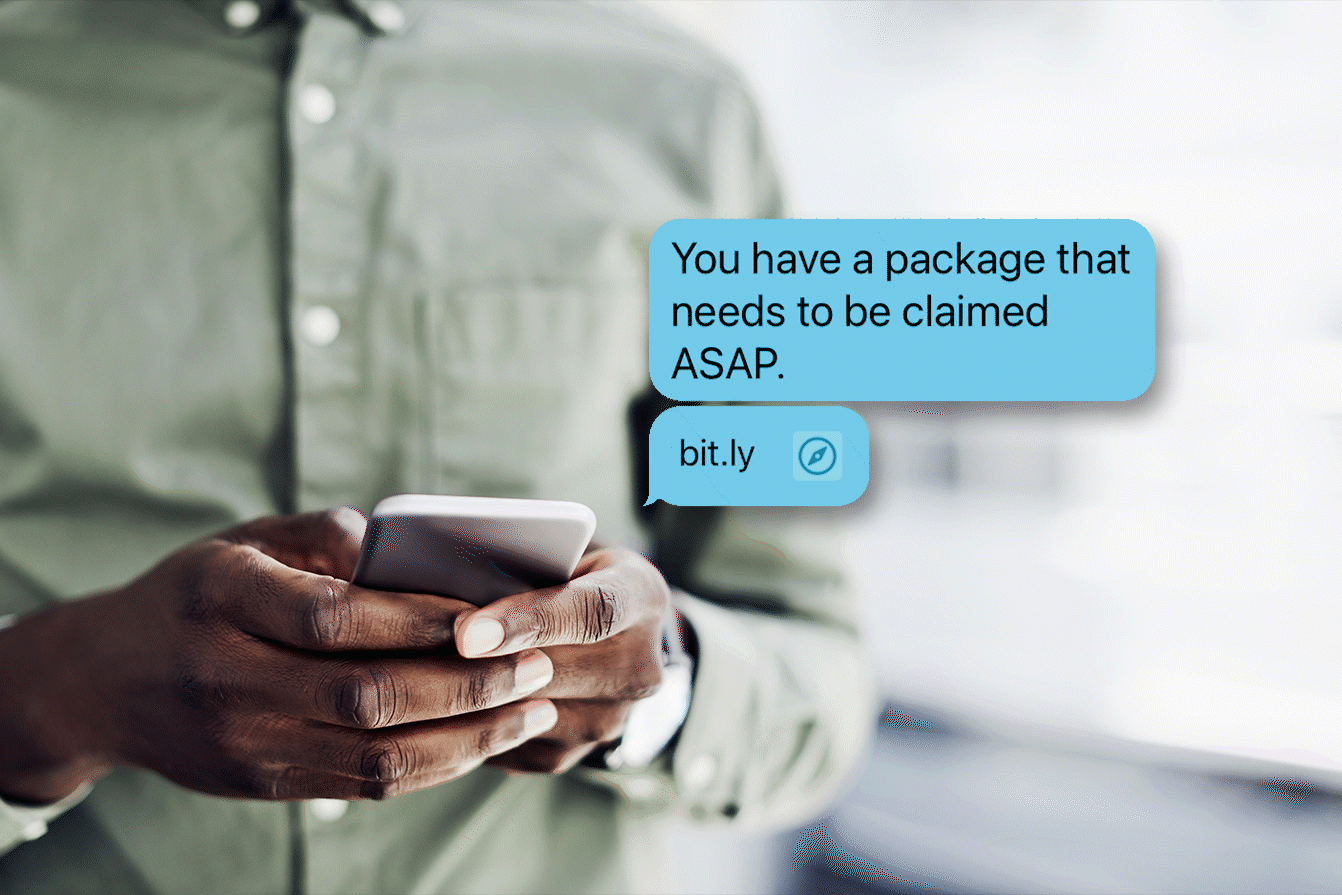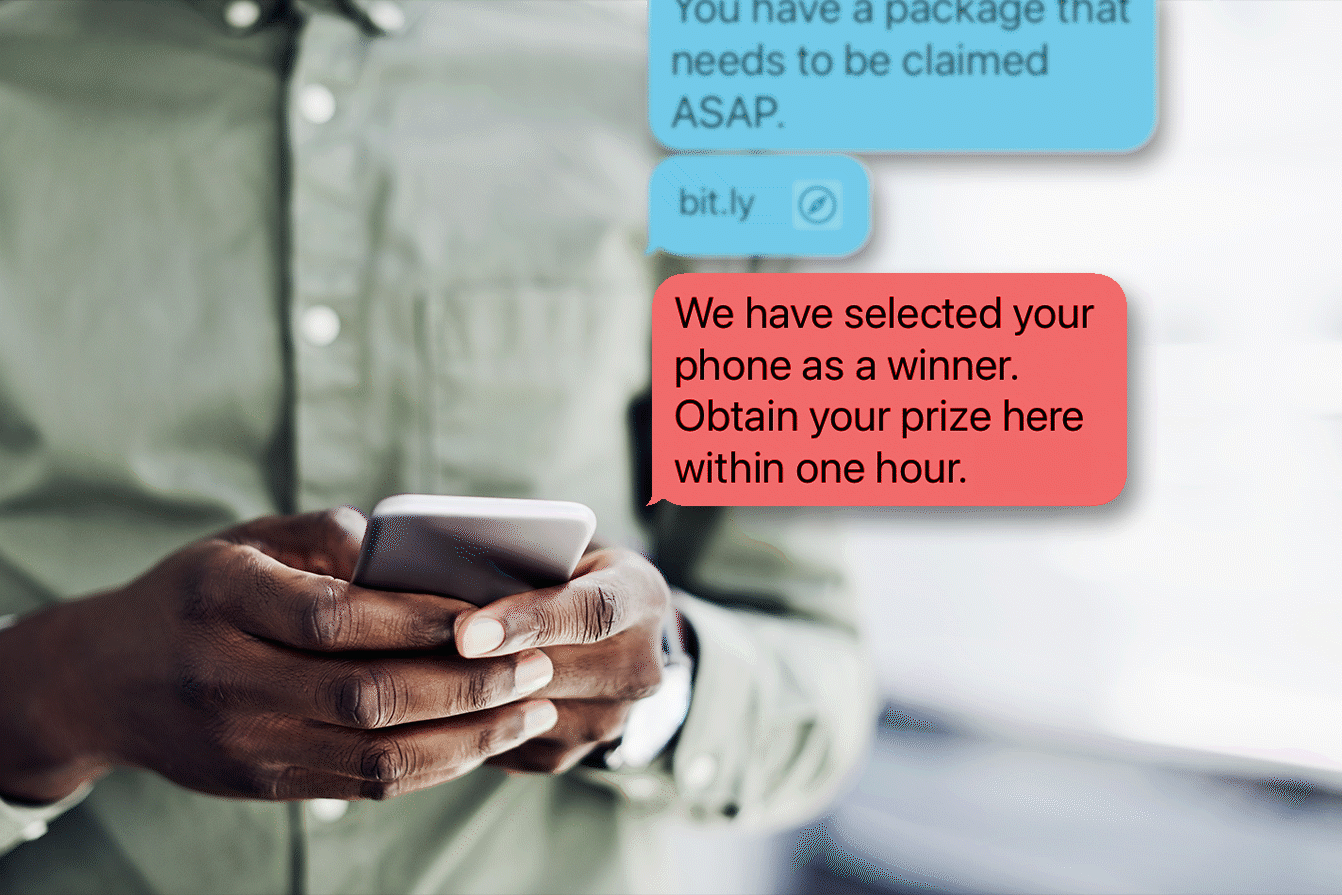 Welcome to National Cell Phone Courtesy Month! As we celebrate the benefits and convenience of mobile technology, it's crucial to also address the challenges and risks that come with it. In this digital age, cyber scams have become increasingly prevalent, targeting unsuspecting individuals through their cell phones, smart phones and mobile devices. As we highlight cell phone courtesy, let's also explore the importance of staying vigilant and safeguarding ourselves against cyber scams, defining some of the cyber jargon you’ll hear, and learning exactly what these different attacks mean.
Welcome to National Cell Phone Courtesy Month! As we celebrate the benefits and convenience of mobile technology, it's crucial to also address the challenges and risks that come with it. In this digital age, cyber scams have become increasingly prevalent, targeting unsuspecting individuals through their cell phones, smart phones and mobile devices. As we highlight cell phone courtesy, let's also explore the importance of staying vigilant and safeguarding ourselves against cyber scams, defining some of the cyber jargon you’ll hear, and learning exactly what these different attacks mean.
Phishing Attacks
Phishing has been around since the early e-mail days, as far back as the mid-1990’s. Today, phishing attacks have become among the most dangerous forms of what we consider to be a cyberthreat. In fact, 36 percent of all security breaches begin with a phishing attack. Mobile phone users are most often at risk to these attacks because of the ease of access that comes with using these types of devices. Scammers send text messages or emails that appear to be legitimate, impersonating real people and organizations (or both) and they’re requesting personal information. This can include everything from an email (or text message) letting you know that you have a package that’s being delivered (when you haven’t ordered anything) to something, such as an email with a confirmation from PayPal (involving a transaction you didn’t make). All of it looks to be surprisingly real. However, when you click on the link and/or enter your information, instead, your money and your personal information is headed into the hands of a cybercriminal as part of a scam.
To protect yourself, here’s some helpful tips to keep in mind, including:
- Being cautious of unsolicited messages. Be skeptical of any message asking for personal information or urging you to click on a suspicious link.
- Verifying the sender's legitimacy. It’s always a good idea to contact the organization directly using their official website or contact information to confirm the authenticity of the message.
- Installing anti-phishing software. There are apps for your phone or mobile device that can help protect you from phishing attacks, easily found by searching ‘anti phishing’ on the app store.
Fake Apps and Malware
Fake apps and malware pose a significant threat to mobile phone users. Cybercriminals can create their own apps that look very similar to the real deal. To avoid falling prey to a hoax:
- Stick to legitimate app stores: Download apps only from trusted sources, such as Google Play Store or Apple App Store.
- Read reviews and check app permissions. Before downloading an app, read user reviews and verify the permissions it requires.
- Install reliable mobile security software. Be sure to invest in a reputable antivirus or security app (that’s within your budget) that scans for and prevents the installation of malicious apps.
Vishing
Vishing, or voice phishing, involves scammers making phone calls impersonating representatives from banks, government agencies, or other organizations (include non-profits) to extract personal information. Protect yourself from vishing attacks with these precautions:
- Be cautious of unsolicited calls: Don't provide personal information over the phone unless you initiated the call or can verify the legitimacy of the caller.
- Verify caller identity: Ask for the name, department, and contact number of the caller. Then independently contact the organization to verify their authenticity.
- Register your number on the National Do Not Call Registry: This can help reduce the number of unwanted telemarketing calls.
- Remember, a verified organization, such as a bank or a credit union, will never ask you to read out a credit card number, social security number, or other sensitive information over the phone.
As we embrace National Cell Phone Courtesy Month, let's prioritize our digital well-being and protect ourselves from cyber scams that target mobile phone users. By being vigilant, following best practices, and staying informed about the latest scams, we can minimize the risks associated with mobile technology.
Together, let's make cell phone courtesy about more than just politeness; let's make it about security and ensuring our digital experiences are safe and enjoyable. Stay cautious, stay informed, and enjoy the benefits of your cell phone responsibly!
Happy National Cell Phone Courtesy Month!
Fun, Friends, and Firewalls: Celebrate National Social Media Day with Secure Sharing
Wednesday, June 28, 2023
Blog topics:
 Today, social media is a large part of all of our lives. It allows us to connect with others, share our stories, and express ourselves. However, with the large reach of social media, it’s very important to prioritize our safety and protect ourselves from various dangers. This week, as we celebrate National Social Media Day on June 30th, it’s a great time to explore and share with you some helpful tips and strategies to keep yourself safe in the digital realm.
Today, social media is a large part of all of our lives. It allows us to connect with others, share our stories, and express ourselves. However, with the large reach of social media, it’s very important to prioritize our safety and protect ourselves from various dangers. This week, as we celebrate National Social Media Day on June 30th, it’s a great time to explore and share with you some helpful tips and strategies to keep yourself safe in the digital realm.
- Guarding Personal Information: One of the best ways to keep yourself safe is to carefully manage your personal information. It’s always a good idea to avoid putting sensitive information online, including your home address, phone number, and/or any financial information. The Department of Justice cautions that sharing sensitive information with people you don’t know personally is one of the biggest risks to your security online. Also, be sure to restrict what apps can see using privacy settings; that’ll help in keeping your data more secure.
- Using Strong and Unique Passwords is one of the fundamental steps to keeping yourself safe on social media and making sure your accounts are protected. Having the same password over multiple sites, using passwords that are common, and not utilizing a good combination of numbers, upper and lower case letters, and symbols puts you at risk of losing control of your account, and giving a cybercriminal access to sensitive information.
- Stranger Danger and Parental Controls: Be sure to look into the parental settings for your accounts, and make sure you have careful control over who can see what your kids and teens are posting. Be careful, too, sending messages to accounts you don’t know well and be mindful of whose friend requests you accept. It’s important for your children understand and are aware of the dangers of strangers online and how to keep themselves safe as well.
- Think Before You Share: When you post, consider the potential consequences. Be careful of what’s in the background of pictures, opinions that you’re making public, or if there’s any information in your post that could give a stranger or someone who “claims” to be your friend an opportunity that could hurt you. For example, making sure that a picture of a new car doesn’t show the license plate is good cybersecurity practice. If that post is public or gets outside of your circle of close friends, anybody can use it to identify you and your address in most states.
- Cyberbullying and Online Harassment: Try as they might to apply standards for the content that’s posted, social media sites contain lots of messages and posts that are intended to harass people. Limiting who can see each post you make is a good preventative measure but utilizing the ‘block’ function to stop interacting with someone who is causing you stress is an important countermeasure to keep in mind. Support platforms on the sites can also help out; it allows you to reach out to the platform’s administration and report the person, making it beneficial for everyone.
- It’s OK to be Skeptical: Hackers use benign and unassuming attacks to get access to your data. For example, QR codes have been efficient and even fun ways to share things with customers and friends in public. However, since humans can’t check where the QR codes will actually take them before they scan it, there can be malware that’s dangerous if it’s downloaded to your phone. The FBI is warning citizens about criminals putting malicious codes over real ones. Being extra careful and practicing a healthy amount of suspicion for things online and relating to your online devices is a great way to keep yourself safe.
By staying safe whenever you’re online, National Social Media Day is a cause for celebration and connectivity with loved ones and your shared experiences. Enjoy!
It’s Not Goodbye, It’s See You Later
Monday, June 19, 2023
Blog topics:
 It’s Not Goodbye, It’s See You Later
It’s Not Goodbye, It’s See You Later
When I started my role as Cybersecurity Program Director for the State of Indiana, I started with an Executive Order from the Governor and a blank piece of paper.
Skip forward 6+ years and now we have two comprehensive (and successful) strategies and a highly visited cyber hub website with a multitude of easy-to-use cyber resources that are focused and used by a number of sectors and businesses who need the help.
How were we able to accomplish all of this? It was through the efforts of the dedicated members of the Indiana Executive Council of Cybersecurity, who have all donated hundreds of hours and millions of dollars in the way of expertise, services, and resources for the benefit of all Hoosiers, governments, and businesses.
It has been an amazing 6+ years serving the State of Indiana in this role. And while today will be my last day with the State of Indiana after 15 years of service, I am so excited to continue serving Hoosiers in my new role with USDHS CISA. The best part of my new role is that I’ll be able to continue my work in cybersecurity to help Hoosiers, in a federal capacity, as the first cybersecurity state coordinator for Indiana with the USDHS Cybersecurity and Infrastructure Security Agency (CISA).
As I look back over my years in this role and my philosophy on this blog, I’m happy to know that many of our readers have provided feedback that has only reinforced things about cyber that I think are missed by the movers and shakers of our world, such as:
- Cyber can be fun! National Selfie Day? National Hug Your Pet Day? Why not connect that to cyber? There is no reason to just focus on the doom and gloom of cyber all the time. I know for me; I learn better when training makes me laugh. I learn better with cartoon illustrations and metaphors. We have been able to accomplish this not just with our blog, but our social media as well.
- Cyber can be simple. A famous Einstein quote that has been at the heart of my core work philosophy since college is “Out of clutter, find simplicity.” I am always leery of anyone in cybersecurity who can only explain something in a very technical way. I truly believe that if someone understands something, he/she should be able to explain it in laymen’s terms. Cybersecurity sounds scary, but it can be demystified.
- Cyber is very personal. I truly believe that if we only focus on our organization’s interests then it will take 100 times longer for people to understand that good cyber hygiene is not only important to keep an organization secure, but (more importantly) it is important to keep YOU and YOUR family safe. Beating the drum on losing weight to help lower the cost of an insurance premium will never get me to eat healthier, BUT if you talk to me about how losing weight will improve my quality of life and allow me to see my grandkids, NOW you have my attention. Talking about cybersecurity shouldn’t just be focused on protecting our state or local government, it should also focus on our homes and families.
Now the great thing is that we have many guest bloggers in the coming months who will keep the blog going. I would be remiss to not call out our amazing communications manager, David Ayers, who is the backbone of our website and communication channels. His dedication will keep important information coming your way, even with me gone. If you have any ideas, don’t hesitate to contact him at dayers@iot.in.gov.
I am truly looking forward to being out and about more with the local governments, organizations, and individuals who want to learn how to better protect themselves, their communities, and our state. So, this is certainly not goodbye by any measure. You will see me around Indiana, and I will always be happy to help in any way I can.
Continue to follow my cybersecurity journey on LinkedIn and/or Twitter.
Cybercrime in the Real Estate Market: Protecting Yourself as a Seller or Buyer
Wednesday, June 14, 2023
Blog topics:
June is National Homeownership Month, and whether you’re a Hoosier homeowner, or you’re looking to buy or rent, there are a few things to keep in mind to make sure that your experience is safe and secure.
Houses are expensive, so the profits for cybercriminals are ripe. No matter whether you’re buying or renting, there are some online scams you’ll want to avoid that could cost you thousands of dollars.
Recently, a couple in California, looking to rent a home, found a property on Facebook. It seemed great, except that the property was not for rent. The real owners had no idea that the property was on the market and the fake landlord had gotten the pictures of the inside of the home from Zillow. Luckily this couple went to the property and knocked on the door, saving themselves thousands.
The FBI routinely provides information, warning American families of homeowner scams. In 2021, the increase was a staggering 64 percent compared to 2020 in real estate-related cybercrimes.
Wire fraud is just one of the other types of scams out there relating to the real estate sector. Some 13,500 people fell victim to this type of scheme, costing them more than $213 million dollars. All too often, scammers will try to sell a property they don’t own, such as what happened with the couple from California.
As a homeowner, you can search for your own property online right now on sites like Facebook Marketplace or Apartments.com to see if someone is trying to list it as their own and report it. As a buyer, be sure to read through the contracts carefully to protect yourself and your investment. It could save you from such things, as a lockout clause, and doing your due diligence could help you avoid sending money to a scammer.
When it comes to agreeing to a wire fraud transfer of funds, the American Land Title Association (ALTA) recommends all homebuyers and sellers double check all wire instructions with the title company. Each wire should be verified in person or on the phone with an authorized company representative. The ALTA website also features a brief video with additional information on ways to properly securing your property against other types of scams.
When it comes to reporting these types of scams, you can contact the FBI. If it involves a fraudulent rental listing, the Federal Trade Commission offers resources that can help you.
Best of luck in your journey to securing a home that’s truly your own!
WAIT UNTIL YOU’RE HOME TO SHARE THOSE VACATION PHOTOS
Wednesday, June 7, 2023
Blog topics:
Summer is finally here! It’s time for a vacation for a lot of Hoosiers, wherever that might be.
Whether you’re a family of five, traveling with friends, or it’s just the two of you getting away for the weekend, there’s some steps you can take to protect yourself from being the victim of a cybercrime (or a break-in).
And it starts by not sharing the details of your getaway with everyone on social media while you’re out having fun.
Vacations are one of those things we want to share with our family and friends. Everything from what we’re planning and when we’re leaving to where we’re at and showing them all the fun, we’re having. In that moment, we don’t always realize that those posts can get out to the wrong people, and it tells the world that no one’s at home.
According to the FBI, most burglaries happen between June and August and roughly half of those are committed by someone who knows the victim. A lot of that comes from the fact that close to 40 percent of the people who are on vacation are posting about it before the trip is over.
Of course, as with a lot of things, there are some steps you can take to protect yourself before you leave and there’s a few ways that’ll help you stay safe online during your trip, including:
- Never Posting Your Upcoming Travel Plans -- As tempting as it may be, the worst thing you can do is post details of any upcoming travel plans. First, you’ll be giving thieves a heads-up as to when you’ll be gone, and second, they could be waiting for you when you arrive on vacation. Only your closest friends and family should know (offline) about your travel plans.
- Waiting Until You’re Home to Do a ‘Photo Dump’ -- It’s a good idea (once you start sharing some of your memories) to mention the vacation is over and that it’s good to be back home.
- Disabling Geolocation Tags on Your Posts -- Being less specific and providing less information also makes it a little safer to share (anything not related to your trip) on Instagram or Facebook.
- Don’t Tag Other People -- If you return from vacation early and your friends or anyone you were traveling with, are still gone, be sure that you don’t tag them in any photos or status updates.
- Wait until everyone is back home and then tag them (if they want to be tagged).
- Additionally, enable the Facebook tag review feature if you don’t want to be tagged in photos or want to approve any tag before something is posted.
Even with the best approach, the other reason for being cautious when you’re online involves the fact that there are people, who might be described as a “friend of a friend”; someone you might not know at all or have ever met is the person who’s not SO good and is the one who breaks into your home. Members of law enforcement have reported how this can happen. So much so, that when some would-be burglars have been apprehended, they admitted knowing the person, who was targeted, was on vacation.
If you have a need to share, I get it, as sometimes we need to stay in touch with our family or close friends if we’re traveling, there’s a couple of things you can do. On Instagram, you can create a close friends list, so that whatever you share, is seen only by those you trust. You can also do the same thing on Facebook. The other option is to go offline and create a group text and share your photos and what you’re doing as a way to stay connected. I’ve found, too, that when I get back home, I’m able to create a journal that provides some great vacation memories!
Stay (cyber) safe out there and have fun!
The Attack on Colonial Pipeline: What We’ve Learned & What We’ve Done Over the Past Two Years
Wednesday, May 31, 2023
Blog topics:
Reprinted with the permission of the Cybersecurity and Infrastructure Security Agency (CISA), today’s blog first appeared on CISA’s website in a bylined piece, published on May 7, 2023, by Jen Easterly, who serves as the Director at CISA and Tom Fanning, who is the Chairman and CEO of Southern Company and serves as Chair of the CISA’s Cybersecurity Advisory Committee.
 By Jen Easterly and Tom Fanning
By Jen Easterly and Tom Fanning
Today marks two years since a watershed moment in the short but turbulent history of cybersecurity. On May 7, 2021, a ransomware attack on Colonial Pipeline captured headlines around the world with pictures of snaking lines of cars at gas stations across the eastern seaboard and panicked Americans filling bags with fuel, fearful of not being able to get to work or get their kids to school. This was the moment when the vulnerability of our highly connected society became a nationwide reality and a kitchen table issue.
The good news is that since that event, the Biden-Harris Administration has made significant strides in our collective cyber defense, harnessing the full power of the U.S. government to address the full spectrum of the threat. At the Cybersecurity and Infrastructure Security Agency (CISA), we have been laser focused on improving resilience across our Nation’s critical infrastructure. Recognizing that organizations need a simple way to access actionable and timely cybersecurity information, we developed stopransomware.gov to provide a central location for alerts and guidance for businesses and individuals. Recognizing that only cohesive collaboration across government will scale to meet the threat, we launched the Joint Ransomware Task Force with our FBI partners to orchestrate the federal government’s response to the epidemic of ransomware. And recognizing the need to bring together industry, government, and internal partners and tear down siloes that create gaps for the adversary, we established the Joint Cyber Defense Collaborative (JCDC) — a concept born out of the U.S. Cyberspace Solarium Commission on which one of us served as a Commissioner — to catalyze a community of experts on the front lines of cyber defense — from across the public and private sectors — to share insights and information in real time to understand threats and drive down risk to the nation.
 Since its establishment, the JCDC led the national response to one of the most extensive software vulnerabilities discovered; played a central role in CISA’s Shields Up campaign to protect critical infrastructure from potential Russian cyber-attacks; and, along with our partners at the Transportation Security Administration (TSA), brought together more than 25 major pipeline operators and industrial control systems partners to strengthen security practices to safeguard the operational technology networks critical to pipeline operations, efforts that complement the Security Directives TSA issued in the aftermath of the attack on Colonial Pipeline. Separately, with the support of Congress, we expanded our capability known as “CyberSentry” which enables heightened visibility into and more rapid detection of cyber threats that could target our nation’s most critical operational technology networks. Finally, we worked to help organizations of all sizes and skill levels prioritize the most impactful cybersecurity investments with the introduction of cybersecurity performance goals, or CPGs.
Since its establishment, the JCDC led the national response to one of the most extensive software vulnerabilities discovered; played a central role in CISA’s Shields Up campaign to protect critical infrastructure from potential Russian cyber-attacks; and, along with our partners at the Transportation Security Administration (TSA), brought together more than 25 major pipeline operators and industrial control systems partners to strengthen security practices to safeguard the operational technology networks critical to pipeline operations, efforts that complement the Security Directives TSA issued in the aftermath of the attack on Colonial Pipeline. Separately, with the support of Congress, we expanded our capability known as “CyberSentry” which enables heightened visibility into and more rapid detection of cyber threats that could target our nation’s most critical operational technology networks. Finally, we worked to help organizations of all sizes and skill levels prioritize the most impactful cybersecurity investments with the introduction of cybersecurity performance goals, or CPGs.
While we should welcome this progress, much work remains to ensure the security and resilience of our critical infrastructure in light of complex threats and increasing geopolitical tension. The U.S. Intelligence Community issued a stark warning of a potential future in its recent Annual Assessment, noting that “If Beijing feared that a major conflict with the United States were imminent, it almost certainly would consider undertaking aggressive cyber operations against U.S. homeland critical infrastructure…China almost certainly is capable of launching cyber-attacks that could disrupt critical infrastructure services within the United States, including against oil and gas pipelines, and rail systems.”
We cannot afford to dismiss this warning. We must do everything today to be prepared for such a scenario. First, we must ensure that the technology that underpins the services that Americans rely on every hour of every day is safe and secure. For too long, we have sacrificed security for features and speed to market, leaving us increasingly vulnerable, with the burden of security placed on those least able to bear it. As listed in one of the core pillars in the President’s National Cyber Strategy we need security to be built into the creation of new technology—as a foundational imperative—rather than bolted on at the end requiring continuous security updates from consumers.
Second, we need to prioritize cybersecurity at the highest levels. The days of relegating cybersecurity to the CIO or the CISO must end. CEOs and Boards of Directors must embrace cyber risk as a matter of good governance and prioritize cybersecurity as a strategic imperative and business enabler.
Third, we must continue to invest in the JCDC model of persistent and proactive operational collaboration between government and industry where the default is to share information on malicious cyber activity, knowing that a threat to one is a threat to all.
Finally, we need to normalize cyber risks for the general public with the recognition that cyber-attacks are a reality for the foreseeable future. We cannot completely prevent attacks from happening, but we can minimize their impact by building resilience into our infrastructure and into our society. We need to look no further than our Ukrainian partners for an example of the power of societal resilience.
These changes are not easy, but we need to hold ourselves accountable to the hard lessons learned from two years ago. Are we going to make the choices that will lead us to a secure, resilient, and prosperous future or are we going to allow inaction to dictate a future in which our national security and our way of life hang in the balance? We have proven that it can be done but only if we act now…together.
Older Americans and Cybersecurity: It’s More Important Than Senior Coffee
Wednesday, May 17, 2023
Blog topics:
Here in Indiana, when it comes to the month of May, there’s a lot going on.
- You’ve got kids of all ages, teenagers, and young adults, too, finishing the school year and moving onto to the next stage of their life.
- Couples are headed down the aisle and, seemingly, almost all of us knows someone who’s getting married. Am I right?
- And, of course, at the end of the month, everyone (regardless of where we’re at) will be celebrating being “Back Home Again in Indiana”. By then, you’ll be one of the more than 350,000 people at the track to experience the “Greatest Spectacle in Racing”. Or you’ll be kicking off your Memorial Day weekend with a picnic or party of our own.
Regardless of where in the Hoosier state we’re at, some of the people who’ll be with us for that grad party, or who will be gathering together, as friends, to share each other’s company for yet another trip to the Indianapolis 500 (that always begins with a cup of that much-appreciated senior coffee), is why we have another reason to celebrate the month of May and that’s because it’s Older Americans Month.
OK, it’s fair to say that you might not have had that one on your calendar. But I think you’ll agree that It’s important and some of the “why” that’s true might surprise you (HINT: it involves cybersecurity).
One of the ways, every day, we pay tribute to older people is by helping to protect them, especially as it regards their personal and financial information when they’re online. Cybercrime cost Americans over the age of 50 nearly $3 billion last year and that’s an increase of 62 percent from 2020, according to the FBI’s 2021 Elder Fraud Report.
In fact, the number of victims could be much higher, as seniors are also less likely to report fraud, says the FBI. This is supported by figures from the Federal Trade Commission, which show that while 44 percent of younger people in their twenties reported losing money to fraud, only 20 percent of those who are in their seventies did the same.
The cyber-related risks show up in everything from fraudulent phone calls, phishing attempts in emails and text messages to social media messages and shopping scams and all of it is designed, specifically, to trick someone who’s older out of their savings.
To help keep that from happening, the National Council on Aging suggests there are four steps that seniors can take for improving their personal cybersecurity, including:
- Don’t click on links in emails from unfamiliar senders. Be wary of strange or unexpected messages, even if they’re from people you know.
- Don’t open any attachments unless you know the sender and were expecting them to send the information to you.
- Ignore any unsolicited phone calls and “robocalls.”
- Don’t respond to or click on pop-up windows on your phone or computer.
The FBI, Federal Trade Commission (FTC) and the Cybersecurity Infrastructure and Security Agency (CISA) offer a great deal of free resources to help you avoid being the victim of an online scam or identity theft.
If the worst happens and you believe that you’ve been the victim of a cybercrime, visit the Indiana Cyber Hub website and go to our “Report a Cyber Incident” page -- there you’ll find all of the steps you need to take to protect yourself and begin recovering.
Best of all, these resources are all FREE. That’s less than even the best deal you’ll find for that senior coffee!
Just What the Doctor Ordered: How Cyber is Protecting Healthcare
Thursday, May 11, 2023
Blog topics:
When it comes to cybersecurity, hospitals, and health care organizations -- supported by the dedicated people, who work tirelessly to take care of all of us -- represent the very definition of critical infrastructure that exists within our communities.
As we prepare to celebrate National Hospital Week, it’s important to know that right here in Indiana, there’s a free-to-download resource -- Healthcare Cyber in a Box -- that is already making a difference when it comes to providing small- to medium-sized healthcare institutions with the ability to create more of the critical systems that are needed for keeping their operations secure. At the same time, it is helping to protect their patents and preserve both their digital, as well as physical, well-being.
The Healthcare Cyber in a Box Toolkit provides an organization with three levels of expert guidance -- basic, intermediate, and mature -- involving 10 critical areas of cybersecurity. This guidance also provides specific, actionable information on how a health care organization can address each area of concern, everything from email protections, system access and asset management to laptop and workstation protections, as well as information about what specific threats each of these areas seeks to protect against.
Created with the expertise of a group of cybersecurity and information security professionals, who work in the healthcare profession in Indiana, the Toolkit is part of an ongoing initiative to help educate and support all Hoosiers. It is also an example of the work that’s been achieved over the past six years by the Indiana Executive Council on Cybersecurity (IECC). The IECC is responsible for creating the cybersecurity policies and initiatives in Indiana, on behalf of all Hoosiers, businesses, and local government.
The initiative for bring about these protections began in 2019, with the adoption of the Section 405(d) Health Industry Cybersecurity Practices: Managing Threats and Protecting Patients. The 405(d) Working Group and the Health Sector Coordinating Council, together with numerous provider, government, and industry volunteers are to be commended for making this a reality.
At a time when all institutions face greater threats from cybercrime, it’s difficult for a lot of organizations to possess all of the necessary resources, when it comes to people, processes, technology, and the budgets, to establish even basic protections. For healthcare, this is especially critical, given the fact that hospitals, clinics, and doctor’s offices are responsible for maintaining and processing some of the most sensitive data, both as it relates to a patient’s personal and financial information, in addition to their medical records.
* * *
 Another new cyber resource that’s available for healthcare pros is the “Cybersecurity for the Clinician” Video Series.
Another new cyber resource that’s available for healthcare pros is the “Cybersecurity for the Clinician” Video Series.
It is a free-to-download cybersecurity training video series that explains in easy, non-technical language the basics for how cyberattacks can affect clinical operations and patient safety, and how clinicians can do their part to help keep healthcare data, systems, and patients safe from cyber threats without losing time away from their patients.
Developed by the Health Sector Coordinating Council (HSCC), clinicians, students, professionals, and institutions with training programs are welcome and encouraged to download the series on YouTube or in eLearning format at: https://www.healthsectorcouncil.org/cyberclinicianvideos/. For a preview, go to: https://youtu.be/awIJ8kSP-Ak.
Just as we’re always searching for a cure to whatever it is that’s ailing us, it’s encouraging to know that we’ve got some talented and dedicated people, right here in Indiana, who are working on cybersecurity solutions to keep us all safe.
Cryptocurrency: A Different Kind of Coin Collecting
Wednesday, April 19, 2023
Blog topics:
In case you missed it on the calendar, it’s National Coin Week!
OK, to be fair, unless you’re an numismatist, it’s not necessarily something that a lot of us might take the time to celebrate. That being said, it did get me to think about where we’re at, as a society, with how we’re using coins as a part of our everyday life, and how bitcoin -- also referred to as cryptocurrency or crypto -- fits into the conversation.
To begin with, if you’ve been to a concert or sporting event lately, you’ve discovered that the one thing you don’t have to worry about forgetting when you leave the house is cash. And it’s not because you don’t have any money to spend, rather it’s because the venue or stadium (even at a lot of local high schools) doesn’t accept it as a form of payment.
Instead, we now have to remember to stop at an ATM before we go anywhere and paying (for a lot of things) with the change we’ve saved up is not necessarily an option either, as a lot of businesses have decided to go “cashless”. They’ve discovered it’s easier for us to pay with a credit or debit card, or we pay online (using our phone or mobile device) with Apple Pay. There’s even “Kohl’s Pay” (which I’m told is not to be confused with Kohl’s Cash).
As all of this has been going on, cryptocurrency is continuing to emerge as one more way people and companies are using as a legitimate form of payment and/or as an investment.
If you’re wondering what kind of “coin” we’re talking about, consider:
- According to Pew Research, approximately 16 percent of Americans use cryptocurrency in some shape, form, or fashion and it’s estimated that almost 70 million people use Blockchain wallets worldwide to store their cryptocurrency.
- Between 2012 and April 2023, the price of Bitcoin has gained 127,310 percent (from $22 per USD for $1 million worth of the token to $28,030).
Of course, it’s important to keep in mind, as someone who works in cybersecurity, crypto is also regarded as the preferred method of payment cybercriminals use when demanding payment from small businesses and local government, even schools, as part of their committing a cybercrime, either by stealing data or money or both. According to the FBI, cryptocurrency investment fraud increased 183 percent from $907 million in 2021 to $2.57 billion in 2022.
If you’d like to learn more about cryptocurrency, including how it works and the types of scams to be aware of, visit the website for the Federal Trade Commission. It’s a good place to start to understand some of the basics, along with some of the risks.
Seeing how there’s approximately 22,932 cryptocurrencies worldwide, it’s safe to say it’ll be a little while yet before we stop collecting coins, or feel as though we need to trade in our piggy banks for a digital wallet that’s filled with all of our money.
Backing Up Your Data: More Than Just a “Plan B”
Wednesday, March 29, 2023
Blog topics:
When it comes to our everyday life, there’s always a few things that we know we need to do, but try as we might, even with the best intentions, we struggle with making the time to getting it done (at least, like we should, right?).
One of things that you could say that fits into that category is backing up our data. And there’s a lot out there -- from everything that’s on our phones, laptops, and mobile devices, all the way down to the files we have at work and the precious photos we have saved, seemingly, everywhere!
Friday, March 31st is World Backup Day. It’s a perfect time to “celebrate” by making sure that just as we lock our doors at night, we’ve taken a few simple steps to protect ourselves digitally. For some, it’ll be a new experience, as 21 percent of people have not backed up all of the data on their computers. And even if you’re tech savvy, it’s important to keep in mind that nearly 30 percent of data loss cases were caused by accident.
That being said, here’s five great tips to help protect your data, including:
- Set it and forget it. Cloud-based storage and external hard drives both give you the option to set up automatic data backups on a recurring basis. This way, even in case of emergency, you won’t have to worry about the last time you backed everything up.
- Redundancy is key. Having your data stored in multiple storage spaces will keep it more secure, especially if one storage space fails. (For example, if your external hard drive is lost or broken or you don’t have the internet to access your cloud data.).
- Choose the right option for you. There’s no one-size-fits-all approach when it comes to data backup.
- External hard drives are a physical unit you plug directly into your computer. They’re relatively inexpensive, and they can be used with a variety of devices so you can access your data from anywhere.
- Cloud-based storage, meanwhile, is completely digital. It can be used across multiple devices, and there are even some free options highlighting some of the best practices to follow.
- Protect against cyberattacks. Unfortunately, the increase in technology use has also caused an increase in cybercrime. Backing up your data helps secure your information if your device becomes compromised. Additionally, you’ll want to make sure you’re running the latest antivirus software on all of your devices and systems (if you’re at work).
- Don’t be afraid to ask for help. Data backup can be overwhelming, especially if you’ve never done it before. However, it’s important to take these steps before it’s too late. If you’re unsure of what you’re doing, reach out to that tech-savvy friend for help. There’s also a lot of resources online, in the way of tutorials, that you can download or use as reference to use as a guide. And in case you need it, there are also some data recovery software tools that are free to use.
Who knows, with a little work, here and there, backing up your files will give you an opportunity to enjoy all over again (and keep secure) some of those precious photos!
Protecting Your Credit is Easier Than Filling Out Your Bracket
Wednesday, March 22, 2023
Blog topics:
It’s safe to say that National Credit Education Month isn’t likely to generate the kind of excitement a lot of us experienced last week, as we filled out our brackets for “March Madness” (especially as we were trying to figure out which of the #13 seeds were going to pull an upset, right?).
But it’s important for you to know that when it comes to protecting your identity and managing your money (especially when you’re online), you’ll want to follow a good game plan, because cybercriminals are out there using a full-court press to try and get you to commit some costly turnovers.
According to the FBI’s Internet Crime Report 2022, 800,944 complaints of cyber-crime were reported to the FBI by the public -- a five percent decrease from 2021 -- but the total potential loss increased from $6.9 billion in 2021 to more than $10.2 billion in 2022. Here in Indiana, in 2022, there were 11,682 complaints, with losses totaling $73.6 million.
Fortunately, there are some great (and FREE) resources Hoosiers can use to help stay safe, including the Consumer Protection Division of the Attorney General’s Office -- featuring a variety of interactive tools on its website to help protect you from being a victim of identity theft. And while it’s true that you cannot avoid the risk completely, you can benefit from using some of the resources that are out there to protect yourself and learn more about what you can do to educate yourself and your family.
If you need assistance, the Attorney General's Identity Theft Unit provides investigative services to help in the prosecution of identity thieves. The Identity Theft Unit is committed to reducing incidents of identity theft around the state by providing free educational resources, as well as information on how to “freeze” your credit and block unwanted calls from telemarketers. The site also offers links to information from the Identity Theft Resource Center, including the steps you can take to recover your identity, as well as protect your business.
Because cybercrimes also involve different forms of cyber incidents and cyberattacks, such as ransomware, malware, denial of service, among others), as well as fraud and other violations of privacy, you’ll want to be sure and visit some of the other pages on this website -- known as the Indiana Cybersecurity Hub -- including the steps you need to take if you have to report that you’ve been the victim of a cybercrime -- including the information you need to share if you work in local government.
Another resource (also FREE) is the Federal Trade Commission. The site offers everything from helpful tips on how to protect yourself against identity theft to knowing how to tell if someone has stolen your identity.
At a time when it can take less than a minute to withdraw money from an ATM or transfer thousands of our hard-earned dollars electronically, you might be interested to know that credit is something that was first used in the 1520’s -- defined as a term that came with a mix of different origins, including “belief, trust” and was also described as “a loan, [a] thing entrusted to another”, as well as a past participle of credere "to trust, entrust, believe".
Whatever the circumstance that you find yourself in, it’s good to know that there’s help out there to keep who we are - along with our credit - safe and secure, and that’s still got to be easier than figuring out who’s going to win all of these basketball games!
Toolkit Offers Hoosier Small Businesses Free Cybersecurity Resources to Stay Protected
Wednesday, March 15, 2023
Blog topics:
We hear the stories all the time, but most people think “that would never happen to me” or “I’m not important enough to be hacked”. Cybersecurity threats are very real for any business – but small businesses are increasingly big targets for cybercriminals. Verizon‘s 2021 Data Breach Investigations Report shows that 46% of data breaches impacted small and midsize businesses (defined as businesses employing less than 1,000 individuals). So even the small businesses need to be aware of their cyber risk!
What makes a small business a target? They have valuable data! Do you take payment via credit card? Do you allow for bank payments? Do you have business information for partners, suppliers, buyers, etc.? Small businesses collect a lot of very valuable data without even thinking about it. As businesses increase their digital footprint, pivot to more online sales, or store more customer or business data, this threat will continue to grow.
Small businesses are highly vulnerable to cybersecurity threats, as they often lack the resources and expertise to implement robust security measures. But the repercussions for cybersecurity threats are large:
- Disruption of Operations: A cyberattack can disrupt the operations of a small business, leading to downtime and loss of productivity. This can have a severe impact on revenue and can cause delays in fulfilling orders.
- Damage to Reputation and Customer Following: A data breach can easily damage the reputation of a small business. Customers may lose trust in the business and may choose to take their business elsewhere. Small businesses can also lose access to their social media platforms making ruining their digital profile and losing their earned customer following.
- Legal Liability: Small businesses can face legal action if they are found to be responsible for a data breach. They can be held liable for damages resulting from the breach, including compensation for the affected parties, regulatory fines, and legal fees.
- Compliance Issues: Small businesses that handle sensitive data are required to comply with certain federal regulations. Failure to comply with these regulations can result in penalties and fines.
Cybersecurity threats can have a significant impact on small businesses. It is essential for small business owners to take proactive steps to protect their businesses from cyberattacks.
Understanding your small business’ cyber vulnerability and mitigating cyber threats are not easy tasks. But putting in the effort now to protect your business is worth it! The Indiana Economic Development Corporation’s (IEDC) Small Business Development Center program offers a no-cost, ready-to-implement toolkit to provide Hoosier small businesses with easy to understand and ready to use resources that can help avoid or reduce the impact of cyber incidents. The IEDC engaged the Global Cyber Alliance to create a unique toolkit for Indiana small businesses interested in understanding the basics of cyber hygiene and mitigating cyber risks as well as finding organizations to help with training and cybersecurity implementation.
The Indiana Small Business Development Center also offers no-cost business advising, training, referrals, and a library of cultivated tools and resources to help a business succeed, from startup through to sale or retirement. You can find more information on the cybersecurity resources available through the Indiana SBDC program here or visit any of the 10 regional offices located throughout the state.
Celebrating International Women’s Day: Lifting Up the Next Generation of Women in Tech in Indiana
Wednesday, March 8, 2023
Blog topics:
 By Lieutenant Governor Suzanne Crouch
By Lieutenant Governor Suzanne Crouch
Although half of Indiana’s workforce is female, just over a quarter of the people performing tech jobs are women, the 4th largest tech worker gender gap in the nation.
Some may see this as a bleak statistic, but I see it as an opportunity for our state to grow and position itself as the perfect place for women to begin their tech careers.
According to the Girl Scout Research Center, 74% of teenage girls are interested in pursuing a career in STEM. In just a couple of years, they will be ready to step into the workforce of this currently male dominated field. And once they do, it is important that we attract them to Indiana.
Enticing people to our state starts by reminding people of all the unique opportunities and activities available in Indiana. As Lieutenant Governor, I oversee a portfolio of agencies including the Indiana Destination and Development Corporation (IDDC). IDDC is dedicated to promoting, branding, and telling Indiana’s authentic story to both attract and retain businesses, talent, students, and visitors to our state.
By utilizing the “IN Indiana” branding at your business, in public art or with #INIndiana on your social media posts, you are helping share the story of Indiana, which will attract more people from across the country to want to come visit, including prospective women in tech.
But once people find their way to Indiana, it is important that we work to ensure that they feel connected and supported while living here and can plug into common interest groups.
One group that is doing just that is Government Women In Technology (GWIT), a State of Indiana affinity group that supports, advocates and motivates women in technology. Founded in 2020 by Anushree Bag, GWIT now has over 100 members from 35 state agencies who gather to share their knowledge, serve as mentors, and empower one another to take risks and navigate an impactful career in technology.
The work being done by GWIT is vital to the success of our state and is building a strong foundation for future generations. I am optimistic that building a culture of support within the tech community, especially for the women who work in this field, will encourage this next generation to come to Indiana for college, for their careers and for their lives.
During Women’s History Month, I challenge you to take a step in supporting the next generation of women in tech. Whether that be by joining an organization like GWIT, volunteering for a local elementary school’s STEM club or becoming a mentor for a local student who is interested in the tech field. By taking these steps, each of us can help close the gender disparity gap in the Indiana tech industry.
JCDC FOCUSED ON PERSISTENT COLLABORATION AND STAYING AHEAD OF CYBER RISK IN 2023
Thursday, February 16, 2023
Blog topics:
 Reprinted with the permission of the Cybersecurity and Infrastructure Security Agency (CISA), today’s blog first appeared on CISA’s website in a bylined piece, published on January 26, 2023 by Eric Goldstein, who serves as the Executive Assistant Director for Cybersecurity at CISA.
Reprinted with the permission of the Cybersecurity and Infrastructure Security Agency (CISA), today’s blog first appeared on CISA’s website in a bylined piece, published on January 26, 2023 by Eric Goldstein, who serves as the Executive Assistant Director for Cybersecurity at CISA.
In 2021, CISA and our partners across government and the private sector created a new kind of partnership organization — the Joint Cyber Defense Collaborative (JCDC). While our model is still evolving, we collectively demonstrated how persistent collaboration and frictionless engagement can yield benefits in addressing exigent risks like the Log4Shell vulnerability and potential cyber activity resulting from Russia’s full-scale invasion of Ukraine. However, collaborating around immediate risks is necessary but not sufficient. We must also look over the horizon to collaboratively plan against the most significant cyber risks that may manifest in the future. This proactive planning is foundational to JCDC, as first envisioned by the Cyberspace Solarium Commission and then codified by Congress.
To advance this critical aspect of our work, CISA and our partners are proud to announce JCDC’s 2023 Planning Agenda. This Agenda is the first of its kind — a forward-looking effort that will bring together government and the private sector to develop and execute cyber defense plans that achieve specific risk reduction goals and enable more focused collaboration. We will continue to expand the breadth and depth of our partnership to maximize both the completeness and impact of these planning efforts.
Through a rigorous process that included input from subject matter experts and our government and private sector partners, we have developed a Planning Agenda focused on three topic areas: systemic risk, collective cyber response, and high-risk communities.
- While all organizations are at risk of cyber intrusions, we know that certain elements of the ecosystem can be abused by malicious actors to achieve widespread impacts. To reduce these types of risk at scale, we will convene key partners across the following efforts:
- Understand and mitigate risks potentially posed by open source software (OSS) used in industrial control systems
- Advance cybersecurity and reduce supply chain risk for small and medium critical infrastructure entities through collaboration with remote monitoring and management, managed service providers, and managed security service providers
- Deepen operational collaboration and integration with the Energy Sector, in partnership with the Department of Energy
- Identify approach to enhance security and resilience of edge devices for the water sector
- Over the past several years, government and the private sector have significantly advanced our processes and approaches for incident response, but our plans and doctrine have not kept up. JCDC will lead an effort to update the National Cyber Incident Response Plan, in close coordination with the Federal Bureau of Investigation and other partners, which will include articulating specific roles for non-federal entities in organizing and executing national incident response activities.
- Malicious cyber actors do not only target critical infrastructure or businesses; to the contrary, we know that high-risk communities, such as civil society organizations that support journalists, and cybersecurity researchers are routinely targeted by adversaries seeking to undermine American values and interests. JCDC will lead collaborative planning efforts with key non-government organizations, government, and industry stakeholders to develop a cyber defense plan for civil society organizations who are at high risk of being targeted by foreign state actors.
In the coming weeks, we will kick off our planning efforts on OSS and scaling cybersecurity to support small and midsize critical infrastructure and state, local, tribal, and territorial entities. The remaining priorities for cyber defense planning efforts will commence in the following months.
Through these planning efforts, CISA and our partners across government and the private sector will take steps to measurably reduce some of the most significant cyber risks facing our country and deepen our collaborative capabilities to enable more rapid action when the need arises.
This level of proactive planning is new; we’ll learn as we go, and we’ll be transparent about our successes and our continued areas of growth, informed as always by the input and feedback from each of our partners in this critical work. We will also maintain flexibility to undertake urgent planning efforts as the risk environment changes, recognizing that agility is foundational to our shared success.
JCDC is a public-private cybersecurity collaborative that leverages new authorities granted by Congress in the 2021 National Defense Authorization Act to unite the global cyber community in the collective defense of cyberspace. CISA welcomes all critical infrastructure organizations and entities with cybersecurity expertise and visibility to participate in our collaboration efforts. For further information about JCDC, email cisa.jcdc@cisa.dhs.gov.
Celebrating Valentine’s Day One Click at a Time
Thursday, February 9, 2023
Blog topics:
In the course of our lives, we experience romance in a variety of different ways.
For some of us, there was a time where it began simply enough, with a folded note that we asked our best friend to pass over to someone while we were in class.
From there, it’s the relationships that begin as early as our teens and twenties. Or if we aren’t so lucky it takes a few frogs to find our prince. And, if we’re fortunate, it continues on, until we’re in the twilight of a life well-lived in the company of someone special who cared about us.
With Valentine’s Day right around the corner many people (me included) start thinking about what we can do for our loved ones to offer a token of our love that day. In fact, it’s estimated that people will spend an average of $192.80 for Valentine’s Day -- when you add up the cost of what we’ll spend, not only for our husband, wife, or significant other, but our family, friends and even our pets! What’s more, consumers ages 35 to 44 are planning to spend even more -- an average of $335.71, the most of any age demographic.
Yet, in order to get to our storybook ending, it’s important for you to know that cybercriminals and scam artists are doing everything they can to steal away your life savings and your personal information while, at the same time, breaking your heart.
Here in Indiana, hundreds of Hoosiers fall victim to the scheme every year. From 2019 to 2021, romance scam complaints, nationally, have increased by 25 percent and the victims' losses totaled $1.3 billion in the past five years.
Many victims hesitate to report it because of embarrassment. Recently, a woman in Central Indiana, shared her story in the hope that it’ll help other people avoid being the victim of a romance scam.
In a recent interview with the Indianapolis Star, Herbert Stapleton, Special Agent in Charge at the FBI’s Indianapolis office said it’s important to understand how a romance scam works and how you can protect yourself.
Additionally, there are some helpful tips to keep in mind, including:
- Be careful what you post and make public online. Scammers can use details shared on social media and dating sites to better understand and target you.
- Research the person’s photo and profile using online searches to see if the image, name, or details have been used elsewhere.
- Go slowly and ask lots of questions.
- Beware if the individual seems too perfect or quickly asks you to leave a dating service or social media site to communicate directly.
- Beware if the individual attempts to isolate you from friends and family or requests inappropriate photos or financial information that could later be used to extort you.
- Beware if the individual promises to meet in person but then always comes up with an excuse why he or she can’t. If you haven’t met the person after a few months, for whatever reason, you have good reason to be suspicious.
- Never send money to anyone you have only communicated with online or by phone.
Most importantly, trust your instincts (and not just your heart…) and if you suspect that you’ve been the victim of a romance scam, be sure to file a complaint as soon as possible with the FBI at the Internet Crime Complaint Center IC3. You can also report it to the Federal Trade Commission at ReportFraud.ftc.gov and it’s a good idea to notify the social networking site or app where you met the person.
And, hey, if it’s meant to be, you’ll be safe and secure and find the fairy tale together. Happy Valentine’s Day!
Advantages of Cyber Compliance Management on Your Business
Thursday, February 2, 2023
Blog topics:
PERSPECTIVES FROM THE FIELD
The strength of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the Indiana Executive Council on Cybersecurity (IECC). Hence the name "Perspectives From the Field Series" in which we invite experts to discuss the real and challenging issues we are facing in the field and the proposed solutions from the experts to better the lives and businesses of all Hoosiers.
In the second installment of a two-blog series, Jeremy Miller shares his expertise on the advantages of cyber compliance management and how it can help protect your business.
Most small businesses believe that cybersecurity is only important for large corporations, which are more exposed to threats since they have more resources. In fact, 60 percent of small businesses owners think it's unlikely that cyber criminals will attack them. Contrary to popular assumption, small businesses are MORE likely than huge enterprises to be the subject of cyber threats.
That is why cyber compliance training and management is essential for businesses today. Employing a variety of learning and maintenance strategies, businesses can reduce risks and the expense of a breach. Maintaining and keeping systems secure and resilient can help to avoid severe consequences including reputation damage, financial losses, and even loss of life.
Let's look more closely at why cybersecurity compliance training and management is crucial for businesses and shouldn't be disregarded today. First, here are some of the different cyber threats  that businesses owners and employees must be aware of and trained to handle.
that businesses owners and employees must be aware of and trained to handle.
- Cyber-terrorism
- Malware
- Trojans
- Botnets
- Adware
- Spyware
- Ransomware
- SQL Injection
- Social Engineering
- Phishing
- Man-in-the-Middle
- Denial of Service
- Online Scams
- Sextortion
While purchasing the most recent cybersecurity hardware and software is advised, providing employees with continuing security skill training to be aware of cyber threats like these will help assure the long-term security of your company's data. Furthermore, performing proper security assessments can show you where security gaps lie, as well as provide you with the tools to improve your security posture and keep you compliant with industry and local regulations.
Additionally, there are a wide range of benefits to having a cyber compliance management system, including:
- Saving time and resources by automating compliance-related processes, such as policy management and security assessments.
- Helping to avoid more of the cost that can come from non-compliance, such as fines and penalties, and potential lawsuits. Also, it can minimize the costs associated with incident response and recovery in case of a security breach.
- Customers, employees and vendors feeling safer knowing you are looking out for them.
- Putting in place more efficient data management policies that will help “keep the lights on”, in the event of a cyber incident or cyberattack.
- Taking solace in the fact you’ve done everything you can to protect your business and that you will be ready and resilient for any issues that may arise.
- Protecting against having to take corrective actions and incurring penalties for noncompliance.
- Mitigating risk to survive and recover from a cyber incident or cyberattack.
The other way to create a greater measure of compliance is to offer cybersecurity training to your employees. In doing so, it offers several advantages, including:
- Awareness -- Cyberattacks often involve a substantial number of human mistakes. An effective security awareness training program will provide them with more of the skills and assurance they need to spot security hazards when they are presented and show them how to escalate problems. The better informed your staff is, the better they can defend your company, and the more proactive your cybersecurity measures will be. It will also help in avoiding downtime.
- Increase Customer Confidence: According to a Ponemon survey, 31 percent of consumers reported that after a data breach, they stopped doing business with the compromised firm. These figures demonstrate how crucial it is to keep a robust security posture. Customers will have more faith in a company and be more likely to do business with them if they are aware that the company is taking cybersecurity seriously.
- Threat Reduction: A cybersecurity awareness campaign is crucial in lowering the dangers that could result in data breaches and other cyber threats. Employees will be informed of information security best practices, apps, and technologies using a cybersecurity awareness program, including social media, email, and websites. Employees that receive cybersecurity awareness training are better informed about common social engineering threats like phishing and spear phishing. By assessing their knowledge about cyberattacks and how they react to phishing emails, this tool can be used to identify individuals who may benefit from more training.
Regardless of the real consequences that can occur as a part of any sort of breach, people must be aware of recommended practices to generate a higher level of security. This will also help in avoiding a situation, in which the company takes a hit to their reputation or the fallout that can come from having to deal with some negative press.
What’s more, by proactively initiating a cybersecurity compliance program, you’ll not only help in protecting your company from hackers and cybercriminals, but it'll also provide a safer, more secure work environment. For more information about cyber compliance, please visit Lionfish Cyber Security or email me at jeremy@lionfishcybersecurity.com.
Cyber Compliance 101 – What It Is and Why It’s Needed
Wednesday, February 1, 2023
Blog topics:
 PERSPECTIVES FROM THE FIELD
PERSPECTIVES FROM THE FIELD
The strength of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the Indiana Executive Council on Cybersecurity (IECC). Hence the name "Perspectives From the Field Series" in which we invite experts to discuss the real and challenging issues we are facing in the field and the proposed solutions from the experts to better the lives and businesses of all Hoosiers.
In the first installment of a two-part blog series, Jeremy Miller provides his perspective on what is cyber compliance and how it fits in today’s digital marketplace.
What is cyber compliance?
Cyber compliance refers to the process of ensuring that an organization adheres to industry regulations, standards, and laws related to information security and data privacy. Many different types of organizations may need to comply with various cyber security regulations and standards. Some examples include:
- Healthcare organizations, which may need to comply with HIPAA regulations that protect patient health information.
- Financial institutions, which may need to comply with PCI-DSS regulations that protect credit card data.
- Retailers and e-commerce companies, which may need to comply with PCI-DSS regulations if they accept credit card payments online.
- Companies that handle personal data of European citizens, which may need to comply with the General Data Protection Regulation (GDPR).
- Companies that operate in certain industries, such as defense or energy, which may be subject to regulations specific to their sector and industry standards such as ISO 27001, NIST or CMMC.
It's important to note that compliance is not only limited to large companies, small and medium-sized businesses may also be required to comply with the laws and regulations of their country or industry.
Why Should Cyber Compliance Be a Top Priority
It’s vital for businesses to be on top of their compliances for a variety of reasons, including:
- To protect sensitive data: Compliance with regulations and standards helps to ensure that an organization is taking the necessary steps to protect sensitive information, such as personal data and financial information. This can help to prevent data breaches, which can result in significant financial losses and damage to an organization's reputation.
- Being compliant for legal requirements: Failing to comply with regulations and standards can result in significant fines and penalties, as well as legal action. Compliance is important to avoid these risks and ensure compliance with laws and regulations.
- To maintain customer trust: Compliance with regulations and standards can demonstrate to customers and partners that an organization takes data security and privacy seriously, which can help to build trust and maintain positive relationships.
- Improving overall security posture: The process of achieving and maintaining compliance can also help to improve an organization's overall security posture. This can include identifying and addressing vulnerabilities, implementing best practices, and regularly assessing and testing security controls.
- To obtain cyber insurance: Many companies have cyber insurance that requires compliance with certain standards and regulations. Non-compliance can lead to denial of claims and can make companies more vulnerable to a cyberattack.
Overall, cyber compliance is an important aspect of protecting businesses from potential cyber threats and ensuring that they are able to operate in a secure and compliant manner. Furthermore, cyber compliance management and training can help a business to protect sensitive data, comply with legal requirements, maintain customer trust, and improve its overall security posture.
For more information about cyber compliance, please visit: www.lionfishcybersecurity.com or email me at jeremy@lionfishcybersecurity.com.
In part two of our special blog series, on Thursday, Feb. 2nd, Jeremy Miller discusses the advantages of cyber compliance management and why it’s important to your business.
Data Privacy: Be Sure to Add It to Your “To Do” List
Wednesday, January 25, 2023
Blog topics:
If you have ever met me, you would quickly know that I LOVE “To Do” Lists. But when it comes to making out a “to do” list, if you’re like me, there’s always that ONE thing you forget about, right?
And just about the time you walk through the door at home, or you’ve left the office for the day, you suddenly remember what it is you forgot to do, and in that moment, it drives you just a little crazy. We’ve all been there. Of course, most of the time, it’s easy to head back to the grocery store for that gallon of milk or open your laptop to finish sending that email but how about protecting your personal information? That’s one item that you could say is and should be on our “to do” list every day.
This week is National Data Privacy Week and it’s fair to say that being concerned about our personal data is certainly something that’s on our minds these days. According to the Pew Research Center, 79 percent of U.S. adults report being concerned about the way their data is being used by companies. Add to that, another Pew Research Center study found that 93 percent of Americans considered it important to be able to control who could access their personal data.
The fact is, our ability to keep tabs on our data – everything from our social security number and date of birth down to the number of steps we’ve taken today, as recorded on our Apple watch or Fitbit device – is a balancing act. It’s all about what we need to do as a part of our everyday life while, at the same time, trying to take advantage of the convenience that today’s technology affords us. In other words, being able to do everything in a click or two without getting hacked or being the victim of a phishing attack.
Fortunately, there are a lot of great (and FREE) resources to help you.
For starters, if you want to learn more about what is data privacy, the National Cybersecurity Alliance (NCA) offers a great article that’ll help you understand more about it.
According to the NCA, there are also several key tips to keep in mind when it comes to protecting yourself, including:
- Knowing the tradeoff between privacy and convenience – Your data is tremendously valuable and it’s a good idea to make informed decisions when sharing it with a business or service.
- Adjusting (and managing) your privacy settings to fit your comfort level (err on the side of sharing less data, not more).
- Protecting your data – Turn on multi-factor authentication whenever it’s permitted and learn how to identify phishing messages.
- Creating complex passwords for each account or device and storing them securely in a password manager.
Here in the Hoosier State, we invite you to visit our Indiana Cyber Hub website for all kinds of cybersecurity resources, best practices, tips and even toolkits that you can download for FREE to help you stay safe whenever you’re online and protect your personal information.
If you’re a business owner, a non-profit organization or work in local government, there’s even a PII (Personal Identifying Information) guidebook (written by privacy experts) that you can use to help better protect yourself.
For more information, visit www.in.gov/cybersecurity.
Working Remotely: Safe at Work, Safe at Home
Wednesday, January 11, 2023
Blog topics:
 You might not have noticed it on the calendar, but this week is National Home Office Safety and Security Week.
You might not have noticed it on the calendar, but this week is National Home Office Safety and Security Week.
And while I’m not sure there’s a Hallmark card for the occasion, working from home is something we can celebrate when it comes to maintaining our productivity, while at the same time, making sure we’re getting our work done, safely and securely.
With more people than ever working remotely, the party is just getting started, given the fact that many businesses and organizations haven’t completely made up their mind as to where everyone is going to work in the long term. As all of that gets sorted out, there are 10 steps you can take to set up and maintain a cybersecurity-safe home office, including:
- Only use company-issued devices
- Use a VPN to reduce hacking risks
- Work within company-approved software and tools
- Keep software updated
- Avoid using public Wi-Fi
- Don’t open suspicious emails
- Change your password regularly
- Set up boundaries for virtual meetings
- Be cautious when sharing your screen
- Practice good digital hygiene
Protecting your home office environment is important, too, for the fact that the frequency and sophistication of cyberattacks and cyber incidents continues to rise. According to recent data from the Cybersecurity Infrastructure and Security Agency (CISA), a ransomware attack occurs every 11 seconds. Unfortunately, a lot of these incidents are the result of someone clicking on an unsecure link. Add to that, 95 percent of cybersecurity breaches are due to human error and compromised passwords are responsible for eight out of 10 security breaches.
Following these suggestions will help you stay organized with your work, but it’ll also help in managing your digital space at home.
As a side note, you might be interested to know that the whole idea (and potential benefits) of working from home was first created – more than 50 years ago – by a NASA engineer, Jack Nilles, who coined the term “telecommuting” from a publication he wrote entitled Telecommunications Transportation Tradeoff. An accomplished physicist, Nilles switched from being a rocket scientist to serving as a research director at the University of Southern California, a position that was created for him so he could follow his theory that remote working would be good for business and even better for the environment.
His nine-month study showed that worker productivity went up, health care costs went down, and infrastructure costs dropped. Also, the company who commissioned the study was going to save as much as $5 million. So, what happened? The company chose not to do it.
Maybe they were waiting to see what was going to happen with the World Wide Web.
Mentoring Is for All Ages
Wednesday, January 4, 2023
Blog topics:
While it could be said that the three things we look forward to most when it comes to the start of a New Year is optimism, hope, and an affordable gym membership, there is another reason to celebrate in 2023.
And that’s the influence or advice we’ve received from someone we consider a mentor. Of course, it’s the perfect time, as January is National Mentoring Month.
From my own experience, the guidance I’ve received – over the course of my life – from people who’ve influenced me, both at work and in my everyday life, is immeasurable. Mind you, some of what I heard along the way, at times, might not have been easy to take or something (in that moment) I might've found to be a challenge. But to be sure, what I gained from it all is something I value, to this day.
What’s more, it’s enabled me to use those experiences and serve as a mentor to others. That’s important, but not for the reasons you might think. A survey by Olivet Nazarene University, published in in a 2019 article in Forbes, reported that 76 percent of people think mentors are important, but it also revealed that only 37 percent of those surveyed said they have one. It also found that just 14 percent of mentor relationships started by asking someone to be their mentor. Sixty-one percent of those relationships developed naturally.
Mentoring.org highlights the case not only as to why someone should become a mentor, but also provides important data about the realities involving the impact of someone who grows up without a mentor. It also illustrates what happens with young adults who DO grow up with a mentor. You can even sign up to become a mentor.
 All of this is important for two reasons. Cybersecurity is one of the fastest-growing professions in the world and the opportunities, as it relates to hiring a diverse workforce, are truly unique. Because of that, there are some 750,000 available job positions in cyber in the U.S.; a figure that includes roughly 20,000 openings here in Indiana.
All of this is important for two reasons. Cybersecurity is one of the fastest-growing professions in the world and the opportunities, as it relates to hiring a diverse workforce, are truly unique. Because of that, there are some 750,000 available job positions in cyber in the U.S.; a figure that includes roughly 20,000 openings here in Indiana.
Secondly, the times have changed, and mentoring is not an activity that’s exclusive to someone who’s older providing their influence on a younger person, who is either in an entry-level position or, perhaps, is a high school or college student. The script has changed and there are many people – working in cybersecurity and other related fields – who’ve gained the requisite level of knowledge and experience (at a much younger age) and they’re able to pass along their experience to someone who’s older. That’s a trend that’s emerged, as people are deciding, as never before, to change careers, or they’ve decided to do something that requires additional training to gain the experience they need to pursue a job in cybersecurity in the long term.
In celebration of all mentors and all of us whose lives they’ve influenced, be sure, too, to visit our Indiana Cyber Hub website for more information about cyber careers, including job boards, training resources, and more!
Cybersecurity for Hoosiers: We're All In This Together
Wednesday, December 28, 2022
Blog topics:
 By Indiana Office of Technology Outreach Team
By Indiana Office of Technology Outreach Team
When you travel the state of Indiana for a little over a year talking about cybersecurity with local governments, it is difficult to encapsulate the experience in short order.
The range of perspectives, the complexities of the challenges, and the dedication of the people you meet offer subjects that could be discussed at length. More narrowly focused topics, such as ransomware and business email compromise (BEC) threats, as well as access to IT and cybersecurity expertise, together with the significant penetration of cybersecurity insurance, cultural inhibitors to governance and ownership, and many others would illustrate the varied strategies that have evolved to protect local government data and services. It was an educational and rewarding experience.
 Before diving headlong into our experience, we must say that Indiana is a beautiful state and Hoosiers are the most welcoming individuals. Visiting with state and local government representatives from 92 counties required some serious time and mileage; thankfully, the scenery and hospitality made the long drives enjoyable.
Before diving headlong into our experience, we must say that Indiana is a beautiful state and Hoosiers are the most welcoming individuals. Visiting with state and local government representatives from 92 counties required some serious time and mileage; thankfully, the scenery and hospitality made the long drives enjoyable.
Local government officials are aware of the threats they face and seem to take the challenge seriously. We found a collective theme of constraints: funding, tools, expertise, and, at times, executive cohesiveness. Still, the capabilities in place with most local government operations are beyond what many assume, and they are checking many of the important boxes. At the same time, in a day and age when even the best run organizations are breached, much work remains to be done at the local level.
We pursued our listening tour with three primary objectives. First, we wanted to better understand the cybersecurity environment statewide. Second, we needed to build and strengthen relationships and lay the foundation for an integrated cybersecurity community. Third, we sought to gather information that would help us craft a “whole of state” cybersecurity plan.
We found the environments to be as diverse as expected, consistent with some general assumptions, and different with each organization. We put a good foot forward toward building the trust imperative for an integrated cybersecurity community. We followed up on every question, and, more importantly, we responded with action to the needs expressed. Through the year, the Indiana Office of Technology (IOT) added to the portfolio of services the state could offer to offset locals’ costs and constraints (e.g. – secure email, cybersecurity training).
Finally, we’ve incorporated what we learned into our draft of the State’s whole of state cybersecurity plan for the federal State and Local Cybersecurity Grant Program (SLCGP). Getting each local government to where they want and need to be, will be a long process, in which we hope the SLCGP funds can assist. Our traveling efforts were a solid step to that end. Success is difficult to measure for this particular effort; however, openness to our message by the local governments, executive support for the necessary resources, and empathetic team members eager to help resulted in the request of a 2023 Listening Tour. We expect this coming year to be even more productive in terms of advancing the cybersecurity capabilities of local governments, and we look forward to enhancing our relationships with local officials and their IT teams – the real protectors of Hoosiers’ data.
Rolling the Dice for Your Cybersecurity
Wednesday, December 7, 2022
Blog topics:
You cup the dice into your hands, shake them around (perhaps wishing them good luck), and finally roll them onto the board. Pandemonium breaks out! The dice has decided the fate of every player on the board. Whether it be Dungeons and Dragons, Yahtzee, or Monopoly, everyone is sure to have a good time when playing games with dice.
Recently, these games have been moving online and people are able to play dice games with people all over the world. However, having these games online exposes dice enthusiasts to cybercriminals looking to take their private information.
In just this past year, there were major data breaches against Roblox, Neopets, and Bandai, with Neopets exposing the data of 69 million players. There was also a data breach in 2019 where more than 200 million online gamers had their data stolen. Is there anything online dice game enthusiasts can do to protect themselves? Thankfully there are ways to mitigate the effects of data breaches on you!
In celebration this week of National Dice Day, here are some online gaming tips from the National Cybersecurity Alliance that will help you stay safe and protect your personal information, allowing you to focus on just having fun.
- Do Your Research – Mobile gaming makes up approximately 45 percent of the global games market. But just because a game is available on a trusted app store, it doesn’t mean it is a safe app to download. Before downloading any new gaming app on your device, make sure it’s a legitimate app. Check out the reviews and look it up online before downloading it.
- Think Before You Click – Cybercriminals will often try to entice gamers into clicking links or downloading malicious files by offering cheat codes, hacks, or other ways for you to gain an advantage over competitors; this is especially true if it comes from a stranger or it’s something you weren’t expecting. If the offer seems too good to be true, chances are it is.
- Protect Your Privacy – As part of your gaming profiles, the more personal information you post, the easier it may be to steal your identity or access your data. Be cautious and if a stranger asks you to share this information, say “no”. The same is true if they ask you to share a photo or turn on your webcam.
- Avoid using geo-tagging features which can reveal your exact location. A better option is to disable this function before you start playing.
- Playing with people you don’t know or aren’t a part of your friend group? Use a safe game name, such as Superstar55 or Catsby90. Don’t use your first or last name in your usernames and use an avatar instead of an actual photo.
It’s also a good idea, as with a lot of things you’ll want to do whenever you’re online, is to:
- Always use a secure wi-fi connection.
- Create long and strong passwords (at least 12 characters long) and if you’re a real gamer, who enjoys playing on multiple gaming platforms, consider using a password manager.
- Use two-factor or multi-factor authentication on all your gaming devices.
- Secure your payment data
- Make sure all the internet-connected devices you’re using to access online games on – including personal computers, smartphones, and tablets -- are updated with the latest security software. Setting up automatic notifications are always good and if you’re playing an app-based game on a device, make sure it is updated regularly.
Of course, as adults, anything that involves a game that can’t be played at the kitchen table or involves handing out “play money”, it’s a good bet you’re going to ask questions, right? One way to learn what it’s all about is to have your kids teach you how to play whatever games they’re playing. It’s a great way to spend some time together and, who knows, you might actually win a game or two (but, if you’re like me, probably not).
Online gaming shouldn’t feel like you’re rolling the dice with your cybersecurity, waiting to see whether or not your private information will be leaked online by hackers. By following these tips, your dice rolls for increased privacy are sure to be natural 20s, just like in Dungeons and Dragons!
Safe Shopping is on Everyone’s Holiday Wish List
Wednesday, November 30, 2022
Blog topics:
One of the realities of the holiday shopping season (besides the fact that it feels like some retailers started celebrating “Black Friday” back in September) is that cybercriminals are always working on a new scam so they can go shopping with your money.
That’s a LOT of cash when you consider:
- Just last week, according to Adobe Analytics, U.S. Black Friday online sales hit a record $9.12 billion. Add to that another $9.55 billion in weekend sales, and Cyber Monday took the top spot as the busiest of all shopping days, with sales coming in at $11.3 billion. Throw in the fact, too, that fully 48 percent of these sales were completed using our smartphones. In making those registers ring, 196.7 million people shopped in stores and online between Thanksgiving and Cyber Monday.
As you look back over your receipts, it’s important to keep in mind, too, how much of what we spend is lost. According to the Internet Crime Complaint Center’s (IC3) 2021 report, non-payment or non-delivery scams cost people more than $337 million. Credit card fraud accounted for another $173 million in losses. In a non-delivery scam, a buyer pays for something they find online, but those items are never received. Conversely, a non-payment scam involves goods or services being shipped, but the seller is never paid.
Fortunately, there’s a lot of free resources, with helpful cybersecurity tips – from sources you can trust – that are designed to make your online shopping experience easy, but more importantly, safe, and secure, including:
- Learning more about cyber from why it’s important to take precautions and how attackers go after online shoppers to ways you can protect yourself is the mission of the Cybersecurity and Infrastructure Security Agency and their website is filled with all kinds of great information, tips and best practices.
- Avoiding “fly-by-night” websites and resisting the temptations of “free” offers are among the tips Regions Bank offers as part of its advice on how to handle Five Common Online Shopping Scams.
- PRO TIP: No online retailer needs your Social Security Number or your Date of Birth to make a purchase. Making sure that you don’t overshare your personal information and always looking for the “lock” when visiting a website that you intend to use a credit or debit card for making a purchase are at the top of PC Mag’s 14 Tips for Safe Online Shopping.
Here in Indiana, cybersecurity is a top priority and there’s always lots of FREE information for Hoosiers of all ages, including cyber tips for individuals and families, as well as businesses, local government, and schools on our Indiana Cyber Hub website and be sure to follow us on LinkedIn, Twitter and Facebook.
Happy Holidays!
Putting a "C" in STEM
Wednesday, November 23, 2022
Blog topics:
As the Cybersecurity Program Director of the State of Indiana, I am encouraged that a career in cybersecurity is among the fastest-growing categories in technology – not only here in Indiana, but across the country and around the world.
Over the last 10 years, Forbes notes that cybersecurity jobs worldwide grew 350 percent (2013-2021). In the United States, there are approximately 750,000 open cybersecurity jobs, but only enough qualified workers to fill 400,000 of them.
By any measure, that’s quite a gap to try and fill. That being said, as someone who’s worked in cybersecurity for several years now, but whose background and experience is in communications (not technical), it’s my belief that the cybersecurity field is set up, you might say, for the kind of progress we’re seeing with STEM/STEAM careers that’s occurred within the past 20-30 years.
With this month being National Career Development Month, here are some reasons cybersecurity is emerging as a career to consider, including:
- People are deciding – for a variety of reasons – to change jobs or switch careers at a rate we haven’t seen since the 1970s and the path for making that kind of transition is as wide-open as it’s ever been for people ranging in age from their late teens to their 50s or 60s (and older…).
- In terms of education, nearly a dozen colleges and universities in the Hoosier State offer cybersecurity degree programs as part of their class offerings. Opportunities are starting to grow among K-12 schools and competitions, such as CyberStart America, are helping to introduce cyber as a career to high school students to consider pursuing once they graduate.
- At the same time, a growing number of organizations – educational, vocational, and military, as well others in both the private and public sectors – are offering programs with real-world training (that doesn’t require a degree) and on-the-job experience that can lead to someone earning an entry-level salary in the range of $40,000-$50,000 in as little as six months.
- Because of the urgency that exists to fill these positions, the opportunity for creating a diverse and inclusive workforce is greater than ever. Additionally, the opportunities for finding a meaningful career includes people who’ve been diagnosed as neurodiverse; creating a career path for someone whose performance is not defined by the fact they are managing a condition, such as autism, attention deficit/hyperactivity disorder (ADHD) or dyslexia, as part of their everyday life.
Whether you’re a student, a parent, or an employer, you are invited to visit the cyber careers page on our Indiana Cyber Hub website. There, you’ll find links to all kinds of FREE resources, covering everything from job boards to educational information that’s designed to help you find schools and/or organizations that are offering degreed programs and where to go to find a wide range of training.
Who knows, maybe as the world of cybersecurity continues to grow, we can find a way to celebrate cyber as part of STEM Day and that we’ll not only keep adding – and filling – job positions in cyberspace, but we’ll find ways to add cyber as an option in more and more classrooms and communities across Indiana.
State of Indiana's Cybersecurity Efforts Help Local Government
Friday, October 28, 2022
Blog topics:
October is Cybersecurity Awareness Month and this year’s theme is “See Yourself in Cyber” and demonstrates that while cybersecurity may seem like a complex subject, ultimately, it’s really all about people.
The celebration comes as Indiana’s ascension in cybersecurity collaboration – as a top-tier state nationally – is continuing to rise at a rapid, yet steady pace; progress driven by the unprecedented release of a second, three-year statewide strategic plan and the success that’s being achieved with two unique programs focused on partnering with local government and municipalities while providing a greater level of training and resources for the benefit of all Hoosiers.
Local Government Focus Features Community Conversation Tour, Cyber Ready Pilot Program
As part of the state’s ongoing commitment to supporting local government, the Indiana Office of Technology (IOT), led by Tracy Barnes, Chief Information Officer for the State of Indiana, is continuing with its 92-county community conversation tour. At each stop, IOT representatives have met with county, city, and town officials to discuss various information security topics and the free and low-cost services available to local governments from IOT. To learn more, visit: https://on.in.gov/IOTlocal.
A second local government initiative is the Cyber Ready Communities (CRC) pilot program. As the State of Indiana’s Cybersecurity Program Director, it is my pleasure to visit and work closely with local government leaders in four Hoosier communities – Jasper, Ind., and Dubois County; Nashville, Ind., and Brown County; Kokomo, Ind., and Howard County; Carmel, Ind., and Hamilton County.
The CRC program is centered on achieving two goals. Primarily, the purpose is to work closely with the communities to be cyber ready at every local government department level by changing the cybersecurity culture and connecting those communities to additional state, federal, and private partners, resources, and services. The second goal is to help inform the IECC (Indiana Executive Council on Cybersecurity) and state leaders as they continue to develop additional programs to help in partnering with local governments.
Emergency Manager Cybersecurity Toolkit
The centerpiece of all things cyber in the Hoosier state is the Indiana Cybersecurity Hub website. Featured among the many resources, best practices and tips that are available for free on the website, there is a great deal of “hands on” information, designed to provide local governments for being prepared, including the Emergency Manager Cybersecurity Toolkit; a free, downloadable “playbook” designed to help take out some of the complexities related to cyber and provide an invaluable resource with the tools to help local governments prepare for an cyber incident.
IECC Strategic Plan
Within the past year, the IECC presented to Indiana Governor Eric Holcomb, the 2021 Indiana Cybersecurity Strategic Plan – highlighting the cyber policies and initiatives that the Council are, now, actively working on and focused on completing in the years ahead. As a part of that work, the Council also completed the State of Cyber Report – 2017-2021– outlining all the cybersecurity policies and initiatives that have been completed since 2017 in Indiana by the Council, as well as throughout the state by colleges and universities and small businesses. The Council completed nearly 80 percent of the deliverables and objectives as part of its “first of its kind” 2018 strategic plan.
For additional information regarding the latest cybersecurity news and trends, visit the Indiana Cybersecurity Hub website and follow us on LinkedIn, Twitter and Facebook.
Defend Against Cybersecurity Threats to Your K-12 School with Four Simple Action Steps
Monday, October 24, 2022
Blog topics:
 Cyberattacks and online threats are an increasingly significant and widespread problem for K-12 schools and districts. A growing dependence on technology for learning, the presence of sensitive student data, and increasingly complex and deceptive cyber criminals have made the K-12 community particularly vulnerable over the past several years. Impacts from such attacks can affect a school’s financial security, educational obligations, and ability to provide a safe, secure environment for students and staff.
Cyberattacks and online threats are an increasingly significant and widespread problem for K-12 schools and districts. A growing dependence on technology for learning, the presence of sensitive student data, and increasingly complex and deceptive cyber criminals have made the K-12 community particularly vulnerable over the past several years. Impacts from such attacks can affect a school’s financial security, educational obligations, and ability to provide a safe, secure environment for students and staff.
Cybersecurity Awareness Month, recognized each October by the Cybersecurity and Infrastructure Security Agency, the National Cybersecurity Alliance, and other organizations throughout the country, provides an important opportunity for the K-12 community to become more educated, empowered, and equipped to take action against cyber threats. This year’s campaign theme – “See Yourself in Cyber” – illustrates that while cybersecurity may seem like a complex issue, everyone can play a role in staying safe online.
For students, teachers, and staff, taking action can mean enabling basic cyber hygiene practices. School communities can get started with these four simple steps:
- Enable Multi-Factor Authentication: Multi-factor authentication (MFA) is a layered approach to securing online accounts that requires users to provide two or more authenticators to verify their identity. Enabling MFA can make users significantly less likely to get hacked.
- Use Strong Passwords: Passwords are the most common means of authentication. Create passwords that are long, unique, and randomly generated, and use a password manager to generate and store passwords across multiple accounts.
- Recognize and Report Phishing: Phishing attacks use email or malicious websites to solicit personal information by posing as a trustworthy organization. Reduce the risk of phishing attempts by ‘thinking before you click,’ enabling strong spam filters, and training staff to recognize and report suspicious activity.
- Update Your Software: Outdated software can contain vulnerabilities that can be exploited by threat actors. Install updates on school devices as soon as possible and/or enable automatic updates to protect your systems.
Learn more about these action steps with this cybersecurity infographic from SchoolSafety.gov. This one-page overview can be printed and shared to help promote cybersecurity best practices within your school, and to encourage all members of the K-12 community to ‘see themselves in cyber.’
Visit SchoolSafety.gov to access additional cybersecurity resources and guidance and follow @SchoolSafetyGov on Twitter for other timely school safety updates.
SchoolSafety.gov Disclaimer
The U.S. Department of Homeland Security (DHS), U.S. Department of Education (ED), U.S. Department of Justice (DOJ), and U.S. Department of Health and Human Services (HHS) do not endorse any individual, enterprise, product, or service. DHS, ED, DOJ, and HHS do not mandate or prescribe practices, models, or other activities described in this communication. DHS, ED, DOJ, and HHS do not control or guarantee the accuracy, relevance, timeliness, or completeness of any information outside of those respective Departments, and the opinions expressed in any of these materials do not necessarily reflect the positions or policies of DHS, ED, DOJ, and HHS.
See Yourself In Cyber, Protect One Another
Wednesday, October 19, 2022
Blog topics:
 By Joel Thacker
By Joel Thacker
October is Cybersecurity Awareness Month, and the cyber risks to our way of life have never been more serious.
The theme this year is “See Yourself in Cyber.” Those who stay diligent to avoid scams understand how important individual responsibility is in this fight. Nearly 90 percent of cyberattacks are due to human error, that one person who mistakenly opens an attachment at work, putting an entire organization at risk. It happens every day, but it does not have to be that way.
Corporate data breaches reached an all-time high in 2021 as more people worked remotely and normal safeguards from workstations went by the wayside. In the U.S., the average breach cost companies more than $9 million, with the most expensive occurring in health care. Again, human error led to multimillion-dollar losses.
With more employees back in the office, training has been amplified, and we are hearing more conversations about how we can protect ourselves. The conflict in Russia and Ukraine has presented new and daunting challenges from the cyber world, and players such as China, North Korea and Iran continue to exploit opportunities.
Just this month, an Indiana utility company was hit with a ransomware attack. This is a local problem with local solutions. This is our problem.
The Indiana Office of Technology offers any municipal body a multitude of free or low-cost services to protect government entities from cyberattacks. One key advantage IOT offers for free is online training to all local government employees through its KnowBe4 platform. A full offering of state services can be found on the IOT Local Government Services website.
Additionally, the Indiana Department of Homeland Security soon will administer Indiana’s portion of the $1 billion allocated across four years for cybersecurity as part of the Infrastructure and Investment Jobs Act. Details are still coming together on how many dollars will be coming to state, local and tribal governments in Indiana, but 80 percent of the allocation is earmarked for local government, including rural areas.
The State and Local Cybersecurity Grant Program was announced on Sept. 16. It is not yet open for applications, but information about how to apply will be provided in the coming weeks.
Momentum continues to increase for the U.S. to protect itself, its infrastructure and its citizens from the new frontier of online crime. The government is doing its share to better position each state according to its needs.
Each one of us must take ownership of cyberthreats and do our part to protect one another.
Money, Money, Money...And Fraud
Wednesday, October 12, 2022
Blog topics:
 By Heidi Leonard and Erik Miner
By Heidi Leonard and Erik Miner
“You’ve been compromised.”
Those three simple words keep business owners awake at night. And for good reason.
The Association for Financial Professionals estimates that 71 percent of companies have received fraudulent attempts during the past year.
Ensuring the secure transfer of funds is essential for any organization. The AFP survey also identified real estate as one of the three most often-targeted industries by criminals (in addition to construction and commercial services). It also points out where business fraud is on the rise, increasing more than tenfold over a two-year period.
The factors behind this high-risk industry gives us pause and think of state and local governments, given the common factors real estate firms share with many cities, towns, and schools:
- They involve large dollar transactions.
- They have easy access to public records.
- It is easy to impersonate someone via email; and, in both industries, there is oftentimes a lack of strong authentication processes.
 The public sector houses some of the hardest working professionals we’ve had the pleasure of working with. However, it is an industry subject to potential turnover framed by heavily scrutinized budgets. It is key for staff to be armed with fraud education and cybersecurity resources such as multi-factor authentication and other fraud prevention tools.
The public sector houses some of the hardest working professionals we’ve had the pleasure of working with. However, it is an industry subject to potential turnover framed by heavily scrutinized budgets. It is key for staff to be armed with fraud education and cybersecurity resources such as multi-factor authentication and other fraud prevention tools.
When you add the current strained and volatile economy to the risk profile of many municipal governments, it could be argued that the risk of fraud schemes will only increase in 2022 due to distraction, unpredictability, and chaos. Extra vigilance is required by Hoosiers in today’s economy, and we should all task ourselves with mitigating cyber risks both at home and at work.
At Regions, we recommend that organizations implement a multi-layered approach, leveraging education and information sharing with an internal process driven by best practices, along with utilizing external resources.
- Begin by talking with your banker about the best safeguards against fraud, including products like Positive Pay and ACH Alerts. Be and stay curious.
- Carve out regular time to educate yourself and your team on current fraud strategies (they never cease to amaze us).
- Create an internal team to conduct a thorough IT/infrastructure assessment to identify any potential points of compromise. Document your process and plan – you can leverage these free resources to help you.
- Implement an anti-fraud training program and internal controls using Stop-Call-Confirm and dual approvals to be more proactive. By adding some intention and dimension to your business practices, you are bound to reduce your risk, no matter your industry, something that allows all business owners to sleep more soundly each night.
Unfortunately, fraud isn’t going away because when big money is involved bad actors want a piece of the action. Protect yourself and your organization with ongoing education, training and multi-layer protections that make access difficult for scammers.
Let's Stop & Talk About Getting Prepared
Friday, September 30, 2022
Blog topics:
As we move from September’s National Preparedness Month to October’s National Cybersecurity Awareness Month, it is important to remember how the two connect and what we can do to keep yourself and your loved ones safe and healthy.
As the Executive Director of Indiana Department of Homeland Security, the #1 piece of advice I give people when preparing for an emergency or a disaster is to have a plan. And, just as you need to make certain you go to a safe location in your house, in the event of severe weather, or you decide on a safe meeting place if there’s a fire or a flood, it’s important for you to include a cybersecurity plan that helps protect everyone, regardless of the situation.
The National Security Agency offers a list of best practices to keep your home network secure, such as updating your operating systems and safeguarding your mobile devices, as well as some helpful tips designed to help you stay whenever you’re online – including taking precautions on social media to using different devices for different activities for protecting your personal information. With National Cybersecurity Awareness Month, USDHS Cybersecurity & Infrastructure Security Agency also features four things you can do to help improve your cyber hygiene and stay better protected.
* * *
In addition to being prepared at home, our cities, and towns – across Indiana – have to be prepared for any emergency, in order to protect everyone they’re dedicated to serving, as well as making certain that the critical infrastructure systems that are a vital part of local government are maintained safely and securely.
Among the resources that are available includes the Emergency Manager Cybersecurity Toolkit. Developed by the Indiana Executive Council on Cybersecurity (IECC), is a free, downloadable resource for emergency managers that includes four key sections, including:
- A survey to assist emergency managers in planning with their partners they work with to develop emergency and continuity of operations plans;
- A cybersecurity incident response plan template; a training and exercise guide and;
- Additional resources for navigating a range of different cyber incidents and threats.
While there really is no perfect plan or guide to use when planning for an emergency, nothing more is important than protecting our families and our communities. For more information, visit the DHS website on how you can get prepared and the Indiana Cyber Hub website at: www.in.gov/cybersecurity.
Monitoring the Baby Monitor
Wednesday, September 21, 2022
Blog topics:
Every year, it feels more and more like we’re living in a science fiction world because of all the technological advances we benefit from in our day-to-day lives. This is especially true for parents to watch over their babies with smart baby monitors.
If you are anything like me, when I became a new mom I was OBSESSED with this baby who made my whole heart full. So as a new mom, I was consistently checking on my little one at night. But with the extra convenience (and peace of mind), it can come at a cost if you don’t take a few steps to protect your little one.
It might surprise you to know that baby monitors have been notoriously weak in security, and I’ll tell you how and why it’s an issue. For some context, last year, there was a critical vulnerability that was found in more than 83 million smart devices, which included baby monitors. There were even more examples of smart baby monitors with critical vulnerabilities last year and in 2018 and probably much more that went undiscovered! A common theme is that some of the monitors were rushed into market at an affordable rate, which comes at the cost of not designing in enough security measures into the product itself. Because of this, it exposes people to some issues involving their privacy (including the use of any cameras) and their home network being compromised. This just adds to the stress for new parents, who are just looking to take care of their children. That being said, here are some helpful tips you can use to protect your smart baby monitor!
Secure Your Wireless Router
Your router is the (digital) front door to your home and that includes any, if not all, of the smart devices that are connected to your network – including your baby monitor. The first thing you’ll want to be sure is to keep your router secure, beginning with a strong password (when you set it up), and to keep the router’s firmware updated, disable any remote router access, maintain strong passwords, and never leave your WiFi network open.
Create a Strong Password for Your Baby Monitor
Your password is the first line of defense for your baby monitor. Make sure they’re at least 12 characters long using a combination of uppercase and lowercase letters, numbers, and special symbols. Also, be sure to change the default password – before turning it on -- as some of these passwords are commonly known to would-be cybercriminals.
Update Firmware for Your Monitor’s Camera
As with all of your devices, it’s important for you to go through and make sure that you’re completing updates to your firmware, as it will help protect you and guard against any vulnerabilities the vendor may discover over the life of the product.
Register Your Monitor
Registering your monitor, with the manufacturer or retailer, will help you stay current with any security updates. If a security vulnerability is found after being sold, the vendor may send out a recall notice or software update.
Disable Remote Access to Your Monitor’s Camera
While it’s convenient for watching your baby through the internet, it also gives others the potential to use the camera to monitor your home and your baby as well. Removing it from the network will prevent others from easily spying on your house and protect your baby.
As we grow more technologically advanced, we become more exposed to security vulnerabilities. By following these tips, you can stay ahead of the curve in protecting your family's privacy, your baby, and your home. If you’re interested in following more tips, be sure to check out our blog here and our cyber tips here!
Indiana Students Excel as CyberStart America Competition Winners
Wednesday, September 14, 2022
Blog topics:
 From October 2021 to April 2022, hundreds of Indiana students participated in CyberStart America, an interactive, national competition to help high school students understand the many advantages that come with a career in cybersecurity.
From October 2021 to April 2022, hundreds of Indiana students participated in CyberStart America, an interactive, national competition to help high school students understand the many advantages that come with a career in cybersecurity.
The competition involves an easy-to-follow platform that allows them to learn technology security basics through a series of gamified competitions.
Indiana clinched a Top 10 spot among all states that participated in this year’s competition with more than 700 students from 84 schools across the state who participated. While 105 Hoosier players qualified to apply for National Cyber Scholarship Foundation scholarships, ultimately 51 Hoosier students ended the game with scholarships to continue their education in cybersecurity. Indiana also moved into the number 10 spot nationally in 2022 after placing 11th in last year’s competition.
Cybersecurity continues to be an in-demand skill, and the need for trained industry professionals is not slowing down for the foreseeable future, which makes the need to find these future professionals so necessary. According to the Bureau of Labor Statistics, the rate of growth for jobs in cybersecurity are expected to grow by 33 percent by 2030, much faster than the average. With so many jobs available, and the need to fill them so dire, more K-12 schools are offering lessons, classes, and degrees in cybersecurity.
This year's top-performing schools and their scholars were:
Noblesville High School (4 scholars, 1 remained anonymous)
- Ellie Hohmann, Trace Downs, Aj Einterz
Carmel High School (3 scholars)
- Oren Jensen, Alex Anderson, Irene Liang
Hamilton Southeastern High School (3 scholars)
- Sandilya Kambhampati, Aryadeep Buddha, Anish Kambhampati
The state of Indiana congratulates this year's winners and looks forward to all their future successes. For more information about CyberStart America, visit: www.cyberstartamerica.org and if you’d like, you can register and sign up to receive updates as to when the next CyberStart America intake is open for registration.
Right Tools & Teamwork: Key To Taking "Compromise" Out of Email Scams
Wednesday, September 7, 2022
Blog topics:
 PERSPECTIVES FROM THE FIELD SERIES
PERSPECTIVES FROM THE FIELD SERIES
The strength of Indiana is that we bring together a variety of perspectives from the plethora of areas that touch the field of cyber, especially through the Indiana Executive Council on Cybersecurity (IECC). Hence the name "Perspectives From the Field Series" in which we invite experts to discuss the real and challenging issues we are facing in the field and the proposed solutions from the experts to better the lives and businesses of all Hoosiers.
In the latest installment of our series, we go to Kevin Mabry – founder, president and CEO of Sentree Systems Corporation, a data security consulting firm dedicated to helping small- and medium-sized businesses – who shares his perspective about the impact cybersecurity scams – such as Business Email Compromise (BEC) – are having on organizations – of all sizes – and what companies can do to protect themselves.
Every day, when a business opens its doors, which, these days, can be defined as simply turning on its computers or its digital networks, it’s not unusual for a problem or two to come up.
And regardless of the type of business you’re in, there’s a good chance that the health and well-being of your cybersecurity is at (or very close to) the top of the list of your priorities. When it comes to the types of threats that are out there, Business Email Compromise (also known as Email Account Compromise) is rapidly emerging as one of THE most prevalent and sophisticated scams worldwide.
According to the FBI, the BEC/EAC scam – between July 2019 and December 2021, accounted for a 65 percent increase in terms of the amount of exposed losses (that includes both the amount of actual and attempted loss in US dollars). What’s more, this type of cybercrime – at a cost of more than $43 billion – has been reported in all 50 states and 177 countries, with more than 140 countries receiving fraudulent transactions.
Yet, for all of its complexity, a BEC/EAC begins with a bad actor who gains access (to a company’s email system) by making it appear as though they are the CEO, owner, or some other executive.
Recently, there was a company in the financial services industry, in which someone tried to log into the owner’s email (from overseas) during a time they were not in the office.
Fortunately, the company was alerted to the issue (by having their systems monitored externally, reviewing all of their logs and events coming in from any devices or emails) and they were able to confirm that the person was not using their email at the time. In doing so, they were able to stop the attack from occurring.
There are other ways to help protect your company and minimize the potential risks associated with a BEC/EAC that includes:
- Changing the password of the owner’s (or other executives) email address(es);
- Use their password vault to generate it and store it in the vault;
- Turn on 2FA (2 factor authentication) for all emails.
If this incident had been successful, they could have sent a request to one of the other staff members to release or send an ACH transfer payment to a false account. This type of action is very difficult and, often times, is almost impossible to reverse. The client would have simply been out of that money and on the hook for the amount. As you might expect, the company was very pleased with the action that was taken.
Therefore, it is very important to have the right security tools in place, not just more security tools. We just can’t say that “if only” they had an EDR, XDR or just an antivirus and a firewall, they would have never gotten the insight to stop this attack. Rather, it’s a better solution to have someone – or a team of someones – working together as a team for monitoring everything that’s occurring in your environment.
Changing our mindset away from “set it and forget it” when it comes to data security, is a better approach. Otherwise, there’s simply too much at stake.
Going to the Farmers Market? Don’t Let Cybercriminals Harvest Your Information
Monday, August 8, 2022
Blog topics:
There is nothing better than on a nice spring, summer, or fall day than to go to a weekend farmer’s market here in Indiana with my family. In fact, with more than 8,000 farmers markets across this country (according to the U.S. Department of Agriculture), it is no wonder that this is a popular thing to do nationally.
But as I was enjoying my local market this past week, which was extra busy since it was National Farmers Market Week, it made me realize how important it is to be sure we are educating our local farmers and small businesses as well as the customer in how to best secure our information.
Credit Card Sales
While farmers are out collecting their produce, it’s important to know that everyone’s information is protected before, during, and after the sale.
It has become quite commonplace to see or use credit card readers at farmers markets. There are many different types, but most of them are connected to the seller’s phone or tablet. This opens up the thought in some people’s minds that their information could be compromised. Generally speaking, these card readers are secure for completing your transactions, but it’s always a good idea to provide customers with a receipt, or if you’re buying an item, to select the option to have a receipt sent to you in a text or an email.
Protecting Your Business
Recently, the FBI issued an alert to the food and agriculture sector stating that ransomware actors were on the hunt to disrupt their seasons. Additionally, 43 percent of cyberattacks involve small- to medium-sized businesses. Since cybercriminals see these industries as lucrative, easy targets, it is important that farmers and small businesses take a few steps – ahead of time – to make sure everyone has a safe shopping experience.
The federal government’s Cybersecurity and Infrastructure Security Agency (CISA) offers a plethora of information on ransomware attacks and ways to protect yourself or your business. To get started, there’s four cybersecurity tips you can follow to help your farmer’s market business and ensure your customer’s information stays safe includes:
- Implementing multifactor authentication (MFA) on your accounts
- Updating software and turning on automatic updates
- Thinking before you click
- Using a password manager
Multifactor authentication
This is a security enhancement that allows users to present two forms of credentials when logging into their various accounts. These credentials can include anything from a password, smart card, or even their fingerprint or face. It fully aims to add an additional layer of security, so that it is harder for cybercriminals to access your personal information.
Software updates
Updating your software is wildly important for a variety of reasons. They help patch security flaws and protect your data. Having hackers take advantage of weaknesses found in your software is the last thing you want to worry about. Make sure that you are being proactive when it comes to updating your software.
Think before you click
Hackers often times use phishing and other methods to target users. These methods are designed to trick unsuspecting individuals into giving confidential information to them. Often times, they will take credit card numbers, Social Security numbers, passwords, etc.
Password managers
Managing your passwords can be hard sometimes, but using a password manager is a good way to keep your passwords unique, strong, and safe.
To learn more about the latest cybersecurity tips, best practices, resources and more, visit our Indiana Cyber Hub website and follow us on social media on Twitter and Facebook.
One Password to Rule Them All
Wednesday, August 3, 2022
Blog topics:
One thing we all wish for is for something to make our lives easier. To simplify things.
We’re already stressed by school, work, and taking care of our families that, at times, it can feel as though you don’t have enough energy left to worry about something like making strong and secure passwords for all our accounts.
Passwords that are strong and unguessable can be hard to remember and it’s more than a little frustrating when you forget your password. At the same time, using personal information, including our name, birthday, or other family member’s names, to create a password (and then re-using them) has made it much easier for cybercriminals to hack into your accounts.
So much so, it leads to the kind of data breaches you hear about in the news on an almost daily basis. Thankfully, there’s a better solution that’s both convenient and secure. What is it? A password manager!
We have all been told that a password should be complex and at least 12 characters in length using a combination of uppercase and lowercase letters, numbers, and special symbols (i.e. punctuation); maybe even a phrase within it. The longer it is, the more protection it provides for you to be avoid being a victim of identity theft or someone stealing your money or account information. But if you are like me, I have countless accounts online for work, kids, finances, social media, medical, and so on. So coming up with a different password for every online account I have can be daunting to say the least. So why work hard when you can work smart AND be more secure?!?
Here’s how it works: A password manager is a program that generates and stores all passwords in a safe location. You can think of the safe location as a vault. Having this vault is designed to help you manage all of the passwords you rely on and use to protect your accounts – with a single, master complex password.
If you are looking into getting yourself, or your family, a password manager, you have a lot of options to choose from. There are three types of password managers called offline, online, and stateless. The most popular and widely used password managers are online, so we’ll focus on that as an option that’s out there for you to consider.
Keep in mind, too, as with a lot of things, there are ‘free’ versions of some of the more popular password managers that you can download and use, but many of these providers also offer a wider range of services at a cost – depending on the number of accounts you need (or can afford based on your budget) and how much security is required.
Also, be sure you are using a company with a stellar reputation. The password manager I use, for example, is not only great, but also very honest with me (and it’s millions of users) when they suspected a cyber breach. (Even the best can get hacked.) But they responded fast and with integrity. That means as much to me as their secure systems.
An Added Bonus to Family Accounts! Many password managers allow for you to set it up on your kid’s devices, in which you as a parent will have access to in case you need to check in on their accounts. Moreover, many use the family accounts for aging parents as well so that if that if they get sick, you can take care of their affairs and have access to their accounts in a secure way.
As a starting point, here’s a list of some of the best password managers to consider from our good writers at CyberNews.com, including:
- LastPass
- Dashlane
- Bitwarden
- RememBear
- 1Password
- Keeper
You can also google “password managers” for more options but be sure you are researching the company before subscribing and use a strong master password.
Being secure doesn’t have to be inconvenient and frustrating. With tools like a password manager, you can simplify your life, enjoy some well-deserved peace of mind, and keep your accounts safe from cyber attackers.
More cyber tips can be found at https://www.in.gov/cybersecurity.


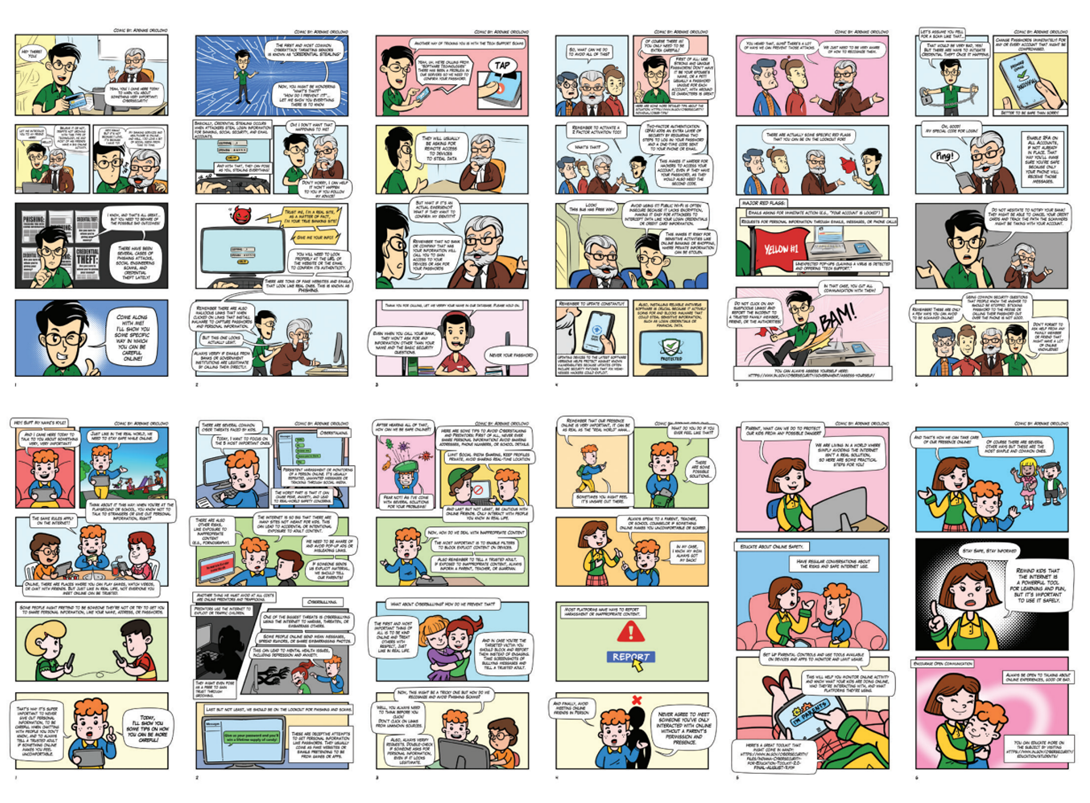
 By
By  By
By  By
By  By
By  By
By  By
By  By
By  By
By  By
By  By
By  By
By  By
By  By
By  By
By 
 By
By  By
By  By
By  By
By